Ransomware targeting Linux machines is becoming increasingly common. While the vast majority of ransomware is still designed to target Windows systems, ransomware groups are modifying their attack arsenal so that they are compatible with Linux OS.
As Linux tends to be the OS for servers and networks which are typically critical infrastructure, the potential damage that can be wrought is devastating, hence the motivation to adapt a ransomware strain to operate on Linux machines. The rise of Linux-based ransomware attacks is an indication that cyber criminals are actively looking for additional strategic attack surfaces to exploit in the aim of finding more weak links. The less susceptible Linux machine may serve that interest, by not getting the same security vigilance as Windows and therefore providing easier security gaps to exploit.
Increasing Prevalence of Ransomware Targeting Linux
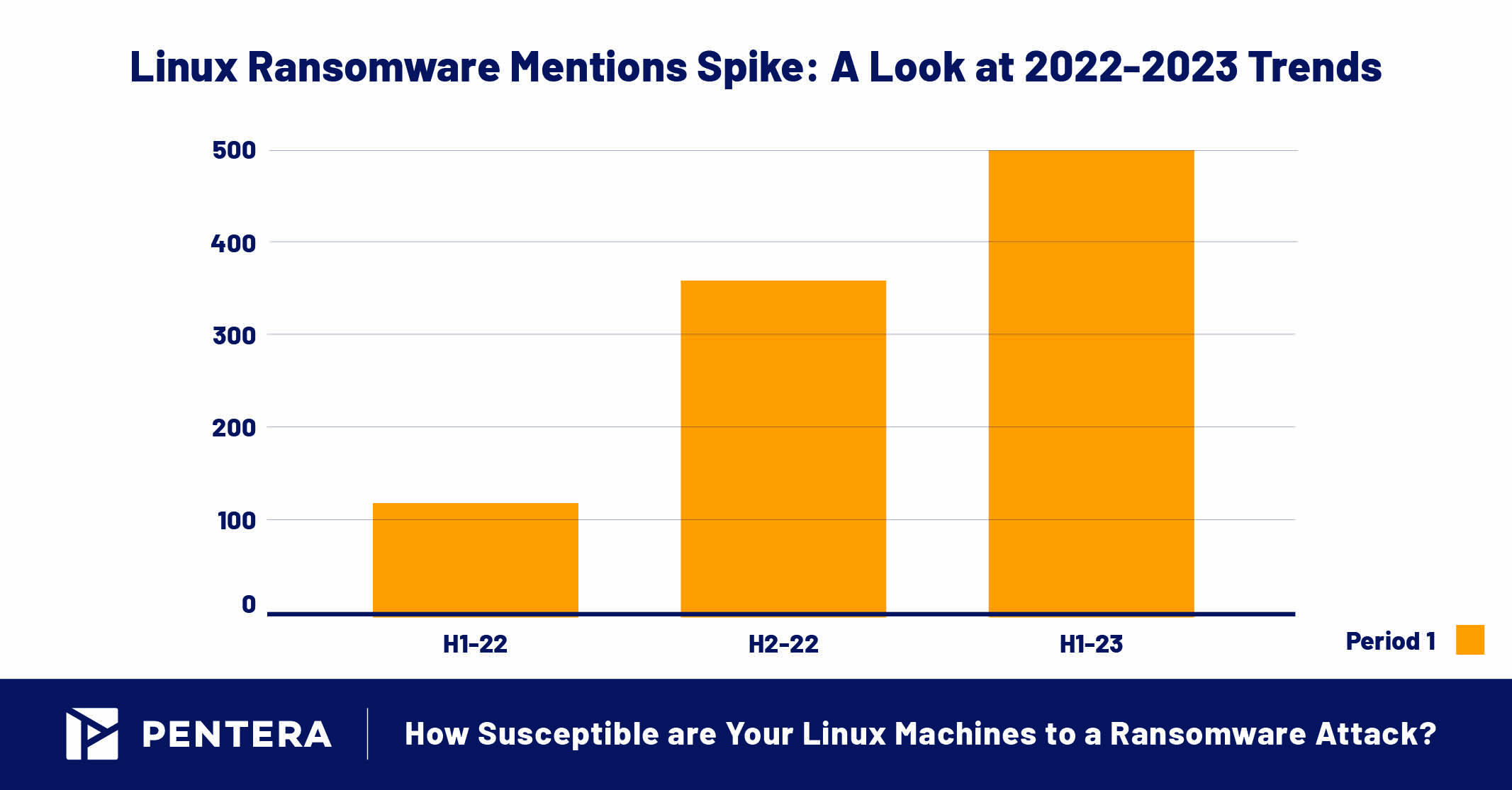
The number of ransomware families targeting Linux has increased dramatically in the last few years. One study found a 75% increase from H1 of 2021 (1,121 detections) to H1 of 2022 (1,961 detections). According to Recorded Future Insikt 2023 Annual Report, threat actors are pivoting their techniques with alarming frequency to attack Linux systems.
