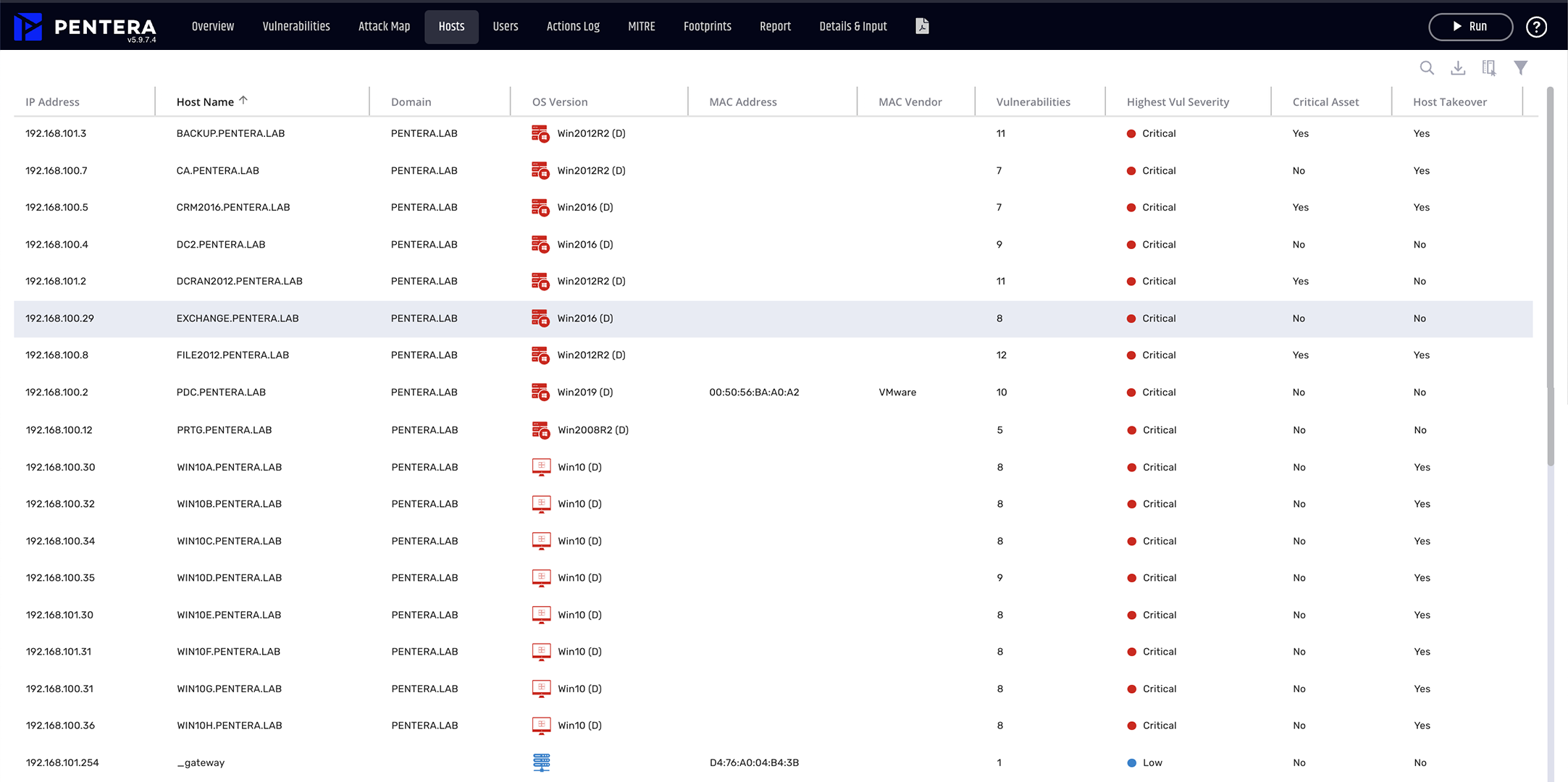
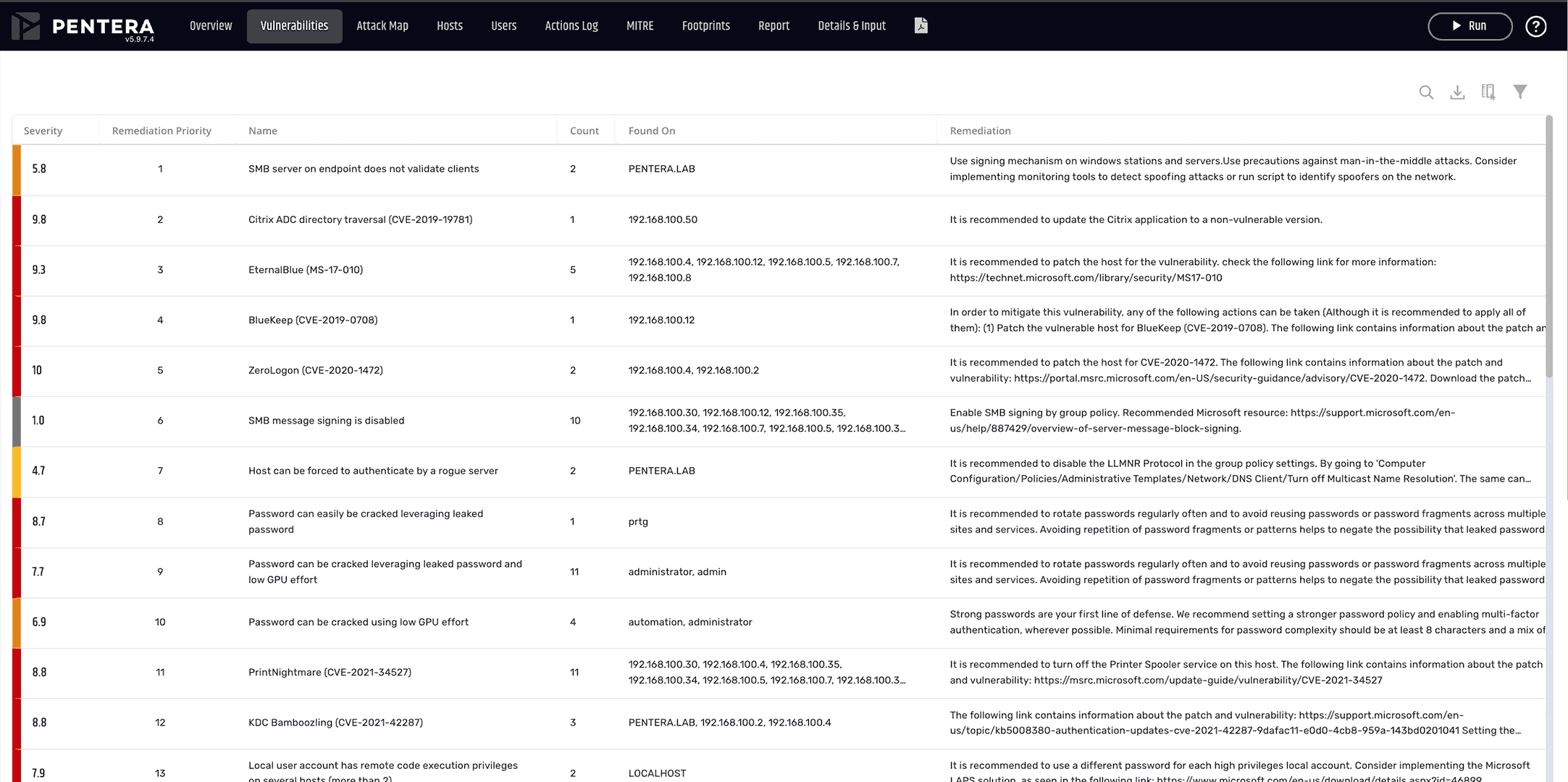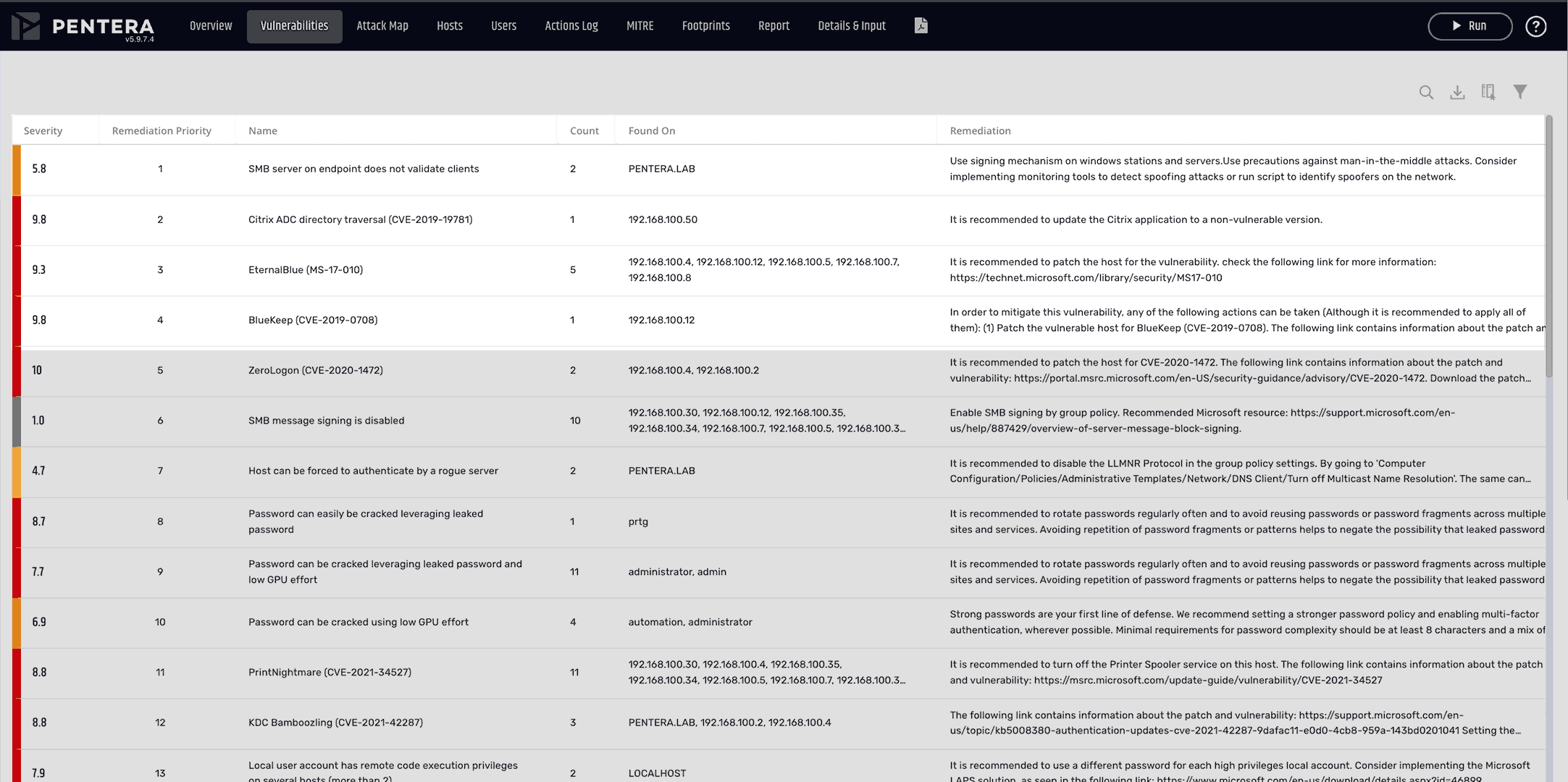