Ransomware isn’t just a security issue; it’s a business problem that’s grown too big to ignore. What started as floppy-disk attacks back in the 1980s has now evolved into something far more dangerous— Ransomware-as-a-Service (RaaS).
RaaS has fundamentally changed the ransomware landscape. Now, attackers no longer need to be malware experts. With RaaS, launching an attack has become accessible to those without deep technical expertise, making ransomware an even more pervasive threat. Cybercriminals simply subscribe to a service, much like using a software platform. The ease of access has dramatically increased the frequency and severity of ransomware attacks, as more attackers jump on the opportunity to launch attacks without needing advanced technical knowledge.
The Evolution of Ransomware: From Scareware to a Full-Fledged Criminal Enterprise
Ransomware has come a long way. What started as locker ransomware—locking users out of their computers—has turned into a multi-billion-dollar criminal industry. Today’s ransomware isn’t just about locking your data; it’s about double extortion, where they take your files and threaten to leak them, or even triple extortion, where they go after your partners and customers too.
Worse, Ransomware-as-a-Service has transformed ransomware into a widespread, highly accessible threat, fueling a rise in attacks and putting more organizations at risk. RaaS has created a marketplace where cybercriminals collaborate for nefarious gains, intensifying the threat and keeping security professionals on constant alert.
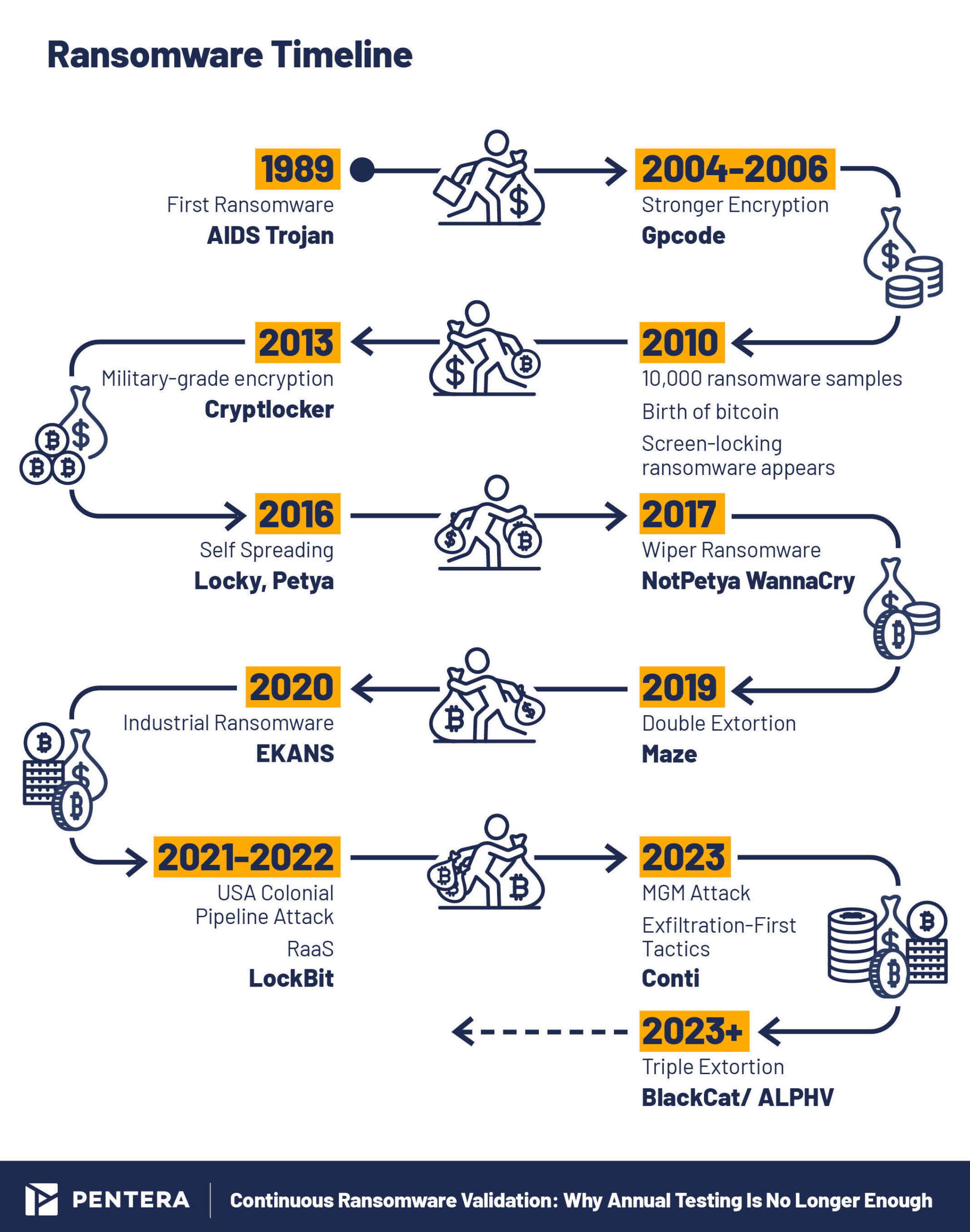
Key moments in ransomware’s evolution.