In the period between H1 of 2022 to H1 of 2023, references to Linux-targeted attacks increased by four times. While it doesn’t have the active history of ransomware targeting Windows, attackers certainly appear to be making up for lost time.
BlackCat made headlines in 2023 when it attacked numerous corporate networks, such as MGM, NextGen Healthcare, Solar Industries India, Instituto Federal Do Para, Munster Technological University, and Lehigh Valley Health Network. In 2024, it was used to attack Change Healthcare which made a $22 million extortion payment to bring back online their prescription drug services that had been unavailable across the US for weeks.
Similarly, LockBit ransomware has left a large trail of destruction, which in its various forms has been used to execute attacks against more than 2,000 victim organizations including Saint Anthony Children’s Hospital, Boeing, the UK’s Royal Mail service, and the Subway sandwich restaurant chain from which it was successfully extorted more than $120 million in ransomware payments. While temporarily brought down by the UK’s National Crime Agency (NCA), activity by the ransomware group has since been detected, when it posted data from five new victims on its dark website in March 2024.
Unique Ransomware characteristics
Most ransomware targeting Linux are adaptations that were originally designed to target Windows machines. An example of this is LockBit which deployed novel Linux versions of its ransomware variant in a campaign of widespread network intrusions in 2019. They tend to be developed in languages with good cross-platform adaptability, such as Rust and Golang, making them relatively easier to compile for the new OS.
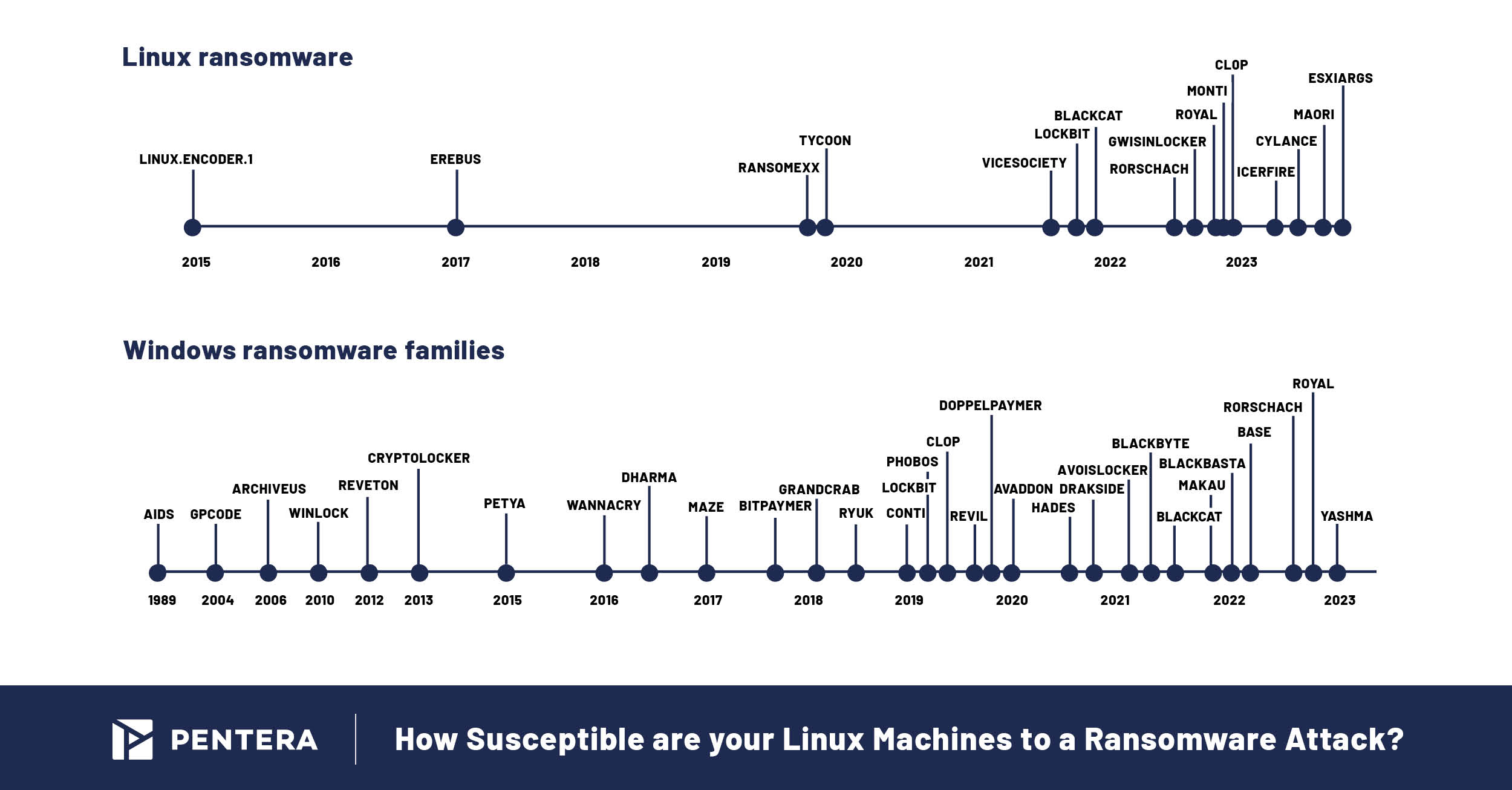
The first ransomware family that was specifically targeted to Linux was first seen in 2015, with the use of Linux.Encoder.1 ransomware. This attack used TTPs that were already highly developed for Windows systems. Oftentimes TTPs don’t translate well on Linux systems, causing them to be forked as they undergo a process of adaptability and refinement for other systems.
