Ivanti Ground Zero
On January 10, 2024, Ivanti disclosed two vulnerabilities, CVE-2023-46805 and CVE-2024-21887, impacting its Ivanti Connect Secure and Ivanti Policy Secure products in supported versions (9.x and 22.x). Successful exploitation can result in authentication bypass and command injection, leading to unauthenticated remote code execution and lateral movement inside the victim’s network.
Then on January 31, 2024 Ivanti disclosed two more vulnerabilities that were discovered while investigating the previous two flaws: a privilege escalation vulnerability tracked as CVE-2024-21888 and a Server-Side Request Forgery (SSRF) in the SAML component CVE-2024-21893. The latter can allow attackers to access restricted resources without authentication and was also exploited as a zero-day. “We have no evidence of customers being impacted by CVE-2024-21888 at this time, and we are aware of a limited number of customers impacted by CVE-2024-21893,” the company said. Exploitation is expected to rise, however: “Ivanti expects the threat actor to change their behavior and we expect a sharp increase in exploitation.”
Mitigation was introduced on February 1, 2024 where fixed versions were made available for all impacted products. However, the US Cybersecurity and Infrastructure Security Agency (CISA) issued a directive to all federal agencies to disconnect the impacted Ivanti products from their networks by end of Friday, February 2, 2024 and perform additional forensic analysis and clean-up steps in case they’ve already been compromised.
In this blog, we explain how adversaries exploit the Ivanti CVE-2023-46805 and CVE-2024-21887 vulnerabilities. We then show how security teams can use Pentera to determine their organizations’ risk exposure resulting from these CVEs and what remediation or mitigation actions they need to take.
Test your security readiness against Ivanti zero-days with a free Pentera assessment
Why the Ivanti Vulnerabilities Matter
The recent discovery of two critical vulnerabilities in Ivanti’s security suite – CVE-2023-46805 and CVE-2024-21887 – has sent ripples through the cybersecurity landscape. Ivanti Connect Secure and Ivanti Policy Secure, affected by these issues, play crucial roles in securing corporate data and controlling network access. Their compromise exposes both external and internal assets, further complicating mitigation and remediation efforts.
The two vulnerabilities announced earlier this month, tracked as CVE-2023-46805 and CVE-2024-21887, allow threat actors to establish persistent system access and move laterally across a target network while performing data exfiltration operations. At the heart of the problem is the dual functionality of the affected Ivanti products. Ivanti Connect Secure facilitates employee access to critical resources from a range of external devices, while Ivanti Policy Secure serves as a Network Access Control (NAC) solution, granting internal network access solely to authorized devices and users.
With vulnerabilities present across both systems, attackers can exploit them to gain unauthorized access from outside the organization to its internal network. This situation presents a dual risk: externally, through compromised access, and internally, by circumventing controls designed to protect the network from unauthorized access. This combination of vulnerabilities highlights the need for continuous security control validation that covers both external entry points and internal network access controls, ensuring existing protections are effective against such complex threats.
Testing the Impact of the Ivanti Vulnerabilities with Pentera
To grasp the real-world impact of the Ivanti vulnerabilities, it’s crucial to assess not only their exploitability but also the actions an attacker could undertake to propagate an attack and compromise sensitive resources post-exploitation. Pentera does just this, in a fully automated manner, on-demand across an organization’s entire infrastructure. The Pentera Platform automatically uncovers real exposure in the organization’s environment, challenging the complete IT attack surface—including internal, external, and cloud components—by safely emulating attacker behavior, to deliver real-time security validation at scale.
