Cloud computing has fundamentally changed how we operate. It’s efficient and scalable, but it’s not without some problems. Security is the biggest. As we’ve shifted to the cloud, we’ve exposed ourselves to new risks that can’t be ignored.
Cloud Security Risks: A Growing Challenge
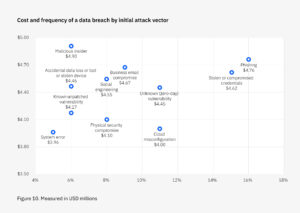
The IBM Cost of a Data Breach 2023 Report points out that 11% of breaches are due to cloud misconfigurations. Cloud’s complexity and vast reach make it a magnet for attacks, with its complicated architectures of interconnected services and identities. Combine this with the human element – our slips in setting up and managing cloud systems – and there comes trouble. It’s easy to assume it’s okay to use default settings or that we’ll remember to revoke that temporary access, but even one slip can have massive consequences.
Addressing these challenges requires a proactive approach that goes beyond traditional security measures. Implementing cloud security stress testing ensures organizations can identify real-world risks before they are exploited.
Source: IBM Cost of a Data Breach 2023 Report
Pentera Cloud: Closing the Security Gap
At Pentera, dealing with these risks isn’t just part of the job—it is the job. The truth is, as our reliance on cloud services has grown, so has our exposure to threats. This isn’t about IT; it’s about the future of our operations, our data, and our company’s integrity.
Pentera Cloud was born out of necessity. We needed a way to see our true cloud security gaps clearly and fix them before they were exploited.
That’s why we’ve extended our Automated Security Validation offering to the cloud.
Pentera Cloud represents a significant advancement in our mission, offering a solution specifically designed to validate the complexities of cloud-native security. Through automated penetration testing, we provide organizations the means to effectively identify and address security flaws, ensuring their cloud environments are secure and resilient.
How Cloud Pentesting Complements CSPM
By offering a proactive way to identify and mitigate potential security threats, cloud pentesting complements Cloud Security Posture Management (CSPM). Unlike CSPM, which primarily focuses on configuration and compliance management, pentesting delves deeper, emulating real-world attacks to exploit vulnerabilities that may or may not be flagged by CSPM products. In the on-prem world, we know that marking a vulnerability as ‘critical’ doesn’t necessarily mean it is critical in your unique environment. It depends on the context and on whether or not that vulnerability can actually be exploited and lead the attacker to your crown jewels. This logic equally applies to cloud native vulnerabilities.
Pentera Cloud starts where CSPM ends, addressing the famous alert fatigue which Vulnerability Management products have become so famous for.
The Complexity of Cloud Pentesting
For the past 24 months, as the category leader, we have built a product that accurately mimics the attacker’s mindset to identify real threats beyond misconfigurations.
Pentesting the cloud is a speciality. The complexity of cloud environments requires a deep understanding of the architecture – a skill very few pentesters possess. AWS and Azure, for example, have their own rules of what constitutes a penetration test. Add to that the fact that hacking and testing of cloud-native environments is different from the good old Windows-based on-premises networks.
Bridging the Gap Between On-Prem and Cloud Security
Many companies operate in a hybrid mode, integrating their corporate on-premises network with their multi-cloud environments. With Pentera Cloud, knowing true security gaps is made possible, regardless of where they originated from. On our way to 360° attack surface coverage, the cloud attack surface was a missing piece. It represented a promise we made both to our customers and to ourselves. Our ability to expose attack vectors that switch between on-prem corporate networks and cloud environments will contribute immensely to keeping an organization’s cyber resilience strong.
Having the first cloud-native pentesting product in the cybersecurity space is an honor for us. Adding Pentera Cloud to our Automated Security Validation Platform reinforces the ability of our platform to validate the cybersecurity resilience of your on-premises networks, infrastructure, and publicly accessible attack surfaces.
The future is undoubtedly in the cloud, but it must be a secure future. We’re committed to making that happen and driving innovation in security validation to defend against the threats of today and tomorrow.
Let’s remove assumptions and validate our cloud security every day, from the attacker’s perspective.
The future of our digital world depends on it.
Pentera Cloud is available now. Click here to learn more and watch on-demand webinar on Pentera Cloud..
Frequently asked questions
How do you validate security in a cloud environment?
Cloud security validation involves automated testing, penetration testing, and continuous security validation to assess potential vulnerabilities. Solutions like Pentera Cloud provide real-world attack emulation to uncover security gaps in cloud configurations, identity management, and network security.
What is validation in cloud computing?
Validation in cloud computing ensures that security measures are properly implemented and effective. This includes: Configuration validation (checking IAM roles, policies, and permissions), compliance validation (aligning with frameworks like SOC 2, NIST, ISO 27001), threat validation (simulating real-world attack scenarios to assess resilience)
How is cloud security validated?
Organizations can validate cloud security by leveraging: 1. Cloud security posture management (CSPM) for misconfiguration detection 2. Cloud penetration testing to emulate attacks 3. Continuous Security Validation to test security against emerging threats.
What is the difference between authentication and validation in cloud security?
Authentication verifies who you are (e.g., login credentials, MFA). Validation ensures security controls are working as expected (e.g., testing if IAM policies prevent unauthorized access).
How do you audit cloud security?
Cloud security audits involve: Assessing IAM configurations, checking logging and monitoring settings, running security validation tools to test resilience, reviewing compliance with frameworks like CSA STAR and NIST.