When analyzing the commonalities in ransomware families targeting Linux, researchers have found that the payloads they use tend to be stripped back to just bare essentials, possessing only minimal capabilities and content within the binary. In some cases, they’re reduced to just the file encryption code. This leaves the ransomware very dependent on configurations, scripts or command lines within the target environment to gain control and execute actions. An example of this is Cl0p, which only has encryption capabilities, and the only parameter it supports is a path to encrypt.
Content of an encrypted file by iFire
By the nature of having so little internal logic, the ransomware becomes extremely challenging to detect. For example, they don’t possess many of the logic sequences found in malware targeting Windows machines, such as a communication protocol with a server, commands to prepare the system for encryption or creating methods for persistence. The minimalist code replicates and is easily camouflaged amongst the code of other legitimate applications.
Achieving Infection
Getting an initial foothold on Linux machines requires different methodologies and techniques than Windows or macOS, which involve phishing or credential stuffing. Instead, hackers tend to exploit vulnerabilities or web-exposed misconfigurations. One of the most common infection chains for Linux is exploiting a vulnerability in an exposed service hosted on the victim’s server.
The reason for this difference is that Linux machines are not typically used as workstations, where the weakest link is the user; they tend to be deployed on servers running services that are exposed to the Internet. Once these machines are compromised they can be exploited and provide easier lateral access across the organization’s network.
