As cloud infrastructure adoption grows, it’s a mistake to assume that these environments are inherently secure. In fact, as reported by StrongDM, “public cloud breaches tend to be more expensive than hybrid cloud breaches, with an average cost of $6.35 million for data breaches in the cloud as of 2022.” Additionally, “misconfigurations in cloud environments, which are common, can cost companies around $3.86 million per incident.” While on-prem incidents can be far less costly, they’re oftentimes followed by significant downtime and have other operational ramifications for the organization (Varonis).
Both on-premise and cloud environments demand careful security scrutiny. In this article, we explore the architectural considerations, security implications, and key penetration testing strategies for each approach.
Environment Architecture
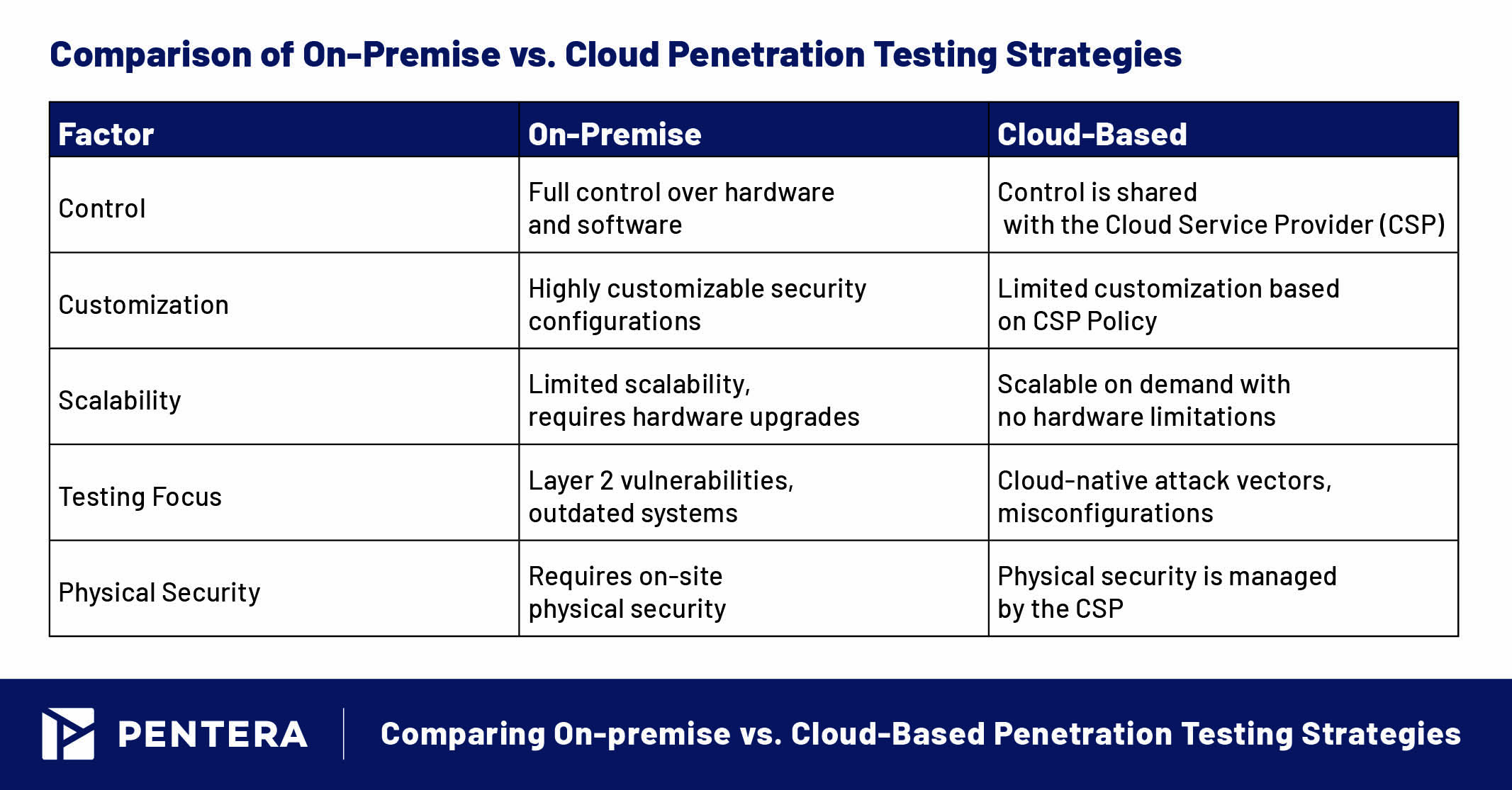
Understanding the underlying architecture is crucial for identifying potential security gaps. Here’s a breakdown of the key components for on-premise and cloud environments.
On-Premise:
- Control and Customization: On-premise infrastructure offers complete control over hardware and software configurations. This allows for customized security measures that help mitigate vulnerabilities unique to the environment.
