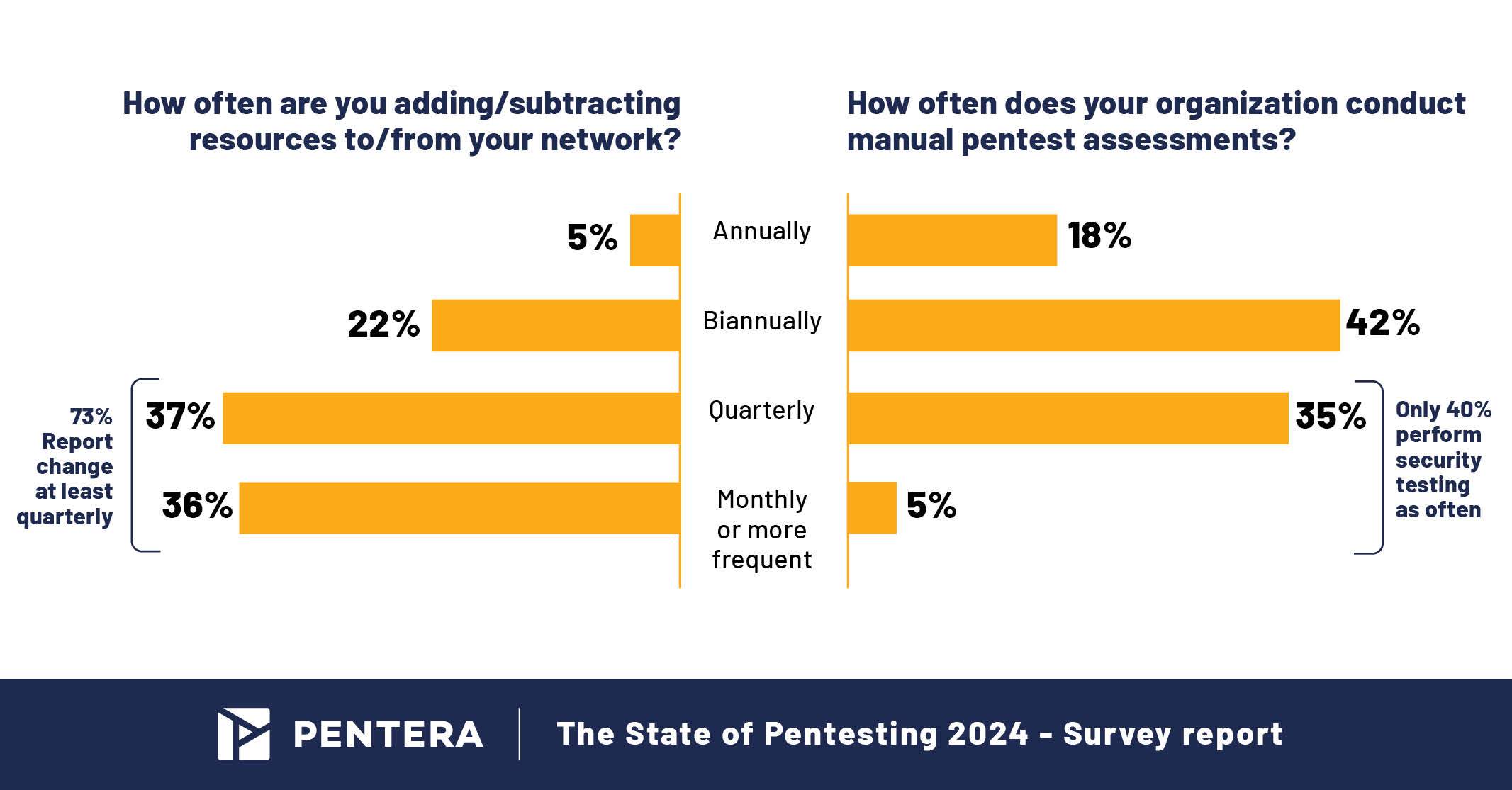
With 73% of organizations tweaking their IT setups every quarter, it’s concerning that only 40% are aligning their security checks accordingly. This frequency gap leaves organizations vulnerable to prolonged risk and highlights a critical area for improvement. Ensuring security measures evolve in tandem with IT changes isn’t just advisable—it’s essential for safeguarding digital assets. One approach organizations are adopting to keep pace is Continuous Security Validation, ensuring security defenses remain effective as environments change.
This insight is part of Pentera’s State of Pentesting Report, which delves into the current state of security validation practices, focusing on the pivotal roles of pentesting and red-teaming.
The analysis, conducted by Global Surveyz Research, involved 450 security professionals from the US, UK, Western Europe, and APAC, across enterprises with over 1,000 employees.