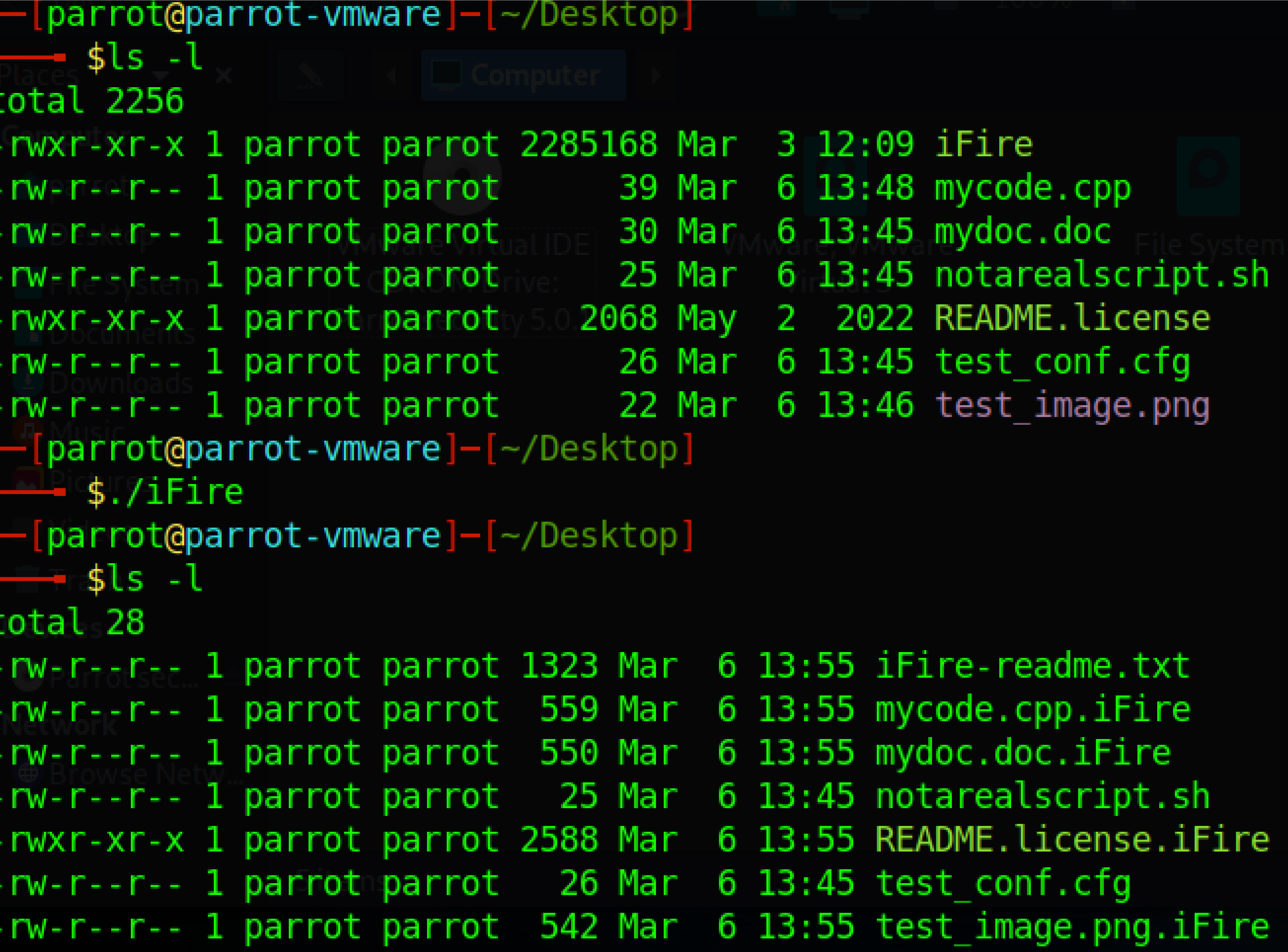
A file listing before and after running the payload
The Kill Chain
Persistence doesn’t figure significantly in ransomware campaigns, as in other types of threats. Once the victim’s files and directories are encrypted, any further execution in the system is pointless. Yet, in the real world, threat actors are motivated to not limit encryption to a single computer but to spread it to others, and bit by bit, infect the entire infrastructure.
Attackers are likely to pivot their techniques to identifying the security strengths and weaknesses of the target environment. After compromising the exposed service, the kill chain tends to involve the deployment of a webshell which is used to take control of the target server.