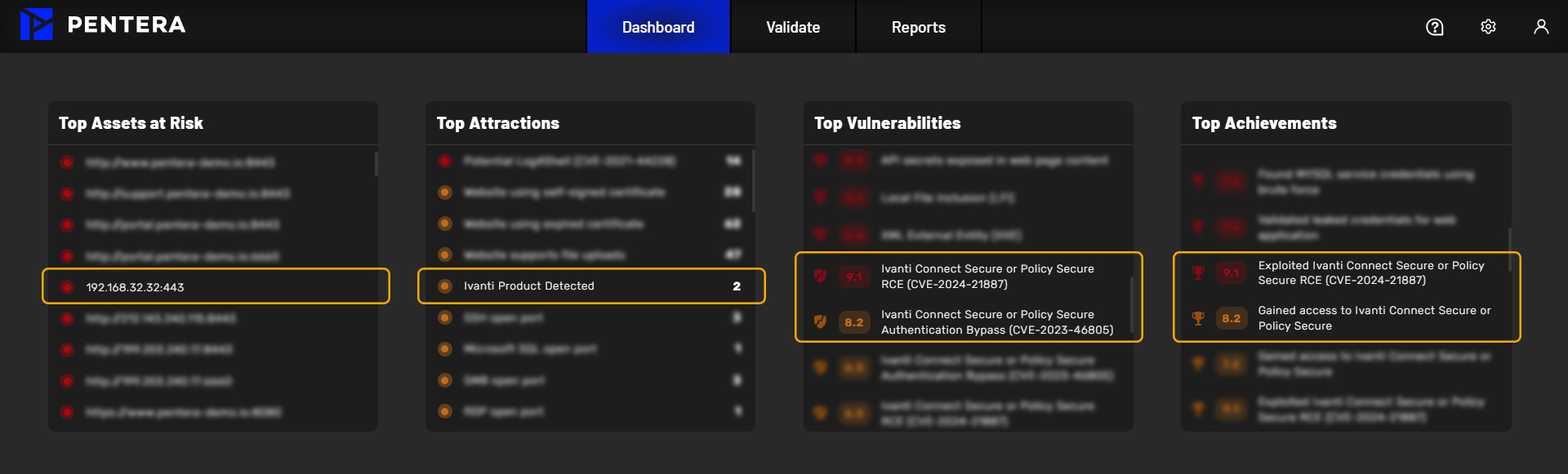
To identify the impact of CVE 2023-46805 and CVE-2024-21887, Pentera starts with the discovery of the organization’s digital estate. As seen in image 1 below, Pentera discovered an Ivanti product and effectively exploited the two vulnerabilities, enabling remote code execution on the targeted host machine.
Yet, the demonstration of successful exploitation marks only the beginning. Attackers don’t stop at exploitation – they double down, unleashing sophisticated attacks.
Bearing this in mind, Pentera extends automation to post-exploitation testing, demonstrating how an attacker will propagate their attack after gaining an initial foothold in the network. This encompasses the execution of advanced Tactics, Techniques, and Procedures (TTPs):
- Remote Code Execution (RCE) and Defense Evasion: Pentera executes code remotely on a system while employing defense evasion strategies to circumvent antivirus (AV) and endpoint detection and response (EDR) systems.
- Privilege Escalation: Pentera uses multiple techniques to attempt a transition from low-privilege user access to elevated privileges.
- C&C Communication: After establishing a Command & Control (C&C) channel, Pentera tests the ability of an attacker to use it, by mimicking C&C communications.
- Data Exfiltration: To achieve unauthorized data transfer from a network to an attacker-controlled location, Pentera emulates exfiltration techniques.
