The countdown to January 2025 is on, and for financial institutions in Europe, the Digital Operational Resilience Act (DORA) isn’t just another regulation—it’s a mandate that carries significant consequences. Failing to comply means facing steep penalties and potential damage to your institution’s reputation.
Understanding DORA’s ICT Risk Management Framework
In November 2022, the EU introduced a uniform Information and Communication Technology (ICT) risk management framework, impacting over 22,000 financial entities and ICT service providers across the EU and beyond. With relevance not only to organizations based in the EU, but also operating in the EU, DORA is based on the TIBER-EU framework and was born out of the growing complexity of cyber threats and the urgent need for operational resilience.
The primary requirements of DORA include:
I – Implementing a comprehensive ICT risk management framework
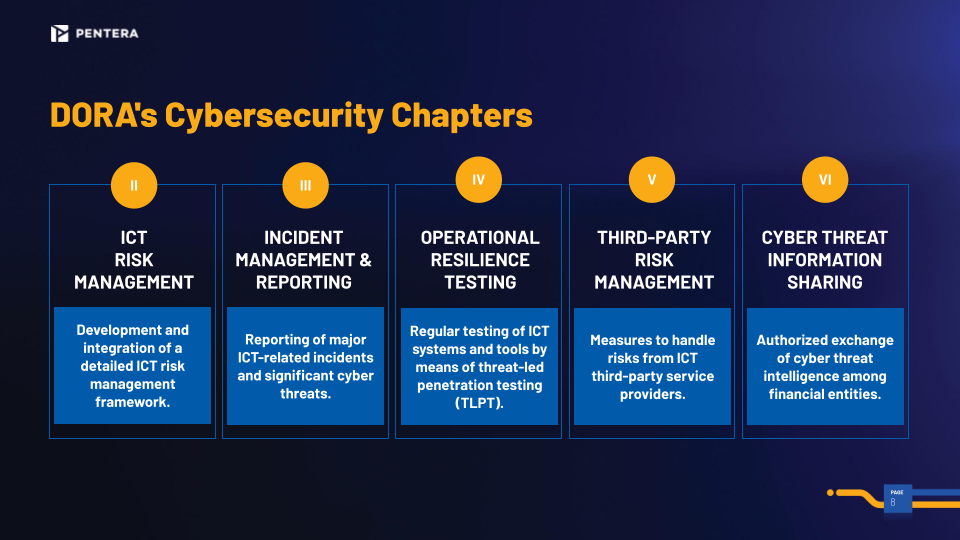
II – Promptly reporting major ICT incidents to authorities
III – Testing program for digital operational resilience
IV – Management of ICT third-party risk
V – Sharing cyber threat intelligence to other financial entities
In this article we provide a summary of the first four requirements and where Pentera is able to support compliance.
Chapter I – ICT Risk Management
At the core of DORA’s requirements is the establishment of a robust ICT risk management framework that builds the resilience of business-critical systems. This framework should be comprehensive, well-documented, and integrated into the overall risk management system of the financial organization.
Where Pentera is able to assist:
- Documenting critical ICT assets and business functions. Identify critical assets and align them to classification groups based on criticality levels.
- Initiating a Gap Analysis and document findings. Users can discover exposure risks and weaknesses in security defense that could impact the integrity and availability of ICT systems and services.
- Define risk appetite and tolerance levels. The platform can be used to regularly confirm that the threat detection thresholds that were defined are effective and that related processes are in place to ensure they remain in line with desired tolerance.
- Establish a continuous testing and evolution cadence. Regularly review and optimize the effectiveness of your ICT Risk Management Framework.
Chapter II – ICT-related Incident Management, Classification, and Reporting
Mandatory obligation to report major ICT-related incidents to authorities. This extends to the voluntary reporting of significant cyber threats. To achieve this, organizations will need to establish a comprehensive strategy that encompasses technology, people, and processes for both incidents and cyber threats.
A streamlined process needs to be set to detect, log, and classify all ICT-related incidents with clear information gathering requirements and a documented reporting cadence. Finally, define thresholds for incident classification levels. Criteria could include quantification of affect, duration & downtime, critical services affected, geographic spread and economic impact.
Where Pentera is able to assist:
- Define cyber threat categorization and impact analysis process. This should include the likelihood and business impact of a breach, based on the predicted effect on critical systems and business operations.
- Harmonize and evolve ICT management processes. Regularly review and optimize your ICT-related incident management and reporting processes.
Chapter III – Digital Operational Resilience Testing
This requires a program with a testing schedule that includes various assessments, methodologies, practices, and tools. The program will also require regular testing of ICT-related incident management processes, systems, and response measures.
Where Pentera is able to assist:
- Initiate testing cadence for ICT Risk. Conduct testing for all ICT exposure risks, across all attack surfaces – on prem, cloud and web-facing assets.
- Initiate testing cadence for security defenses. Conduct testing for all security defenses, and threat detection solutions.
- Prepare for Threat-Led Penetration Testing. Have the right tooling to implement a Threat-Led Penetration Testing (TLPT) cadence.
Chapter IV – Management of ICT Third-Party Risk
Measures must be in place for managing risks associated with ICT third-party service providers. Organizations will need to create a register of third-party service providers that includes all outsourced activities, the risk they may pose to digital services and resilience, and which services are deemed critical to the operation of the business. An oversight committee will then need to review the requirements for each ICT-related service provider.
Where Pentera is able to assist:
- Initiate testing cadence for ICT-related third-party risk. Conduct regular testing of ICT related service providers, in line with your ICT risk management framework.
- Harmonize processes and communication with partners. Evolve risk analysis, testing, and communication processes with ICT-related service providers.
Achieving and Exceeding DORA Compliance
DORA compliance is mandatory— but it’s also an opportunity to build long-term resilience in an increasingly complex threat landscape. By using Pentera, your organization is not only supported to meet difficult-to-achieve requirements but also gains a scalable, automated solution that aligns with budget constraints, enhances stakeholder reporting, and supports strategic business goals.
Explore how Pentera can help you achieve and maintain DORA compliance or schedule a demo today to see our platform in action.