Webshells function as backdoors, enabling threat actors to maintain access to compromised servers even after they are rebooted. When servers are accessed through lateral movement during a complex attack, persistence is often achieved by creating new user accounts or exfiltrating the server’s credentials. This allows attackers to retain access through legitimate services like SSH. It is rare for ransomware to employ multiple persistence methods. Typically, the vulnerable server is encrypted immediately and then deletes itself post-execution, as observed with ransomware like LockBit and BlackCat.
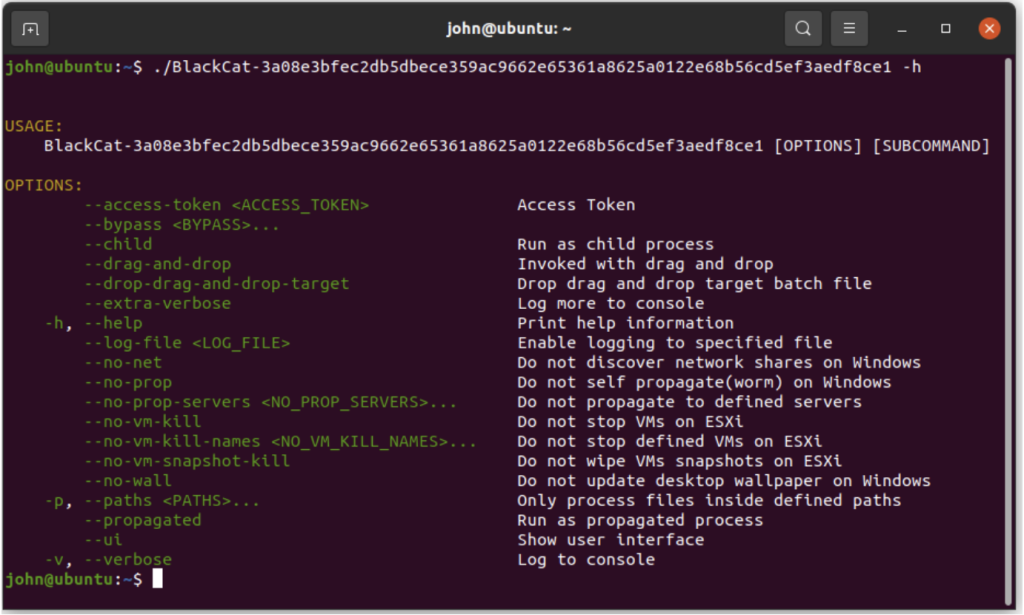
The help parameters called by a BlackCat ransomware attack
Getting Ahead of the Linux Kill Chain
Many of the different ransomware families, be they LockBit, BlackCat or others like Cl0p and Maori tend to share many of the same TTPs, programming languages, and technologies. While variation is noted in new techniques, showing a degree of evolution as hackers try to refine the stealthiness and pervasiveness of their attacks, well-known, proven actions are never totally abandoned. The predictability of attacker behavior makes it possible to anticipate an attack and put in the necessary safeguards to prevent breaches.
Tools supporting CTEM (Continuous Threat Exposure Management) allow security teams to assess their organization’s exposure to ransomware threats, and determine the true risk of each exposure to effectively prioritize remediations. To test the effectiveness of the remediation, security teams run an emulated ransomware attack to validate that implemented fixes have worked.
Pentera’s RansomwareReady is one such solution. It emulates entire ransomware campaigns against the organization’s in-production environment. Doing far more than a vulnerability assessment, the platform emulates many of the most destructive ransomware strains on both Windows and Linux, including Maze, REvil, Conti, LockBit 2.0, and Lockbit 3.0.
Assuming an initial foothold within the network, Pentera safely runs ransomware TTPs, attempting to complete full attack kill-chains. The platform’s algorithms cover an entire attack operation including injection of malicious scripts, exploiting the payload, encrypting data, and exfiltration to a C2 server.
