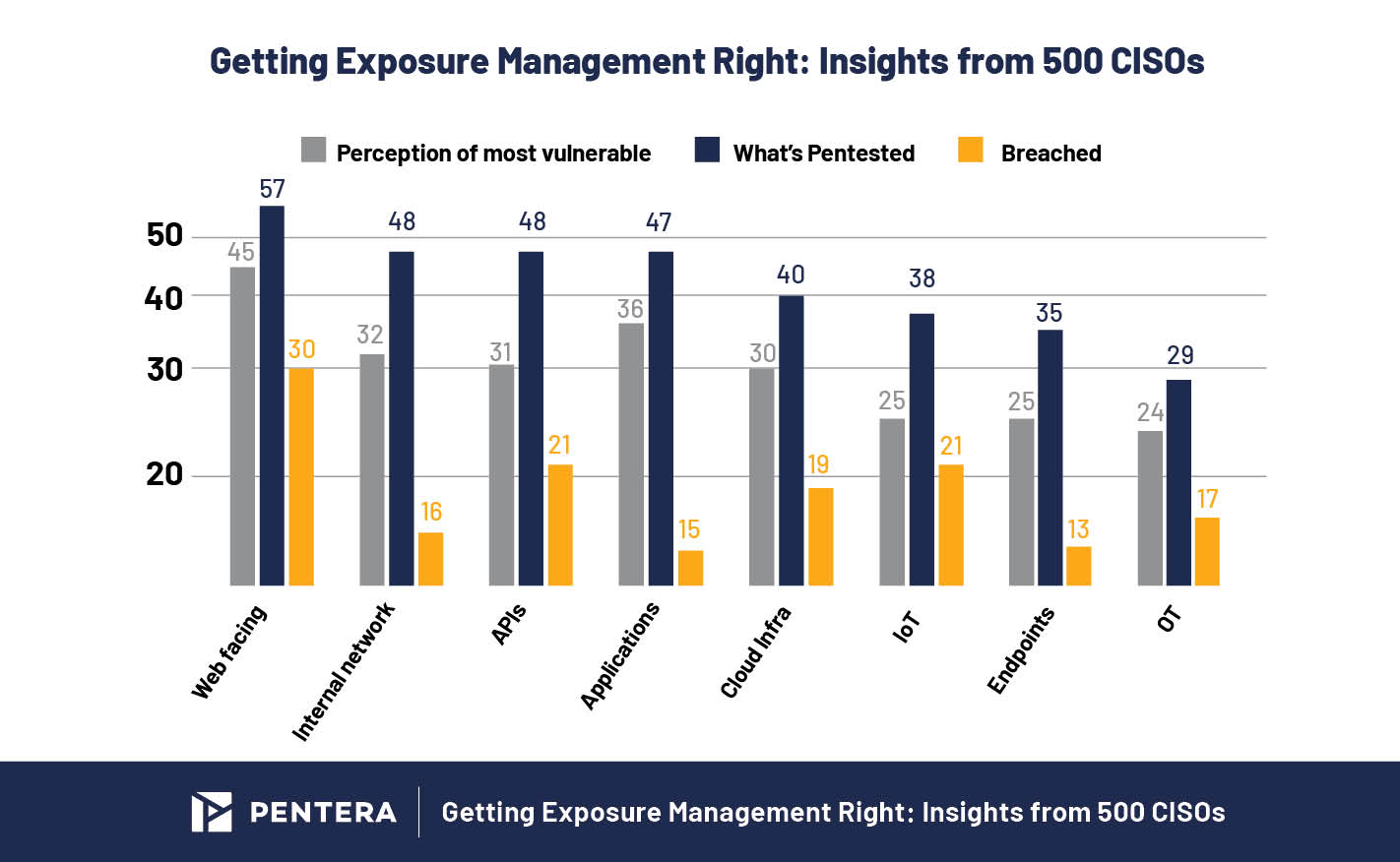
Results from Pentera’s 4th Pentesting report, which surveyed around 500 CISOs globally, show that while Exposure Management practices are maturing, there are still some gaps the market is yet to address.
The modern attack surface is sprawling, dynamic, distributed, and dangerously opaque. As enterprises expand into cloud-native or hybrid architectures, deploy APIs by the thousands, and integrate IoT and OT devices into core operations, the surface area for cyber threats grows both in size and complexity. Today, the average enterprise manages 75 security tools, and nearly half of CISOs report continued growth in their security stacks year over year.
This complexity isn’t deterring attackers. It enables them. Threat actors operate opportunistically. No surface is safe because attackers are driven to exploit whatever is exposed; they’re ultimately motivated to target surfaces that are relatively weaker than the next. For security leaders, this means it’s not a question of how to cover more ground, but where to focus for maximum security – where across the attack surface is the threat of risk most implicated?