For example, the 2017 WannaCry ransomware attack caused widespread damage, impacting over 200,000 computers across 150 countries. This attack exploited vulnerabilities in the widely used SMB protocol, allowing it to spread rapidly and cause extensive damage. Today, continuous validation is the only way to ensure these vulnerabilities are discovered before attackers exploit them.
If your organization is only relying on backups to mitigate ransomware, you’re underestimating how serious it’s become.. You’re also leaving your business vulnerable. It’s not just about being “ready” anymore; it’s about staying ready with automated ransomware defense testing and real-time ransomware testing strategies.
Three Stages of a Ransomware Attack: What You Need to Know
A ransomware attack doesn’t happen all at once. It follows three distinct stages:
- Pre-Encryption: Before encryption starts, attackers prepare the environment. To prevent file recovery, they delete shadow copies, create mutexes to make sure the ransomware runs without interference, or inject their malware into trusted processes to stay hidden. These early moves—known as Indicators of Compromise (IOCs)—are your first warning signs that something’s wrong.
- Encryption: Once everything is set, the ransomware gets put to work, encrypting your files. Some ransomware attacks happen quickly, locking you out in minutes , others operate more covertly, carefully evading detection by security tools until encryption is complete.
- Post-Encryption: After the encryption is complete, the attackers leave you a ransom note, making their demands clear, either plastered across your screen or buried in your files. They’ll demand payment, usually in cryptocurrency, and monitor your response through their command and control channels.
If you’re not sensitive to the IoCs that occur at each of these stages, you’re leaving yourself open to serious disruption. That’s why you need continuous ransomware validation to spot these indicators before an attack can fully unfold.
Indicators of Compromise (IOCs): The Early Warning Signs
One of the most important steps in defending against ransomware is recognizing the Indicators of Compromise (IOCs) before the attack fully takes root. If you’re seeing shadow copy deletions or process injections, you’re already in the pre-encryption phase.. Here are some examples to watch for:
- Shadow copy deletion: This is an early move by attackers to make sure you can’t restore your files later.
- Mutex creation: Mutexes prevent multiple ransomware instances from running on the same machine, making sure the attack runs smoothly.
- Process injection: Where Ransomware is inject into trusted processes, hiding within your system’s legitimate operations to avoid detection.
- Service termination: Attackers might kill off your security services, like EDR or antivirus software, to ensure they’re not interrupted.
IOCs like shadow copy deletion or process injection can often go unnoticed. A SOC equipped with advanced detection tools can identify these early signs, allowing organizations to mitigate the attack before it escalates. With continuous ransomware validation, these signs can be caught in real-time, giving defenders the upper hand.
Why Annual Testing Falls Short
Here’s the uncomfortable truth: testing your defenses once a year doesn’t cut it. If you’re testing annually, you’re leaving yourself exposed for the other 364 days of the year. Ransomware evolves constantly, and by the time you run your next test, the threat could have morphed into something your system isn’t prepared to handle.
That’s why you need real-time ransomware testing strategies. With automated ransomware defense testing, you’re always, validating that your environment will hold-up in the face of an attack. You can’t afford to assume you’re secure; you have to prove it, and you have to do it often.
There is the perception that continuous ransomware validations costly or time-consuming. However, with the rise of automated testing platforms, continuous validation can be integrated smoothly into your security workflow, without much additional overhead. Not only does this reduce the burden on IT teams, but it also ensures that your defenses are up-to-date with the latest threats.