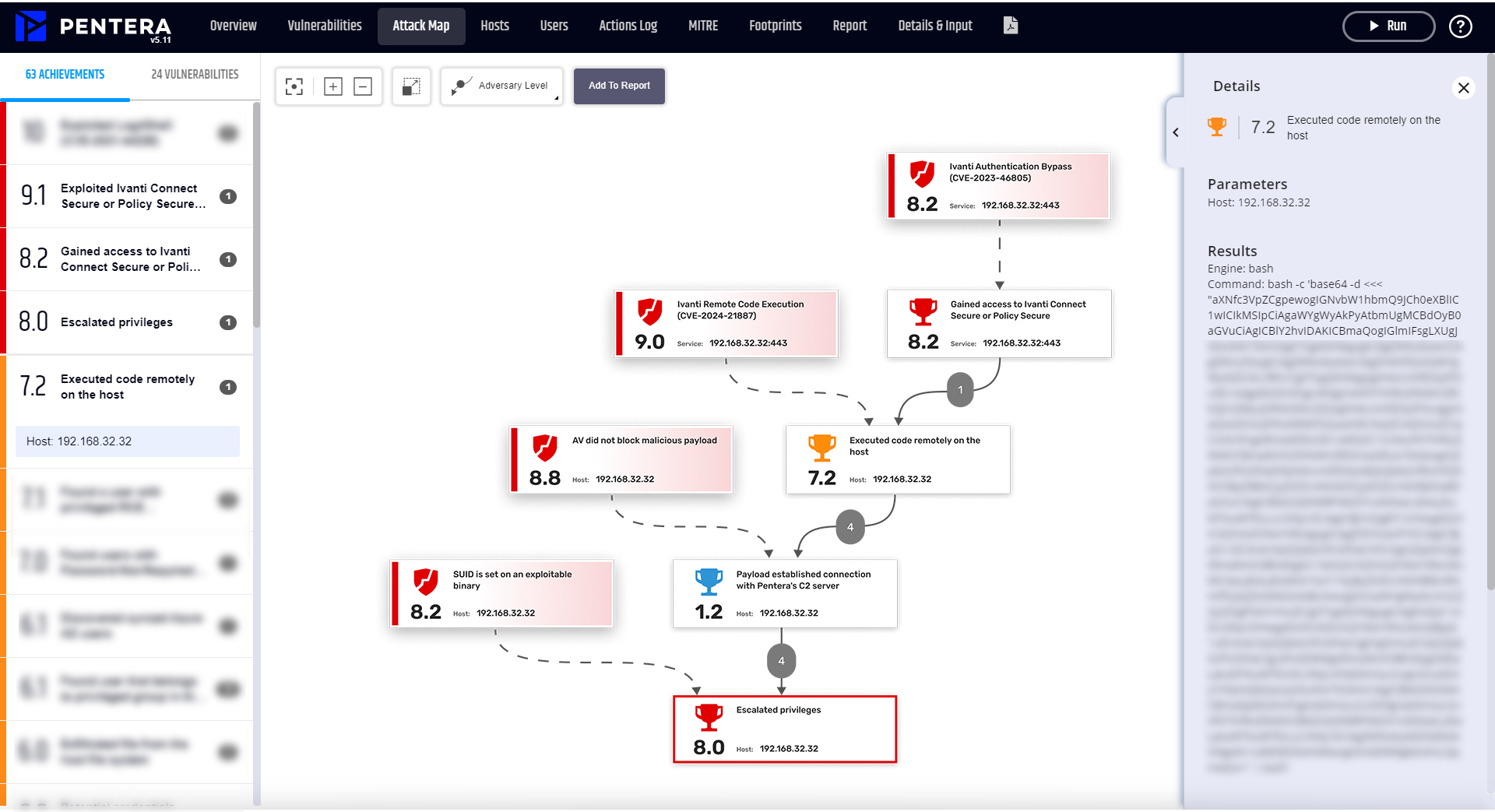
Image 2 illustrates Pentera’s achievement of a full attack kill-chain that exploits the two Ivanti CVEs.
- The root cause of the attack is exploitation of the Ivanti Authentication Bypass vulnerability which allows access to the host.
- The attack then exploits the RCE vulnerability to execute code remotely on the host, initiating contact with the Command and Control (C&C) Server for a malicious executable download.
- Pentera emulates various adversary tactics to reinforce the foothold on the network, leveraging local privilege escalation, to intensify potential damage.
Conclusion & Recommendations
Organizations using Ivanti’s products should heed the recommended mitigations and stay informed about patch releases. We recommend following the guidance outlined in the Ivanti blog post on this activity. Ivanti customers are urged to implement mitigation as soon as possible and to follow the post for upcoming patch release schedules. Ivanti recommends customers awaiting patches to apply the mitigation, run the external Ivanti’s Integrity Checker Tool (ICT) to check for evidence of exploitation.
For Pentera customers – look for findings in your upcoming security validation test runs indicating that CVE 2023-46805 and CVE-2024-21887 were found and proven exploitable in your network. We also recommend running a follow-up test if you see such findings, to validate that any mitigation or remediation steps taken are effective.
Get your Pentera security readiness assessment to identify exposure and test your defenses against the Ivanti vulnerabilities.