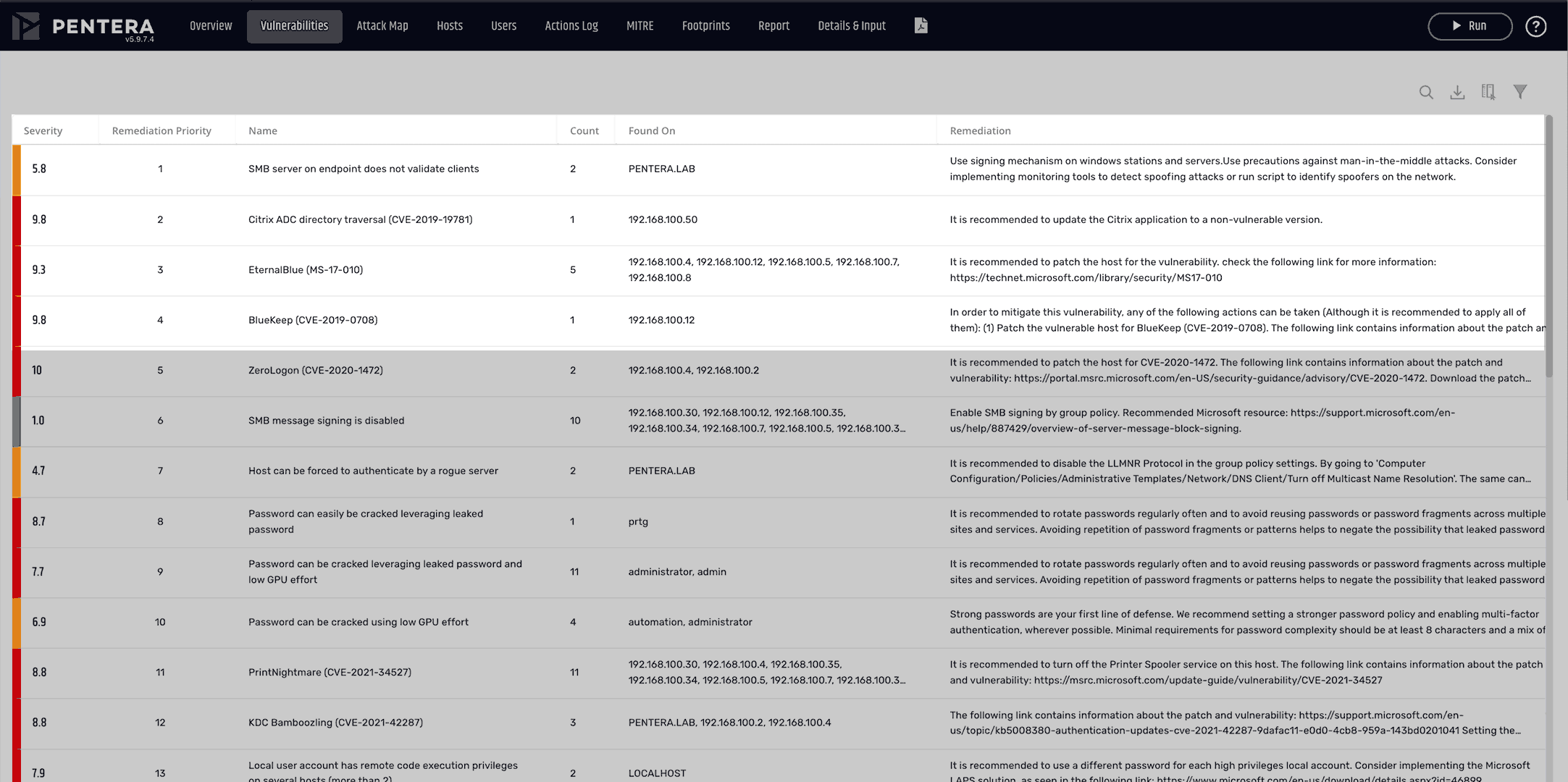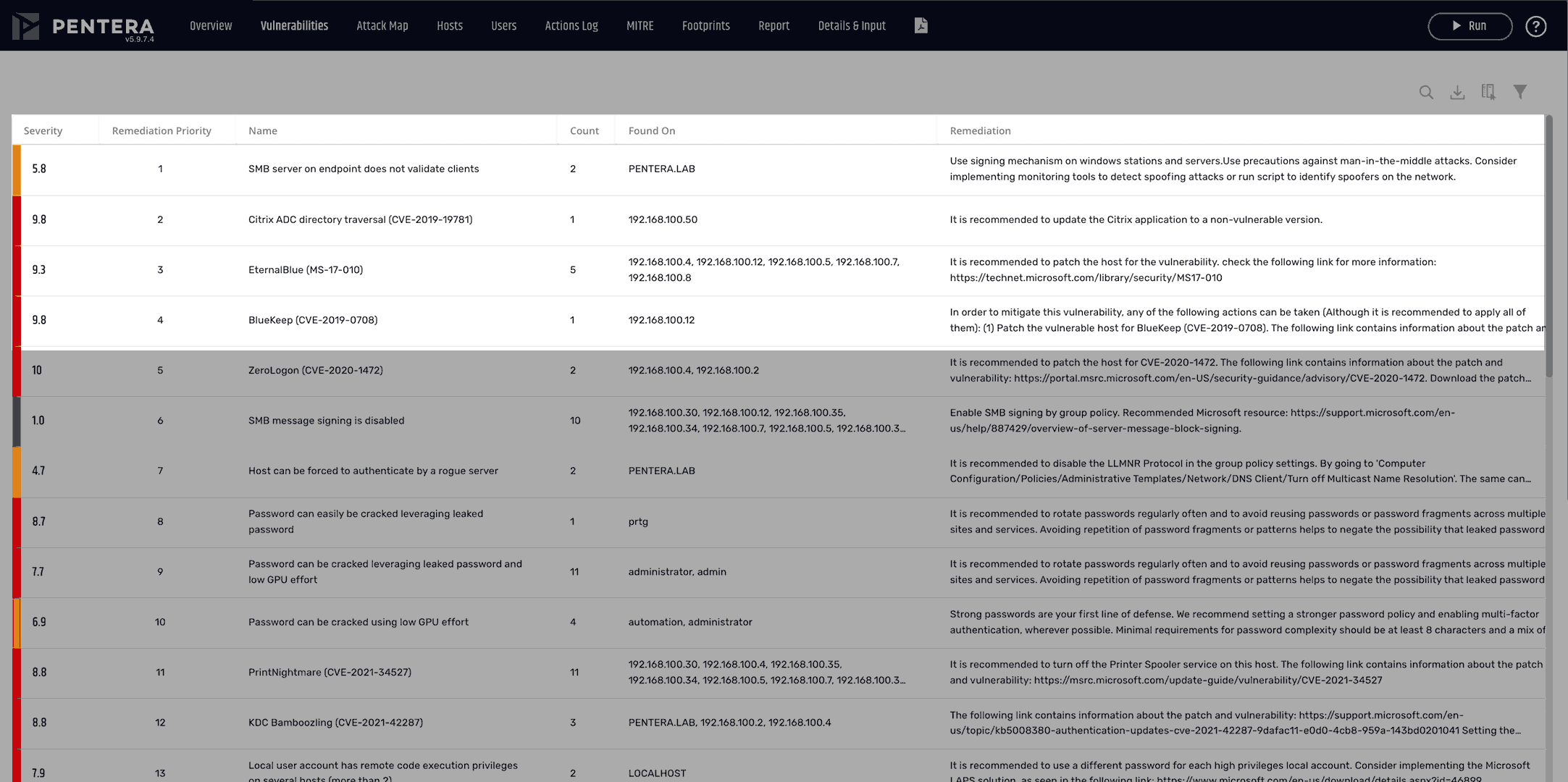
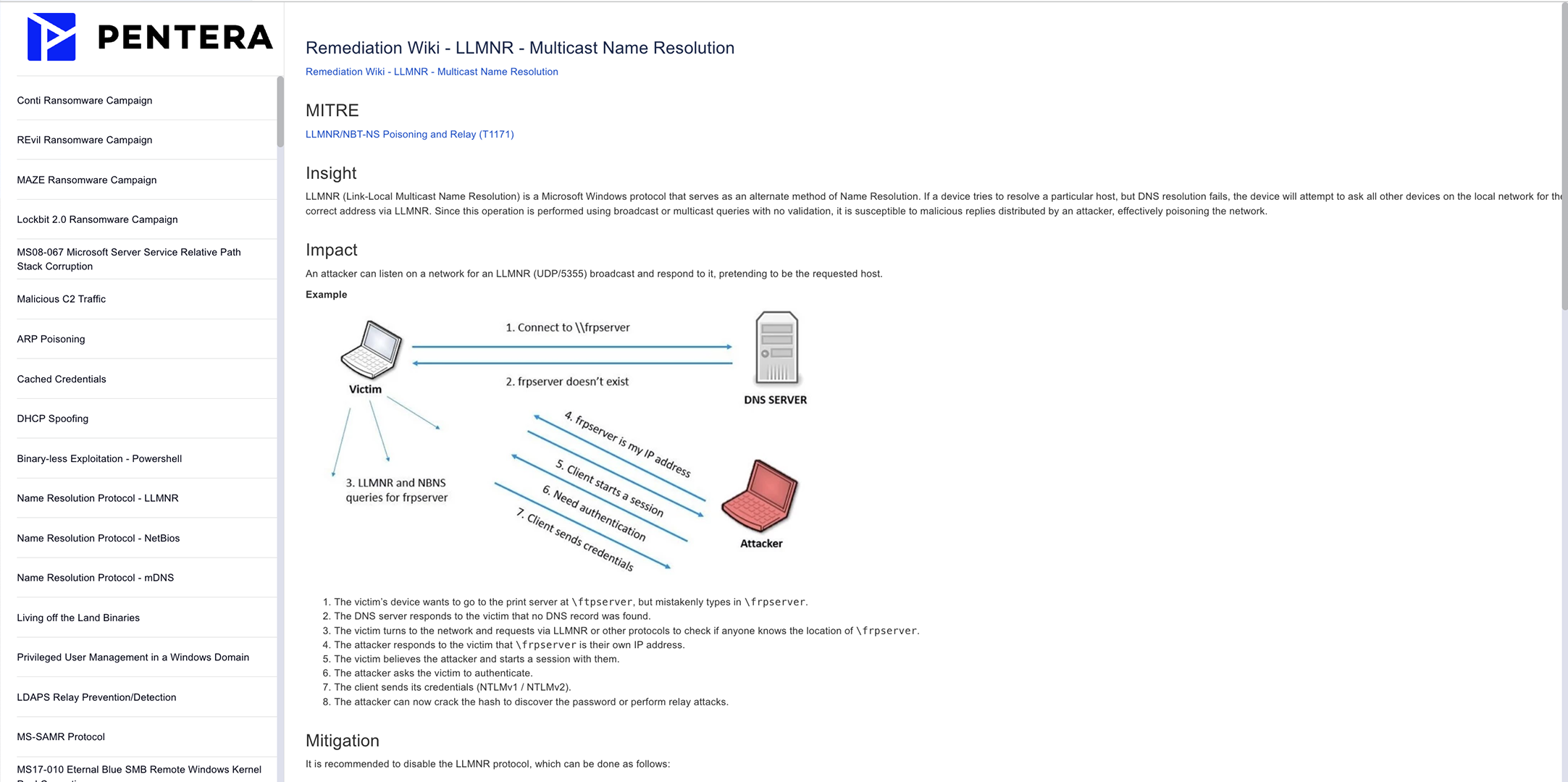
Vulnerability Prioritization
Focus on the critical risks
from an endless list of vulnerabilities.
Review impact of proven attack paths to identify your riskiest security gaps.
Pinpoint security gaps that really need to be fixed.
Automatically run real-world attacks to uncover security gaps with Pentera’s live testing. Identify and prioritize your most critical vulnerabilities, patchable or not, based on proof of the risk they pose to your business.