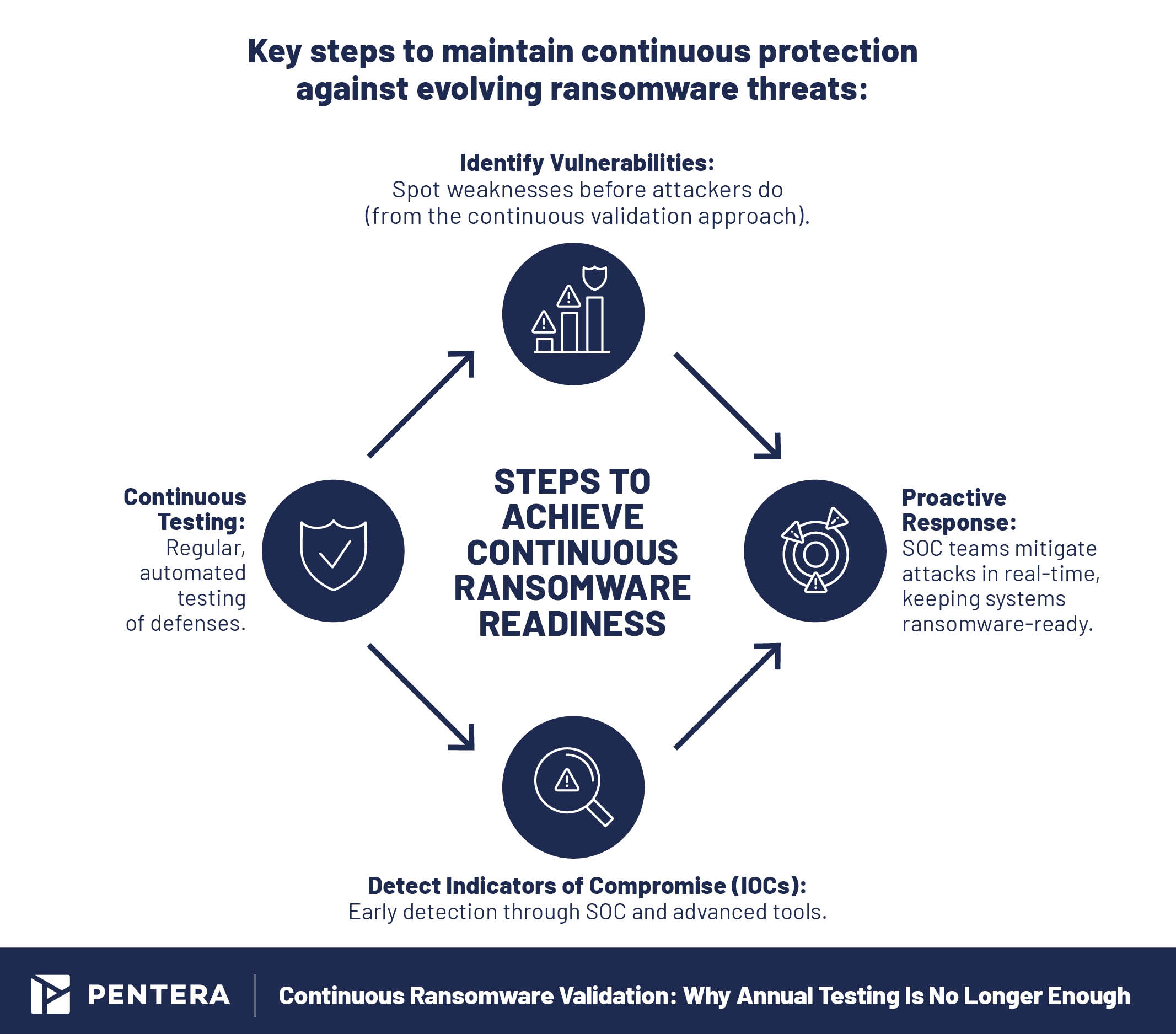
Key steps to maintain continuous protection against evolving ransomware threats.
Building a Ransomware-Ready Organization: It’s About Hygiene
Think about security like hygiene. You don’t brush your teeth once a year and call it good. You do it daily to protect yourself. It’s the same with validating against ransomware, you can’t test once and assume everything’s fine. You need to validate your defenses continuously, finding gaps and fixing them before attackers exploit them.
If you’re not testing frequently, you’re not ransomware ready. You need a mindset that emphasizes continuous validation and regular testing. This isn’t a one-time task—it’s a hygiene habit that needs to be built into your routine.
A well-functioning SOC is the backbone of any ransomware defense strategy. SOC teams are responsible for not just detecting attacks but analyzing and responding to them in real-time. The organization can feel confident in its ransomware readiness and resilience with a proactive SOC actively responding to threats.
The Practical Takeaway: Don’t Assume, Validate
Here’s the bottom line: don’t assume you’re ready—validate it. If you’re relying on backups or annual tests, you’re not prepared. Ransomware is evolving every day, and the only way to stay ahead is through continuous ransomware validation.
To learn more about how continuous ransomware validation can protect your organization, visit our RansomwareReady™ page.