True Story, Verbatim
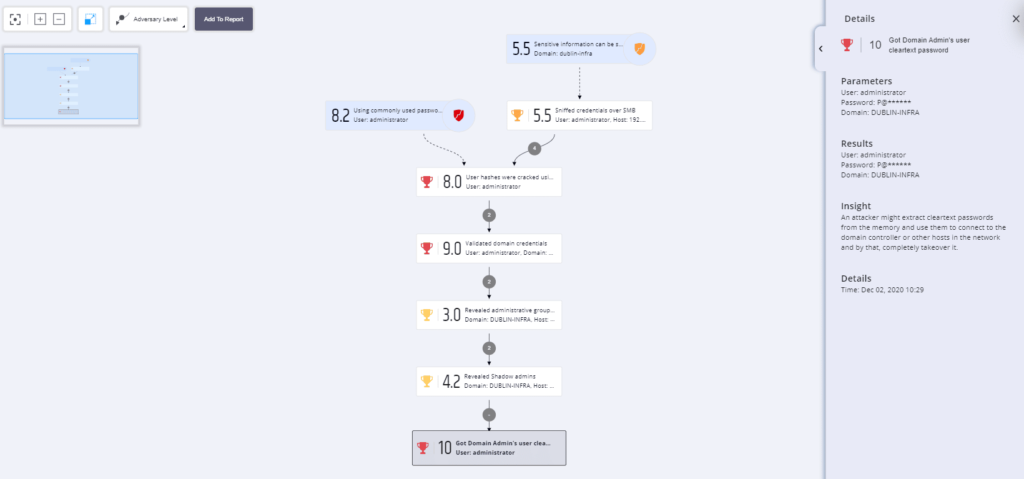
“Let’s stop the test here, and continue tomorrow,” came unexpectedly from the CISO of a multi-billion technology company as the PenTera platform exposed the company’s Git source code repository. “In a few minutes, this software showed us that our entire IP and source code can be reached by nefarious hands.”
Indeed within minutes (18 min and 21 seconds to be exact), a new attack vector discovered managed to compromise the admin’s password, available in free-text format. “It’s ‘all hands on deck’ until we plug this loophole. No one is going home ‘til we do,” the CISO continued while elevating the organization’s risk level, grasping the full business impact and potential disruption of this critically identified vulnerability.
Later the CISO said when discussing with the Pcysys team, “I’m sorry the POV is going to extend to two days but I just can’t live with this situation once I’ve seen it evolve with my own eyes on your attack vector display. I’m not going to let anyone gut our GIT.”
As additional details regarding the SolarWinds supply chain attack unfold, the above true story reminded me how much continuous testing of our complete attack surface (the one we are aware of and the one we are not) is absolutely critical.
Breach Recap
In the current breach making news, the adversaries gained access to the SolarWinds source code. These malicious actors inserted a single, digitally signed, malicious DLL file – SolarWinds.Orion.Core.BusinessLayer.dll – which once loaded provided a local admin access backdoor capable of generating SAML tokens for seamless authentication and unlimited access across the organization’s infrastructure. All while performing an extensive list of checks to evade discovery and C2 communication detection. Just a few innocent-looking, yet deadly, lines of code amongst millions of them.
For many organizations, their Git is their crown jewel, and if maliciously accessed or tampered with, havoc can ensue. Internally to the organization’s own elevated business risk, or like in the case of SolarWinds where you are part of the supply chain, eventually opening that same backdoor everywhere the software is used.
So how do you protect yourself against this type of attack? Illicit access to your code repository? Modification or insertion of benign-lookalike lines of code?
Back to Basics
There is no doubt that the source code repository in a software company is the ultimate target for hackers that are after a supply chain attack. But the issue is that the attack vectors leading to it are rarely tested.
MFA alone at the gate will not suffice and – even if you add to your CI/CD cycle an array of SecDevOps application security tools (SAST, DAST, IAST, and RASP), those will not be able to detect an attack easily if it is performed with legitimate privilege gained by lateral movement takeover of one of your development workstations. That is because once your infrastructure is “owned,” the legitimate programmer remote access cannot be distinguished from wrongful programmer access. The battle has to ‘shift left’ in the attack stages to make sure your infrastructure is resilient to wrongful access, lateral movement, credential takeover, and privilege escalation.
The Missing Attack Vector Testing Towards your R&D environments
To assure IT and development environment integrity, whether on-premises or in the cloud, every organization requires continuous and rigorous penetration testing across their entire attack surface towards your GIT and development CI/CD environments. That is impossible today with manual penetration testing services, but a no-brainer when employing automated penetration testing software. A daily pen test can provide assurance that your R&D environment is resilient to attackers gaining a foothold in the first place.
Pcysys developed PenTera, a modern security pen-testing platform that assures that you are resilient to the breadth and depth of attacks, helping you recognize and stop the breach before any material damage is done. Ask a Pcysys expert or schedule a demo to see for yourself how you can test and validate that your infrastructure is safe against supply chain attacks.