What is CVE-2024-47176? A Linux Privilege Escalation Vulnerability
CVE ID: CVE-2024-47176
Description: A privilege escalation vulnerability in the Common UNIX Printing System (CUPS) affects the cups-browsed service, a helper for the main CUPS service. Attackers can exploit this flaw by crafting malicious packets targeting the exposed cups-browsed service on port 631/UDP. This can trigger the service to connect back to the attacker, potentially leaking valuable information that aids in privilege escalation.
Affected Vendors/Products: Most Linux distributions using CUPS, specifically with cups-browsed service up to version 2.0.1, which may be installed on various Linux distributions, including Ubuntu, Debian, Red Hat, and SUSE.
CVSS Score: 5.3 (Medium)
Pentera Severity Rating: 8.4 (High)
How Attackers Exploit CVE-2024-47176
Attack Vector: Remote exploitation possible. An attacker with network access to the target machine via port 631/UDP can craft malicious packets to trigger the vulnerability in the cups-browsed service, potentially leading to privilege escalation.
Potential Impact: Successful exploitation of this vulnerability, in combination with a chain of related CVEs (e.g., CVE-2024-47076, CVE-2024-47175, CVE-2024-47177), can allow an attacker to escalate privileges to root, granting arbitrary command execution and privilege escalation.
Threat Profile: Despite its CVSS rating of 5.3 (Medium), Pentera assigns this CVE a severity rating of 8.4 (High) due to its potential for local privilege escalation to root. This vulnerability opens an inevitable chain of vulnerabilities that leads to Remote Code Execution (RCE) and Privilege Escalation (PE).
Real-World Exploits: How Hackers Use CUPS Vulnerabilities
- Historical Context: Similar vulnerabilities in CUPS, such as CVE-2022-26691, have been exploited in Linux privilege escalation attacks.
- Threat Actor Usage: Threat actors have leveraged similar CUPS privilege escalation vulnerabilities in past Linux attacks, often chaining them with local exploits (e.g., kernel privilege escalation flaws) to gain full system control. This type of misconfiguration is commonly exploited in multi-user Linux environments, such as shared workstations and on-premises servers, to escalate privileges and move laterally within a network.
How to Discover and Validate CVE-2024-47176 in Your Environment
Pentera’s security validation platform automatically identifies instances of this vulnerability in enterprise environments.
Security teams can validate exploitability and understand potential attack paths before adversaries leverage the weakness.
This capability is available to Pentera customers who have updated to Cyber Pulse update release v6.3.7 or higher.
Why CVE-2024-47176 Matters: Security Risks & Prevention
Pentera’s Security Validation: Detect & Validate CVE-2024-47176
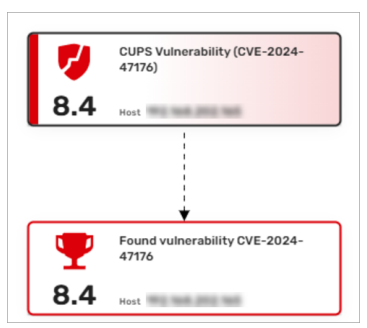
Pentera can discover this widely found CVE. You will discover its appearance in the attack map as a vulnerability – 8.4 CUPS Vulnerability and as an achievement 8.4 Found vulnerability CVE-2024-47176.
How to Fix CVE-2024-47176: Remediation & Mitigation
- Update CUPS software version – Update to the latest version provided by your Linux distribution.
- Remove unnecessary permissions
- Remove the cups-browsed service if not required, as it is often unnecessary for the core CUPS functionality.
- Configure cups-browsed to use DNS-SD instead of the CUPS service by modifying cups-browsed.conf
- Block traffic to port 631/UDP from unnecessary network segments using firewall rules or with ufw (on Ubuntu/Debian)
- Implement AppArmor/SELinux policies – Restrict the execution of privileged binaries.
- Regularly audit system permissions – use tools like Lynis or OpenSCAP.
Continuous validation with Pentera ensures you find and mitigate this CVE before attackers exploit it. Stay ahead of threats with real attack emulations. Discover how Pentera validates your security.
Frequently asked questions
What is CVE-2024-47176?
CVE-2024-47176 is a privilege escalation vulnerability in the Common UNIX Printing System (CUPS), specifically affecting the cups-browsed service. Attackers can exploit this flaw by sending malicious packets to an exposed port 631/UDP, potentially leading to information disclosure and privilege escalation.
How does CVE-2024-47176 impact Linux systems?
This vulnerability allows attackers to exploit the cups-browsed service to gain unauthorized access, leak sensitive system information, and escalate privileges to execute commands as a higher-privileged user, including root.
Which Linux distributions are affected by this vulnerability?
Most Linux distributions using CUPS with cups-browsed service (up to version 2.0.1) are vulnerable, including: Ubuntu, Debian, Red Hat, SUSE.
What is the CVSS score and severity rating for CVE-2024-47176?
CVSS Score: 5.3 (Medium) Pentera Severity Rating: 8.4 (High) Pentera rates this vulnerability as high risk due to its ability to be chained with other CVEs for root privilege escalation and remote code execution (RCE).
How do attackers exploit CVE-2024-47176?
An attacker with network access can: 1. Send malicious packets to port 631/UDP, causing cups-browsed to interact with a remote attacker-controlled machine. 2. Extract system details, including user configurations and running services. 3. Chain it with other vulnerabilities (e.g., CVE-2024-47076, CVE-2024-47175, CVE-2024-47177) to escalate privileges and achieve remote code execution (RCE).
Has CVE-2024-47176 been exploited in real-world attacks?
While there are no publicly known attacks yet, similar CUPS vulnerabilities (e.g., CVE-2022-26691) have been used in Linux privilege escalation attacks, often combined with kernel exploits to gain full system control.
How does Pentera help validate and mitigate CVE-2024-47176?
Pentera’s continuous security validation platform: 1. Automatically detects instances of this vulnerability in enterprise environments. 2. Emulates real-world attacks to assess exploitability. 3. Provides actionable remediation insights to mitigate exposure before attackers exploit it.