There are patches or remediations for all the top vulnerabilities, but they’re still being exploited in the wild. How is that? Well, if you were the attacker, would you go through all the trouble of inventing a new zero-day exploit (just for some street cred), or instead look to leverage a known vulnerability?
A joint security advisory issued on August 3, 2023, by cybersecurity agencies from the US (CISA), the UK (NCSC), and Australia (ACSC) reveals the top 30 publicly-known, most-targeted security vulnerabilities of the last two years. Organizations worldwide were advised to prioritize and apply patches or workarounds for these vulnerabilities as soon as possible. But it’s a struggle to keep up and hackers continue to take advantage of them.
In a reality where not all vulnerabilities, or even a majority of them are ever going to get patched, the question that needs to be asked is whether they should all be patched.
Challenges Faced in Vulnerability Prioritization
Our 2024 Pentesting Survey report found that vulnerabilities are identified at a dizzying rate, with more than 60% of enterprises reporting at least 500 incidents requiring remediation weekly. This volume makes patch perfection elusive and places a heavy burden on security teams.
The sheer volume underscores the need to prioritize vulnerabilities efficiently. While vendor scoring systems assist with prioritization, it’s still challenging to prioritize the vulnerabilities that, if exploited, will have a business impact.
Understanding Vulnerability Prioritization
Vulnerability prioritization is a proactive security approach that involves identifying and addressing the vulnerabilities that pose the greatest risk to your organization, and not necessarily the vulnerabilities with the most critical CVSS score. Prioritizing vulnerabilities ensures that your limited resources are focused on mitigating the exposures that could cause the most significant harm, enhancing your overall security posture.
Strategies for Prioritizing Vulnerabilities
Risk-Based Approach
In this approach, vulnerabilities are assessed based on their potential impact and likelihood of exploitation. By focusing on the exploitability of vulnerabilities, organizations can prioritize addressing the most pressing threats, as some vulnerabilities may be benign and not justify mitigation. As part of risk assessment, consider the criticality of assets and the motivation of potential threat actors to exploit them.
Asset-Centric Prioritization
Prioritize vulnerabilities based on their proximity to critical assets. Identify key systems and data crucial to operations, such as financial systems and customer databases. Focus remediation efforts on vulnerabilities that, if exploited, could lead to significant damage to these high-value assets, whether for their confidentiality, integrity or availability to your business.
Integrating Threat Intelligence
Integrating real-time threat intelligence feeds provides insights into attack vectors and threat actor activities, allowing for adjustment of prioritized tasks based on the latest data. This enables vulnerabilities to be assessed in greater context, emerging threats are anticipated early, and high-risk vulnerabilities are identified accurately.
Vulnerability Severity Scoring
Severity scoring systems, like the Common Vulnerability Scoring System (CVSS), offer a standardized framework for evaluating vulnerability severity. Use these scores as a baseline for prioritization, supplemented with business impact and asset importance, to ensure an efficient approach to vulnerability management.
Best Practices for Vulnerability Remediation Prioritization
To ensure that vulnerability remediation is prioritized effectively, adhere to the following best practices:
Prioritize According to Business Risk
Effective vulnerability remediation prioritizes according to business risk. This means the vulnerability is not only proven to be exploitable but also provides a pathway to sensitive assets, such as PII and proprietary data. Typically, only 2-5% of vulnerabilities pose significant business risk, and addressing these real high-risk vulnerabilities can dramatically minimize exposure.
Leverage Automation and Orchestration
- Automation Tools: Using automation tools for vulnerability prioritization enhances accuracy and efficiency, enabling rapid and continuous assessment and scoring to promptly address high-risk vulnerabilities while freeing up human resources for strategic initiatives.
- Orchestration of Remediation Processes: Orchestration coordinates and manages remediation steps, streamlining workflows to ensure timely execution, minimize delays, and reduce the window of an open exposure.