The recently released 2025 State of Pentesting report by Pentera reveals the relative vulnerability of different attack surfaces, from cloud infrastructure and web-facing assets to APIs, endpoints, and even IoT systems. CISOs from 500 enterprises were asked where across their network they perceive risk, where pentesting efforts are directed, and which areas were ultimately breached. The results provide insight for security teams to sharpen their focus, direct their testing strategies, and close the riskiest exposures faster.
The Little Realized Truth about Exposure Management
Even with the best-run exposure management programs, breaches still occur. But working within more mature security programs, you realize a breach doesn’t always mean compromise.
Take the example of an exposed asset. It might be breached in the technical sense—perhaps even with a threat actor establishing a foothold on it.. But if that asset isn’t tied to sensitive data, production systems, or critical services, the real-world impact is negligible. Not all breaches are equal. That’s the foundational mindset shift exposure management brings.
Unlike traditional vulnerability management, where teams are chasing down CVEs based on severity scores or ticket age, exposure management is strategic. It considers both exploitability and impact to determine what vulnerabilities actually matter. This dual lens allows teams to bypass the noise and zero-in on the exposures that can lead to devastating compromise.
The State of Pentesting report reinforces this truth. Despite nearly 67% of enterprises reporting a breach in the past two years, only 36% faced downtime, 30% suffered data exposure, and 28% incurred financial loss. That means a significant portion of “breaches” had little or no operational consequence. The goal isn’t to eliminate every breach – but only the ones that will hurt you.
Web-Facing Assets – Still the Weakest Link
If exposure management is about aligning remediation with risk, web-facing assets are the prime example of a cautionary tale.
According to the data, web-facing assets top all three metrics: they’re perceived as the most vulnerable (45%), tested the most (57%), and breached the most frequently (30%).
In some ways this is encouraging. It shows that security teams are accurately prioritizing external assets, recognizing them as both accessible and attractive targets, and directing pentesting efforts accordingly.
But despite all that attention, attackers are still getting in.
Why? Because just on the basis of exposure, web-facing assets are risky. These systems – DNS, web portals, and login pages are designed to be reachable. Their openness makes them “low-hanging fruit,” especially when misconfigurations, exposed services, or open ports are left unchecked and without compensating controls such as MFA.
Yet this doesn’t mean failure.
If attackers breach a public-facing asset and reach a dead end – no access to sensitive systems, no valuable data, no lateral movement – then, so what? The breach had no impact. In exposure management, it’s not just about reducing breach rates – it’s about reducing the impact of breaches that do occur.
Internal Networks, Endpoints, and Applications – A Contained Front
When it comes to systems closest to the crown jewels, organizations are getting it right. They’re widely tested (48%) considered vulnerable (32%), and are seeing low breach rates (16%).
Internal networks, endpoints, and applications each rank in the top tier for pentesting activity and show comparatively low breach rates, 16% for internal networks, 13% for endpoints, and 15% for applications. All suggesting a payoff in focused effort.
These are systems that house sensitive data, power operations, and represent a clear path to lateral movement or privilege escalation. Their perceived criticality earns them a greater level of focus and attention, with layered security controls and tooling that’s more mature. It also reflects something deeper: exposure management maturity. Organizations aren’t just scanning these systems for vulnerabilities, they’re pentesting them in context, prioritizing based on potential impact, and validating to confirm that defenses hold under pressure.
API Risk – Shows Gap Between Perception and Reality
APIs sit at the intersection of business logic and backend systems. They’re essential, deeply integrated, and often overlooked, with data from the survey report indicating APIs may be more vulnerable than security teams realize.
While APIs are tested at a similar rate to internal networks (48%), they show a higher breach rate, 21%, compared to 16% for internal networks. That gap suggests a disconnect: either the perceived risk of APIs is too low, or current testing approaches aren’t revealing the full picture.
The challenge is complexity. APIs are dynamic, hard to inventory, and notoriously difficult to test well. Their attack surface isn’t just about ports or endpoints, it’s about logic flaws, broken authentication, and misconfigured integrations, all leading to attack pathways that don’t show up in a standard scan.
APIs also frequently bridge systems, whether between cloud services, third-party tools, mobile apps, and internal databases. That makes them prime targets for lateral movement or data exfiltration. And their visibility gap makes them especially attractive to attackers who understand how to move below the radar.
Closing the gap means leveling up testing, both in terms of frequency and depth. Continuous, adversarial testing of APIs is essential to expose integration flaws that traditional methods appear to be missing.
Exposure Management Shows Encouraging Signs of Alignment
The 2025 State of Pentesting report confirms what we’ve known for years – closer proximity to business risk drives sharper execution.
There’s growing alignment between perceived risk, pentesting activity, and breaches. A strong signal that exposure management practices are maturing, as teams are minimising the gap between assumed and actual risk.
The goal of exposure management isn’t to prevent every breach. It’s to prevent the ones that matter. By combining data-driven prioritization with continuous validation, security teams can focus on real exposures, not theoretical threats. Ensuring that when the attacker comes knocking, there’s nothing valuable behind that door.
To learn more about how leading enterprises are implementing their Exposure Management programs, attend Xposure, the National Exposure Management vSummit. Register Now