Key Findings from the Pentesting Report
Evolving Motivations for Pentesting
Securing the IT environment and assessing the impact of a successful attack have become the primary reasons for penetration testing, moving beyond compliance requirements. This shift signifies a stronger focus on continuous security validation and proactive cybersecurity.
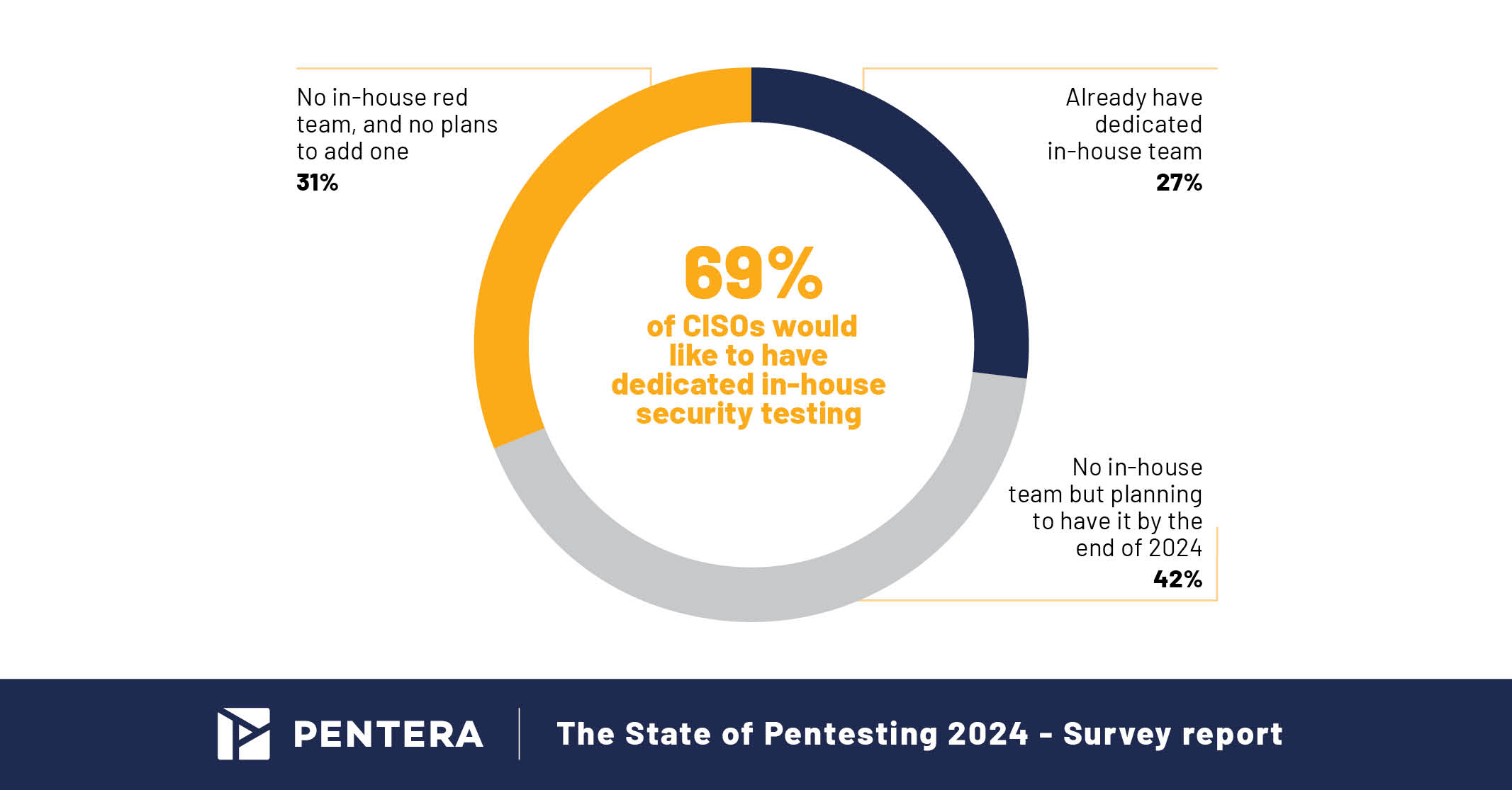
Increased Involvement from Boards
Over 50% of CISOs are sharing pentest results with their executive teams and Boards, reflecting greater involvement of upper management in cybersecurity. This transparency highlights the critical nature of aligning security practices with business needs.