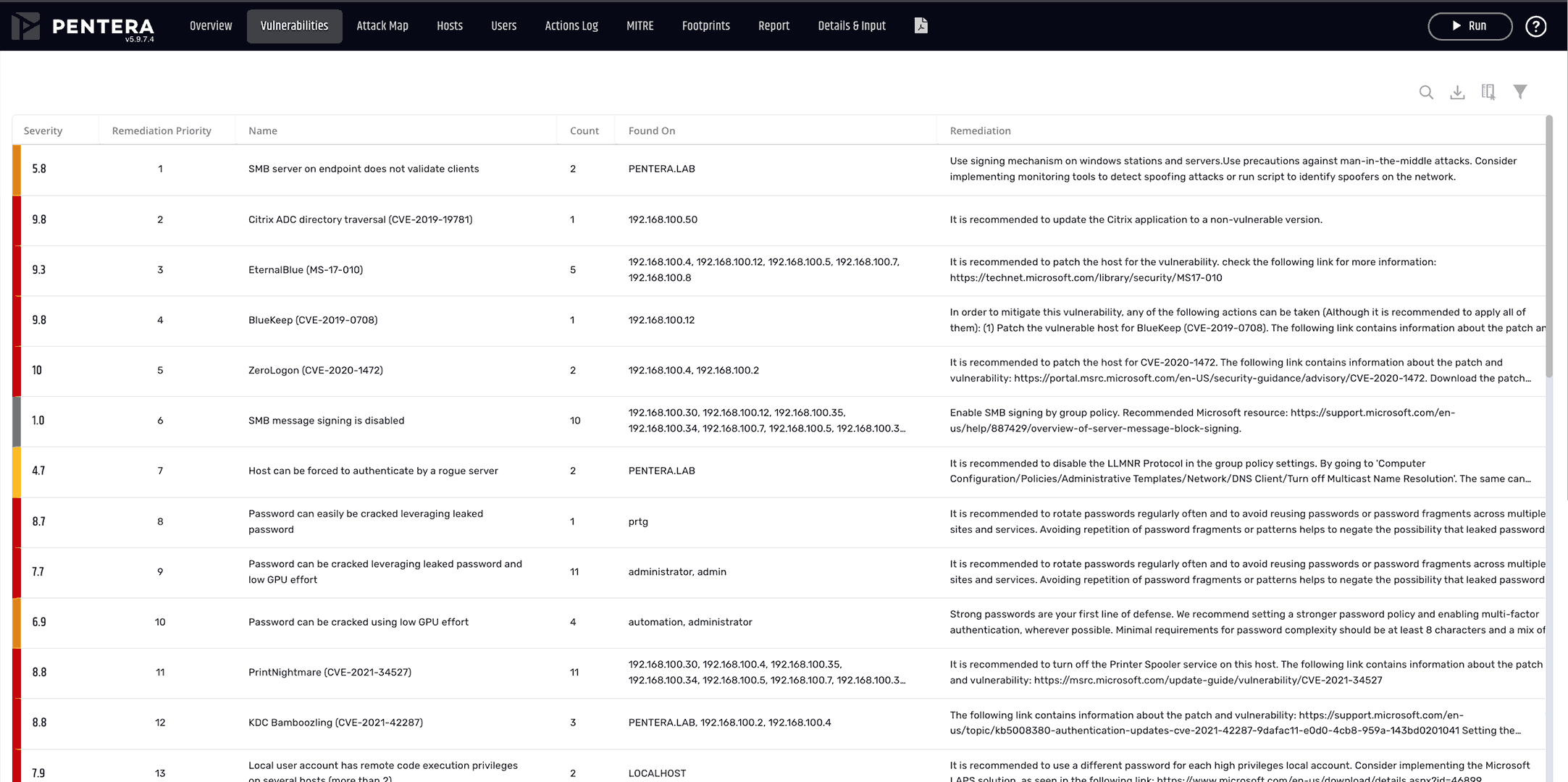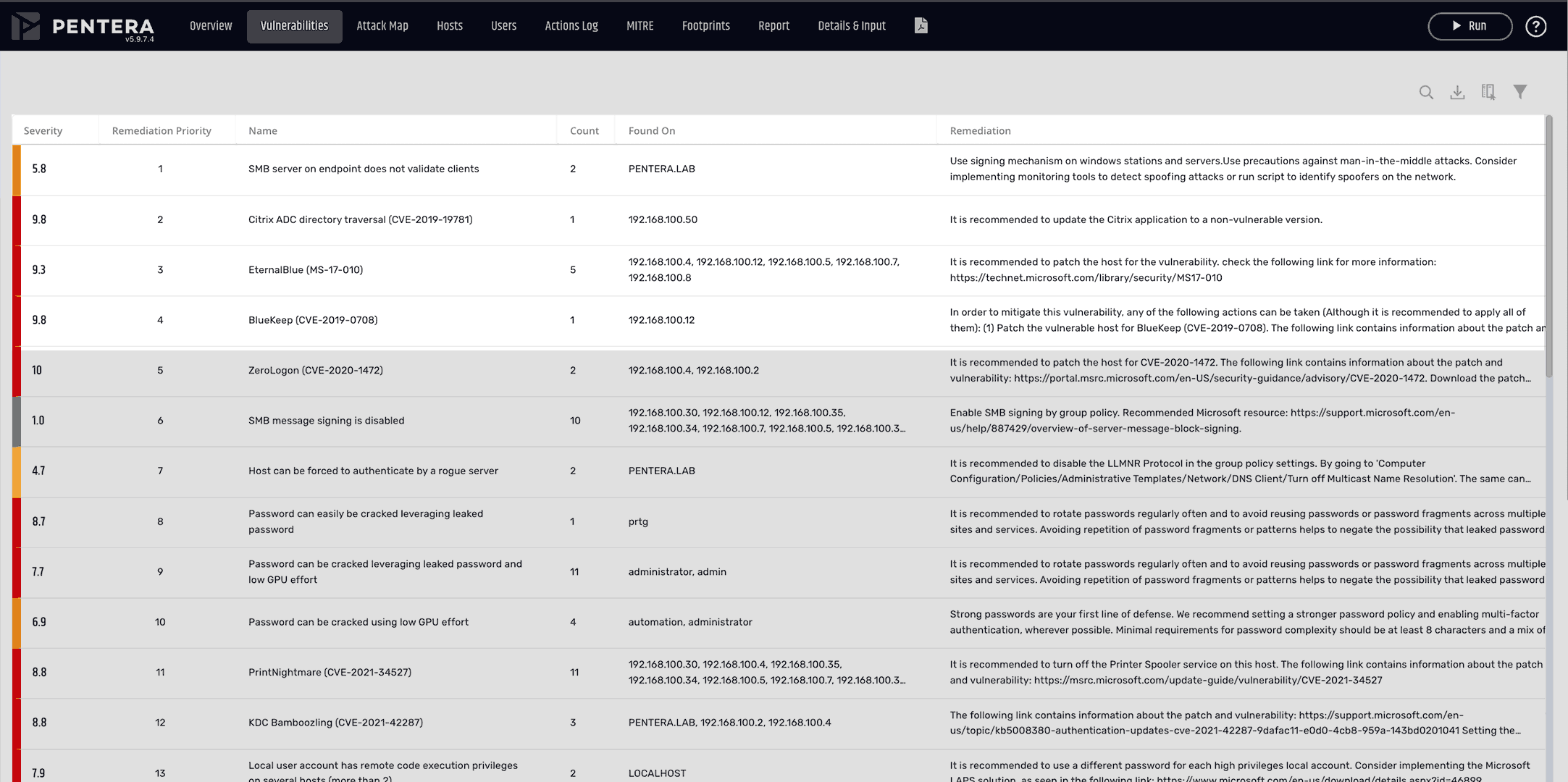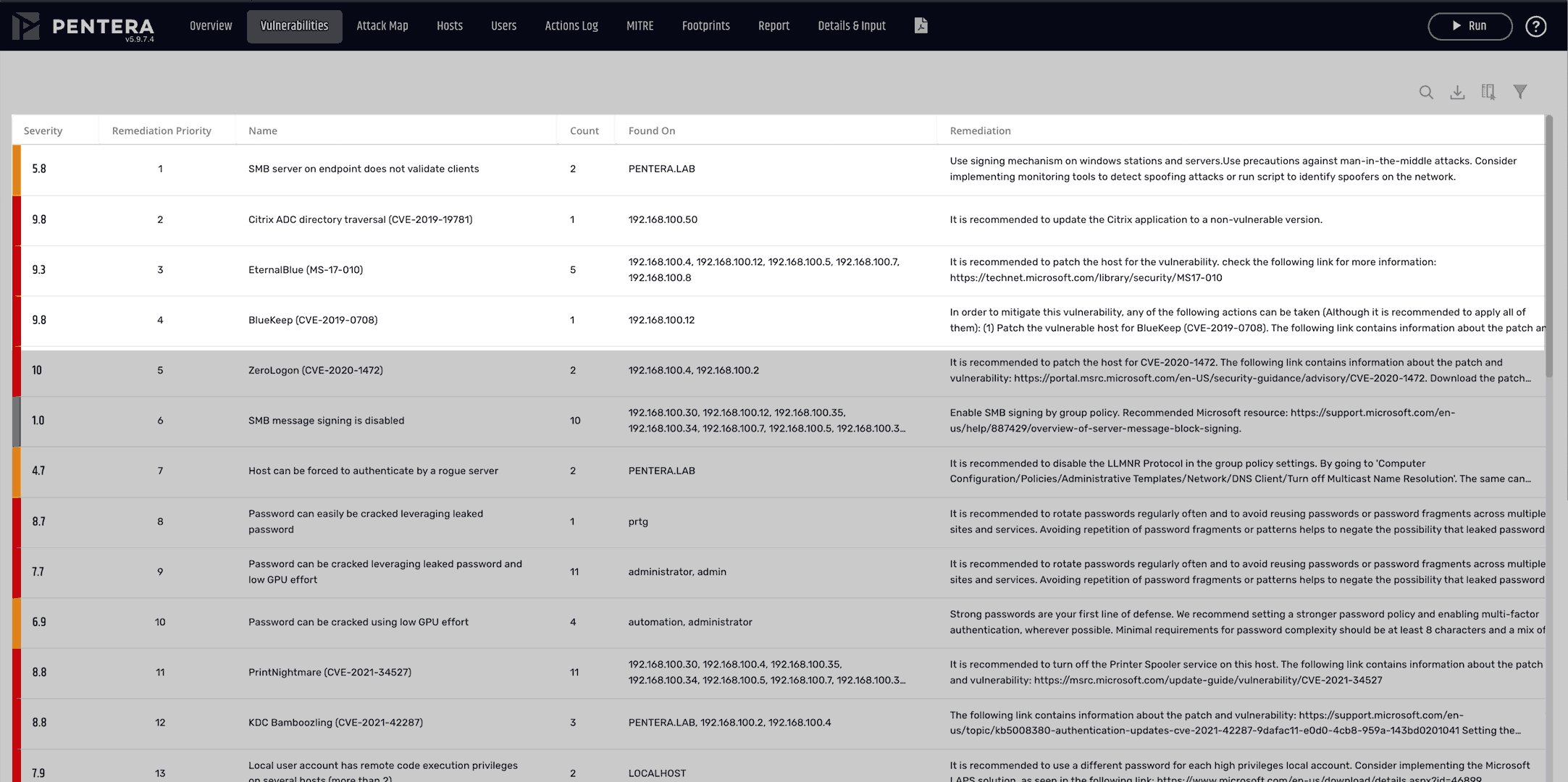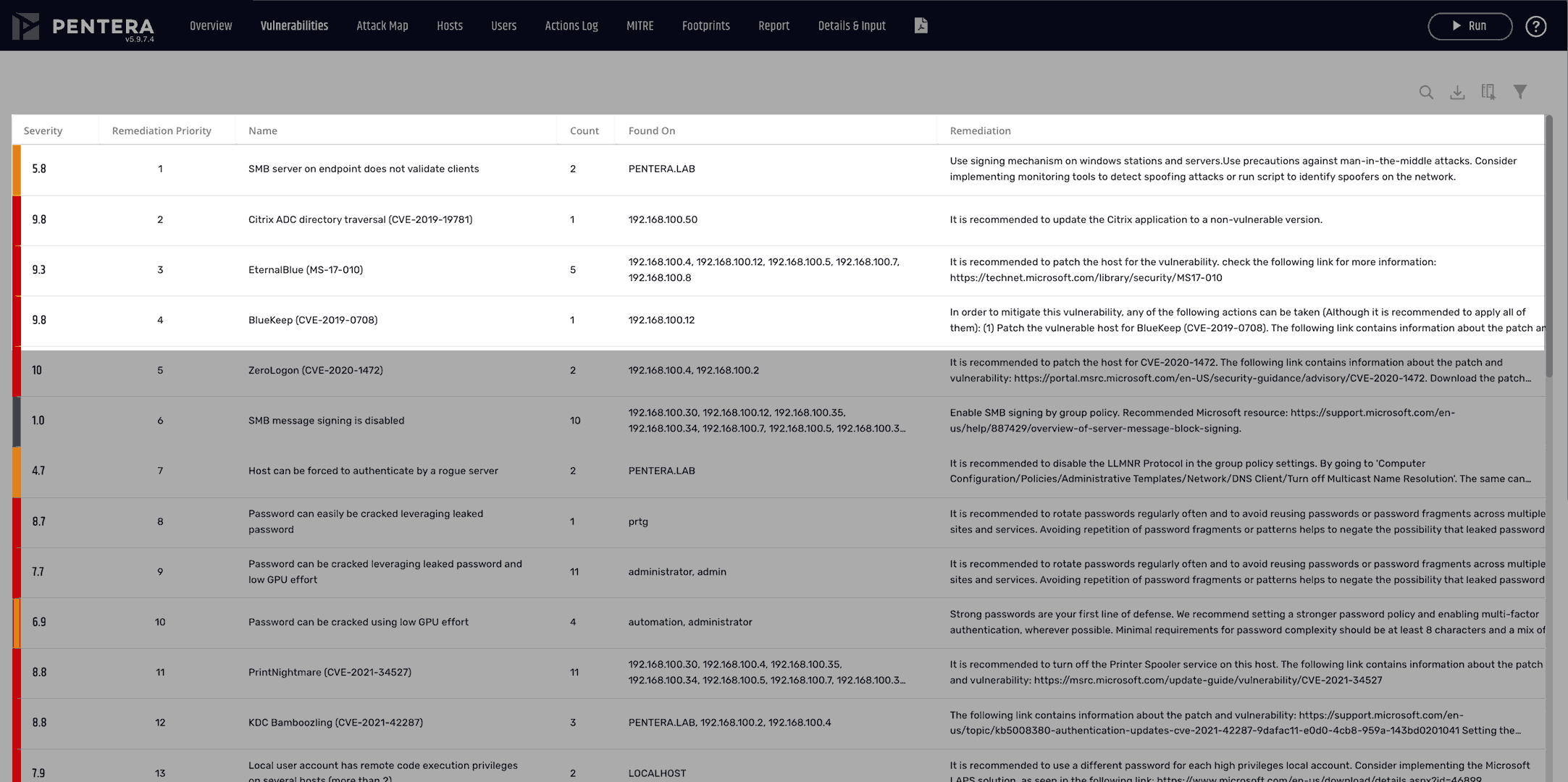
Pentera supports the prioritization of remediating vulnerabilities
Case Study: How Azul Airlines Prioritizes Vulnerabilities
Brazi’s Azul Airline which is ranked among the world’s top 50 airlines is known for its punctuality in operating around 900 flights daily to over 160 destinations. Given this large volume of daily operations and the need to protect sensitive data and systems, the airline faced the critical challenge of ensuring strong security across its extensive network.
By using Pentera’s automated security validation platform, the airline effectively prioritized and addressed its most critical vulnerabilities. This approach provided continuous, real-time insights with which to improve their security posture. The automated platform made testing easier with various configuration options and detailed reports, enabling quick decision-making and planning. As a result, the airline stayed ahead of threats and maintained its reputation for safety and punctuality.
Azul Airlines video testimonial
Effective Vulnerability Prioritization to Minimize Exposure
Minimizing exposure to cyber threats isn’t just about patching every vulnerability—it’s about using resources wisely. By focusing on the most critical vulnerabilities and business impact, you can significantly reduce your exposure and improve your security posture. This approach allows your security teams to efficiently address high-impact vulnerabilities on time, validating that new and existing security controls are effective at detecting and defending against potential threats.
With the right tools and strategies in place, vulnerability prioritization is transformed to strategically reduce risk. You can test your entire attack surface against real-world exploits, mimicking attackers to reveal your readiness against the latest threats.
Learn how to prioritize vulnerabilities to significantly reduce your risk or download our Buyer’s Guide to search for a solution that best meets your organization’s needs.