- Data Sensitivity: Organizations dealing with highly sensitive data often prefer on-premise solutions to keep information within the physical boundaries of the company, reducing external risks.
- Regulatory Compliance: Industries with strict regulatory requirements (e.g., healthcare, finance) benefit from on-premise setups, which can be tailored to meet compliance standards and safeguard sensitive data.
Cloud-Based:
- Scalability: Cloud infrastructure provides unparalleled scalability, enabling organizations to adjust resources as needed. However, rapid scaling can introduce risks if configurations aren’t properly managed.
- Accessibility: Cloud environments allow remote access, enabling penetration testing teams to assess infrastructure from any location. While this speeds up responses to emerging threats, regular audits of externally facing resources are necessary to avoid exposure.
- Cloud-Native Security: Cloud-based environments benefit from using cloud-native attack emulations to test for exploitable exposures. This ensures your cloud infrastructure is tested against real-world attack techniques and potential vulnerabilities.
Penetration Testing: On-Premise vs. Cloud
In addition to architectural differences, penetration testing strategies vary significantly between on-premise and cloud environments. Certain attack vectors are restricted to specific architectures, and penetration testing methods must be adapted accordingly.
On-Premise:
- Physical Security: On-premise systems are vulnerable to physical attacks, such as unauthorized access to data centers or social engineering breaches. Implementing strong physical security measures is critical to prevent these risks.
- Insider Threats: Insider threats are a significant concern in on-premise environments. Regular employee training on security best practices is essential, as human error remains a common point of failure in security strategies.
- Maintenance and Updates: Keeping on-premise infrastructure secure requires regular updates and patches. Decommissioning outdated systems is also vital, as they can harbor vulnerabilities that attackers can exploit.
Cloud-Based:
- Shared Responsibility: In the cloud, security responsibilities are shared between the cloud service provider (CSP) and the customer. It’s important to understand this delineation to ensure comprehensive security coverage.
- Data Transmission: Encrypting data in transit between on-premise and cloud systems is necessary to prevent interception by malicious actors. Secure communication channels and robust encryption protocols are essential components of cloud security.
- Multi-Tenancy Risks: Cloud environments often host multiple tenants on shared infrastructure. Isolation mechanisms must be implemented to prevent cross-tenant attacks. Additionally, it’s important to follow the CSP’s penetration testing guidelines to avoid impacting other clients on the same shared infrastructure.
Cloud-based environments require penetration testing tailored to cloud-native risks, such as misconfigurations and improper access controls. For example, companies like Wyndham Hotels & Resorts use Pentera’s platform to continuously validate their cloud security. By leveraging Pentera’s automated cloud attack simulations, Wyndham is able to assess its cloud environment regularly without depending on external pentesters. The testing helped the company ensure resilience during cloud migration, while also reducing manual security efforts.
Similarly, Blackstone implemented Pentera’s continuous security validation to safeguard both their on-premise and cloud environments. Blackstone’s security team benefited from real-time vulnerability insights across their hybrid infrastructure, prioritizing risks and reducing remediation time.
Penetration Testing Attack Vectors
Penetration testing should cover common attack vectors that affect both on-premise and cloud environments.
Both environments face risks from phishing and social engineering attacks, making employee training a priority. Cloud providers often offer built-in Distributed Denial of Service (DDoS) protection, but on-premise systems may require additional investments in DDoS mitigation. Malware and ransomware remain significant threats across both environments, requiring endpoint security, regular backups, and incident response plans. In cloud environments, leveraging cloud-native security services enhances protection, but endpoint security remains critical as attackers still target devices accessing cloud systems.
Continuous vulnerability scanning and patch management are necessary for both on-premise and cloud infrastructures, as new exploits frequently target legacy systems. Regular audits of port and network configurations are essential, especially in cloud environments, to prevent misconfigurations like exposed firewalls from leaving resources vulnerable.
Choosing the Right Penetration Testing Approach for Your Environment
Penetration testing strategies for on-premise and cloud environments shouldn’t follow a one-size-fits-all approach. On-premise environments should focus on identifying vulnerabilities in protocols and network layers, while cloud-based solutions should leverage cloud-native attacks to test for exploitable exposures. This proactive approach ensures each environment is tested against real-world attack scenarios, helping to identify weaknesses that attackers could exploit.
Cloud-native attack emulations mimic real-world adversarial behavior using techniques aligned with the MITRE ATT&CK framework. For example, Pentera’s platform emulates lateral movement within cloud workloads to validate an organization’s defense against privilege escalation and identity compromise in cloud environments.
As organizations increasingly adopt hybrid infrastructures, it’s critical to have a solution capable of tracking attack paths seamlessly from on-premise to cloud and vice versa. A platform like Pentera can provide continuous security validation across both environments, helping to identify and mitigate risks in real-time while ensuring comprehensive coverage against evolving attack vectors.
Explore how Pentera Cloud’s Automated Penetration Testing can improve your cloud and on-prem security or schedule a demo to discover how Pentera can strengthen your security posture.