According to a Cisco CISO Benchmark survey, 17% of organizations had 100,000 or more daily security alerts in 2020, a number that has only increased since. In 2021, a record-breaking 20,137 Common Vulnerabilities and Exposures (CVEs) were discovered, surpassing the 18,325 CVEs reported in 2020. This sharp rise in vulnerabilities reflects the growing complexity of digital infrastructures and the corresponding expansion of organizations‘ exploitable attack surfaces.
For defenders, this exponential growth presents a dual challenge: sifting through a sea of vulnerabilities and avoiding cybersecurity burnout. It’s important to note, however, that „vulnerable“ doesn’t always mean „exploitable.“ Research shows that for every 100 vulnerabilities, only one is likely to be exploitable. The key to effective security lies in focusing on these exploitable attack surfaces—those that pose the greatest threat to your organization.
So, how can security teams achieve this focus? Below, we outline four steps to help you identify and manage your exploitable attack surface.
Step 1: Take the Adversarial Perspective
The only way to truly filter through a sea of vulnerabilities is to attempt to exploit them—just as an adversary would. This approach helps security teams identify the most critical attack vectors, pointing directly to an organization’s weakest link. By adopting this adversarial perspective, IT teams can:
-
Focus remediation efforts on vulnerabilities with the highest business impact.
-
Avoid spreading limited resources too thin across low-priority vulnerabilities.
-
Transition from reactive to proactive security practices.
Taking an attacker’s point of view ensures that organizations prioritize vulnerabilities most likely to lead to breaches, effectively managing their exploitable attack surfaces.
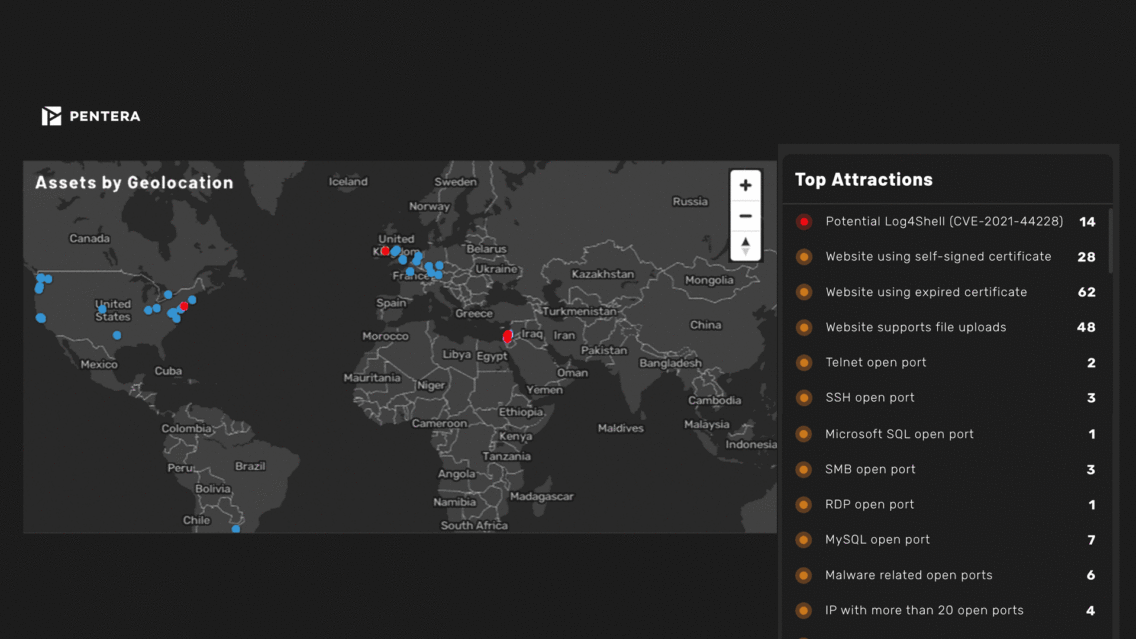
Attack Surface Monitoring Dashboard
For a deeper dive into how attackers exploit vulnerabilities, check out our detailed Continuous Security Validation blog.
Step 2: Expand Coverage of Your Exploitable Attack Surface
Adversaries exploit vulnerabilities wherever they find them, often using combinations of techniques to progress toward critical assets. Security validation must match this full-spectrum approach. A comprehensive penetration test should include:
-
Attack emulation frameworks for security controls.
-
Testing vulnerabilities and credential strength.
-
Audits of network equipment and privileged access.
-
Emulation of lateral movement steps.
By emulating real-world attack paths, security teams can identify exploitable gaps that static vulnerability scans might miss. This helps manage their exploitable attack surfaces more effectively. This comprehensive approach ensures organizations address risks beyond basic vulnerabilities, such as cloud security risks. This approach is a key aspect of red teaming, and it also ensures organizations address risks beyond basic vulnerabilities, such as cloud security risks.
Step 3: Automate Security Validation for Continuous Testing
Security validation today must be as dynamic as the attack surface it’s securing. Periodical and manual tests are no longer sufficient to challenge the changes an organization undergoes. Security teams need an on-demand view of their assets and exposures. The only way to achieve this is through automating testing, a key step in effectively managing an exploitable attack surface.