Rising Concerns about Internal Remediation
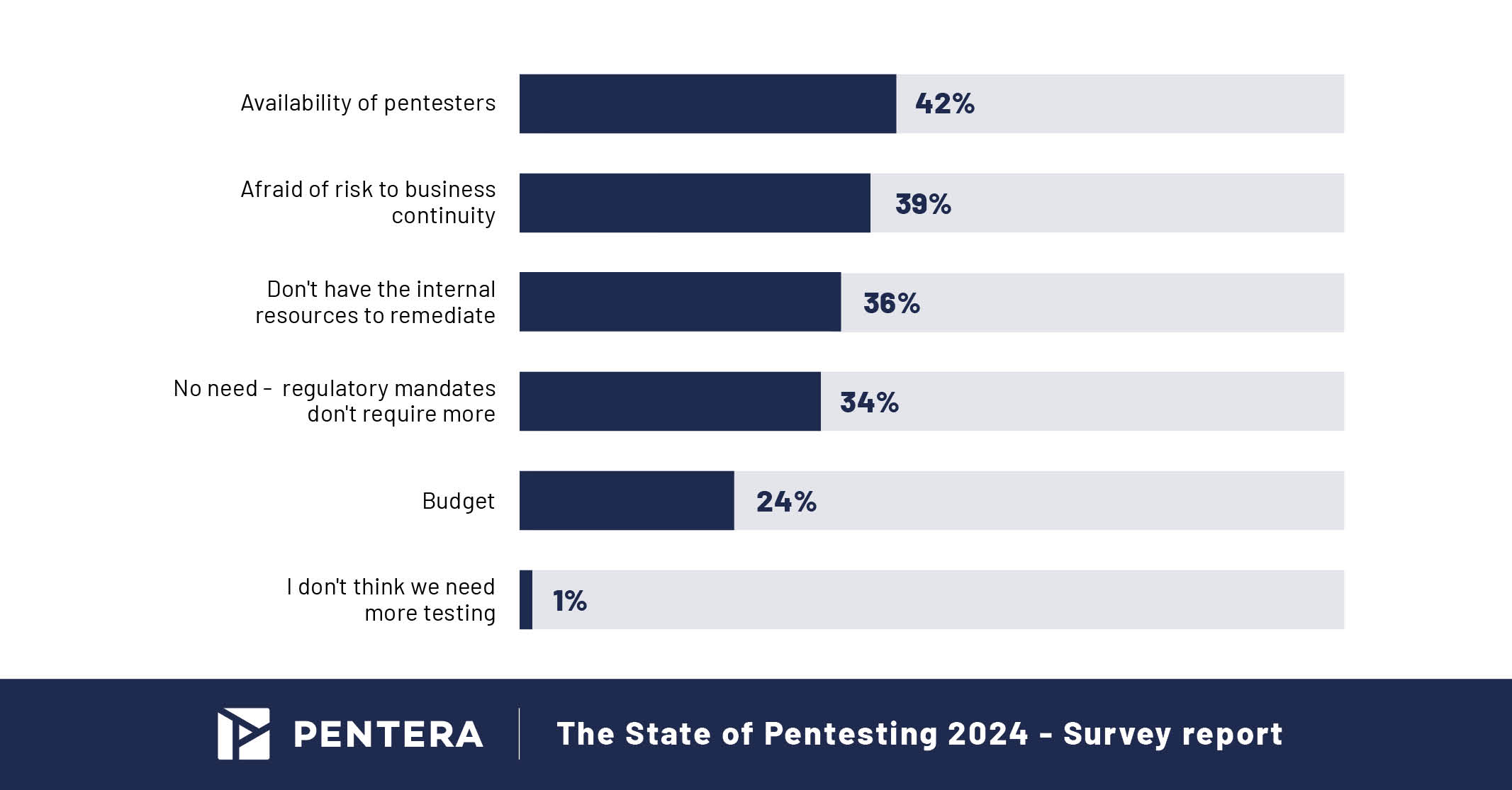
In 2024, 36% of respondents cited internal remediation capabilities as a barrier, a significant increase from 21% in 2023. This reflects the growing challenge of ensuring vulnerabilities are fixed efficiently without disrupting operations.
Barriers to Effective Pentesting
One major barrier to effective pentesting remains the availability of skilled pentesters. Additionally, concerns about business continuity persist, with some organizations hesitant to undertake pentests due to potential downtime.
Pentesting as a Strategic Tool in M&A
Pentesting is increasingly being used in M&A activities to assess cybersecurity risks. By understanding potential vulnerabilities, businesses can avoid inheriting cyber risks from acquired companies.
Why Aligning Security Testing with IT Infrastructure Changes Matters
The survey data provides a roadmap for CISOs to align their security testing frequency with IT infrastructure changes. Implementing regular and frequent security testing can dramatically reduce exposure and safeguard organizational assets from evolving threats.
Interested in more? For those in the trenches of cybersecurity, these insights are invaluable for shaping a proactive, informed approach. Download the full report.