Learn about Automated
Security Validation™.
Build your roadmap to cyber exposure reduction.
Secure your digital world with Automated Security Validation™ (ASV).
In the world of cybersecurity, your main challenge is finding real security gaps among a sea of data. You’ve often had to make assumptions because the data in your vulnerability management systems can be wrong, old, and lack context.
As IT systems evolve, addressing real vulnerabilities before they become a problem is crucial. While penetration testing is accurate, it has limitations in scalability.
Knowing your vulnerabilities empowers you to direct your resources where they matter most. That’s where Automated Security Validation (SecVal) comes in. It sheds light on your real security concerns cost-effectively. SecVal provides you, the CISO, with fresh data reflecting the true impact of threats on your business.
Don’t assume. Validate.
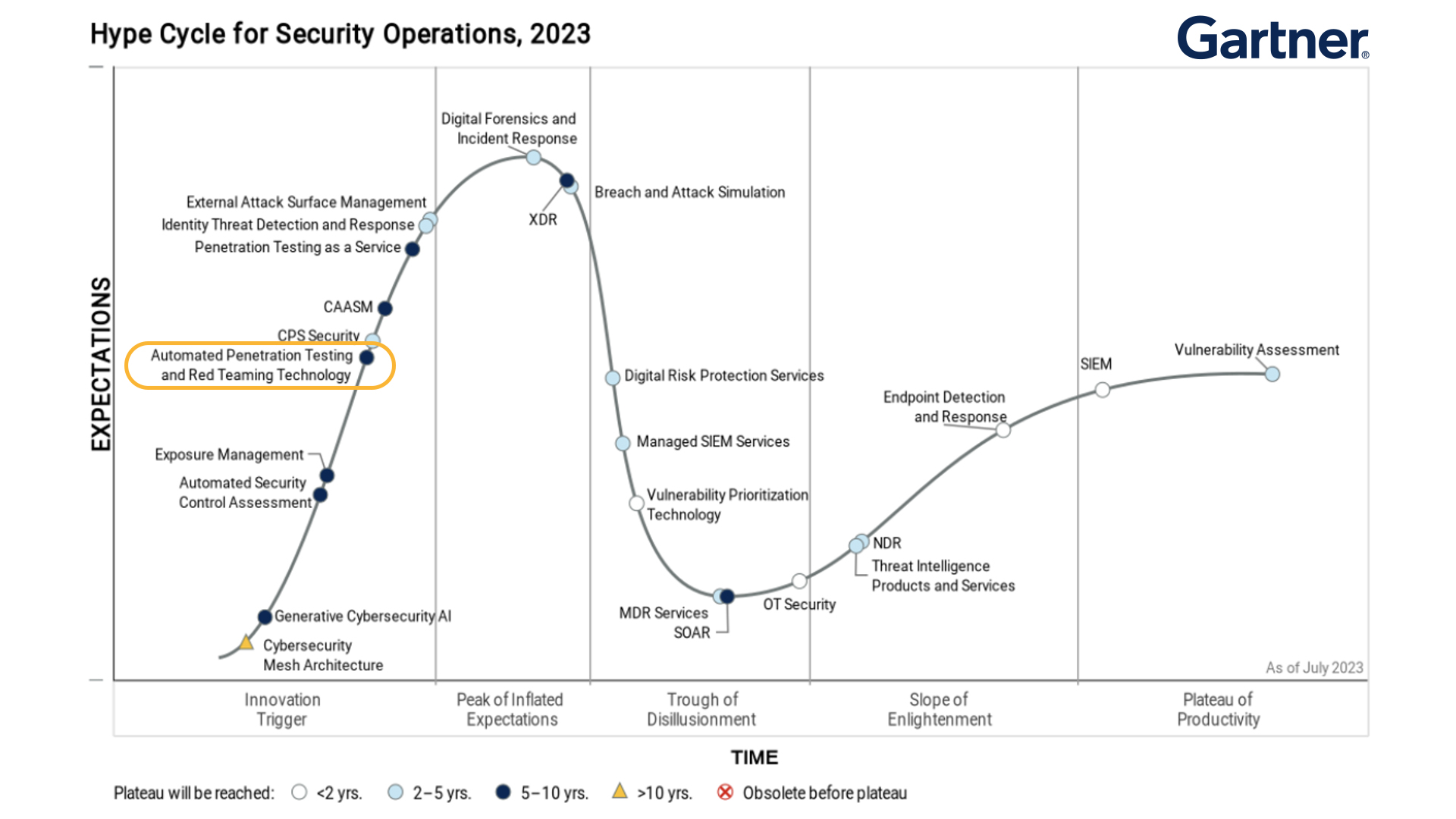
Take a closer look at the 3 pillars of Automated Security Validation™.

Why Automated Security Validation™?
Know your security true efficacy against the latest attacks, today and every day.
Fix your true security gaps, quickly.
See how ASV measures up against traditional security validation.
A side-by-side look comparing our Automated Security Validation™ approach vs. the old way of doing things.
Security
Validation
Attack
Simulation
(BAS)
Testing
Surface
Management
Management