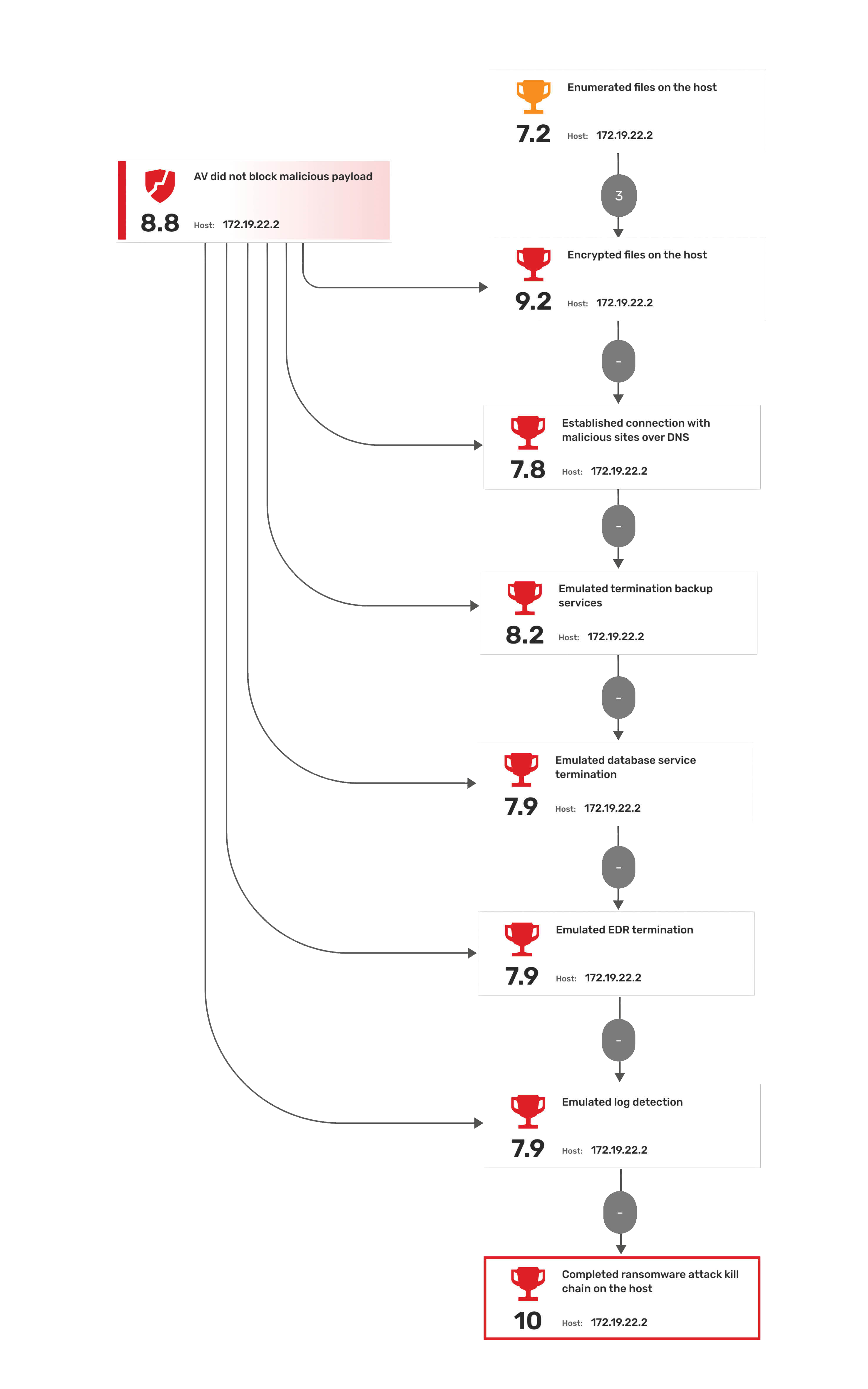
Attack path for LockBit 3.0
In the process of conducting the emulated attack, RansomwareReady can also be used to assess the effectiveness of detection and response security policies and tools.
Finally, security teams are provided with a prioritized step-by-step guide for remediating the exposures so that the process to harden security and ensure organizations are ransomware-ready is clear and easy to implement.
As hackers are broadening their range of TTPs and diversifying their targets across different endpoints and operating systems, enterprises need to make sure that their infrastructure is holistically ready to stop these breaches from happening. Defenders can not afford to fall behind in this race towards ransomware resilience, they need to broaden their scope of what they’re equipped to protect and then validate that it’s indeed working.
Ready for ransomware resilience? Put your Linux systems to the test with Pentera and stay secure.