For instance, automated testing platforms like Automated Security Validation (ASV) emulate adversary tactics to expose security gaps while prioritizing remediation efforts. Learn more about the importance of Automated Penetration Testing.
The growth in digitalization and cloud adoption, remote work, ransomware threats, and recent vulnerabilities like Log4Shell are just a few examples of how important continuous validation is for security teams to properly defend their organization. Continuous testing is a crucial component of effective SOC optimization.
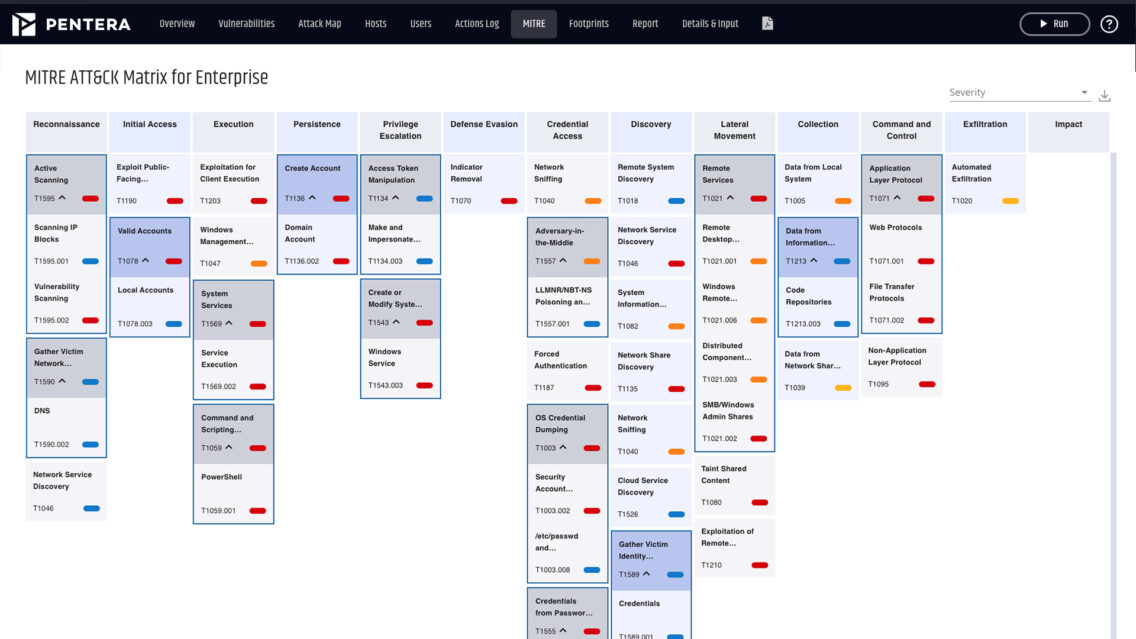
Step 4: Align to MITRE ATT&CK and OWASP Top Ten
Aligning with established frameworks such as MITRE ATT&CK® and OWASP Top Ten ensures comprehensive coverage of adversary techniques and common vulnerabilities. These frameworks provide a structured approach to:
-
Identify and challenge security controls.
-
Validate readiness against the most common tactics, techniques, and procedures (TTPs) used by attackers.
-
Communicate validation results clearly to stakeholders and management.
By aligning their security programs to these frameworks, organizations can confidently report on their security posture and ensure their defenses are robust against modern threats.
Validate Security Against MITRE ATT&CK
Automated Security Validation for Managing Your Exploitable Attack Surface
Automated security validation is an advanced approach to testing the integrity of all cybersecurity layers, combining continuous coverage and risk prioritization for effective mitigation of security gaps.
This approach provides a true view of current security exposures by emulating real-life attacks, enabling an impact-based remediation plan rather than chasing thousands of vulnerabilities.
Security teams can know exactly where they stand and confidently strive towards maximum security readiness.
When evaluating security validation platforms make sure to check these boxes:
- Agentless, low-touch implementation – to ensure minimum to no overhead.
- Automated, zero playbook testing, providing a consistent process for security gap discovery and remediation.
- Safely attack the production network, leveraging ethical exploits to emulate the adversary without disrupting business operations.
- Validate the entire security stack with full scope of real-world techniques aligned to industry frameworks.
- Expose security gaps in cloud workloads and emulate lateral expansion weaknesses from on-prem to the cloud to the remote workforce.
- Immediate reporting that provides a prioritized list of which vulnerabilities are critical to fix based on business impact.
Final Thoughts
Knowing your exploitable attack surface is essential to proactive security. By taking an adversarial perspective, covering the full scope of potential attacks, leveraging automation, and aligning with industry standards, organizations can focus on vulnerabilities that matter most.
The question that needs answering is whether you know your organization’s true security risk at any given time. Do you know where the organization’s weakest links are so they can be remediated or mitigated before an attacker leverages them towards an attack?
If you’re ready to validate your organization against the latest threats including ransomware strains and Log4Shell vulnerabilities, request your free security health check today.
Discover how to effectively monitor and protect your attack surface with our Attack Surface Monitoring solutions.
Originally published on Dark Reading.