What Happened During the LockBit Attack?
On April 13, 2023, we were hit hard. The University of Health Sciences and Pharmacy (UHSP) faced a serious adversary: The notorious LockBit ransomware group. It brought our operations to a screeching halt and thrusted us into a battle for our data and systems. This wasn’t just a cyberattack; it was a reality check that revealed both vulnerabilities and strengths we never fully appreciated until we were in the thick of it. Strengthening ransomware preparedness could have made all the difference.
You might wonder, “If LockBit was so notorious, why weren’t we better prepared?” The truth is, the cybersecurity community has been conditioned to treat cyberattacks as a mark of shame—something to conceal rather than discuss. This culture of silence deprived us of the insights needed to prepare adequately against a ransomware attack.
We must change this mindset. Cyberattacks shouldn’t be seen as blemishes on our reputations; they’re critical experiences to share for better industry preparedness. Transparency is key. By telling our story, I hope to shed light on the realities of a ransomware attack and the importance of cybersecurity readiness.
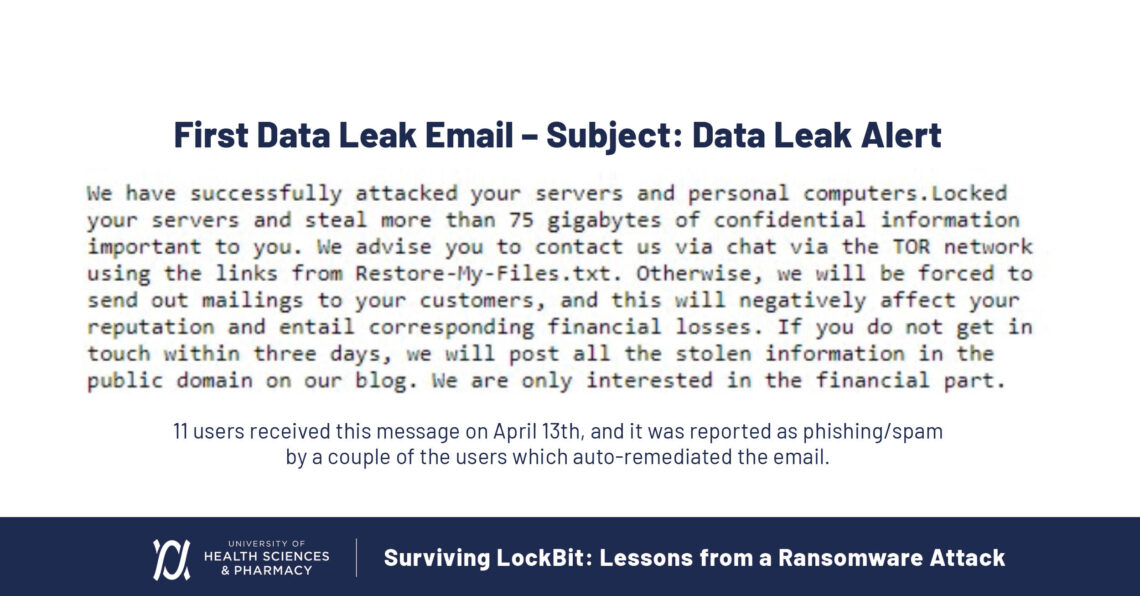
LockBit ransomware demands in the first data leak email to UHSP.
The LockBit Ransomware Attack: A Day-by-Day Breakdown
April 13th: Identification and Initial Signs of the Attack
It started on the morning of April 13th. At 4:30 am, I got the call: our onsite servers and services were down. By 6:30 am, everything was down. At 7:00 am, not yet knowing the origin of the attack path, we began disaster recovery procedures. Later on, we discovered that eleven of our users received an email saying we’d been attacked and that 75GB of our data had been stolen. No one reported these emails.
Underlying Vulnerabilities
To understand how we found ourselves in this situation, I’ll first review the background factors that contributed to our vulnerability. Our infrastructure was largely end-of-life, with servers and firewall equipment overdue for replacement. Although we had placed orders for new hardware, the supply chain disruptions caused by COVID had delayed their arrival. We were caught in a transitional phase, having started a cloud migration to move critical systems to Azure, but many key components were still running on outdated equipment.
Additionally, because our firewall was at end of life and supply chain problems persisted, we partnered with a local cloud service provider for a temporary solution. Unfortunately, this arrangement did not support multi-factor authentication (MFA) for our VPN, leaving a critical security gap. Despite our SaaS-first approach—intended to ensure most applications were more secure in the cloud—these compounding issues left us exposed.
April 14th to 23rd: Containment
By the 17th, we believed this was merely a hardware failure and managed to get 95% of our campus operational again. On April 20th, the server environment crashed once more. This time, it refused to come back online, and we realized this wasn’t just a case of failing hardware.
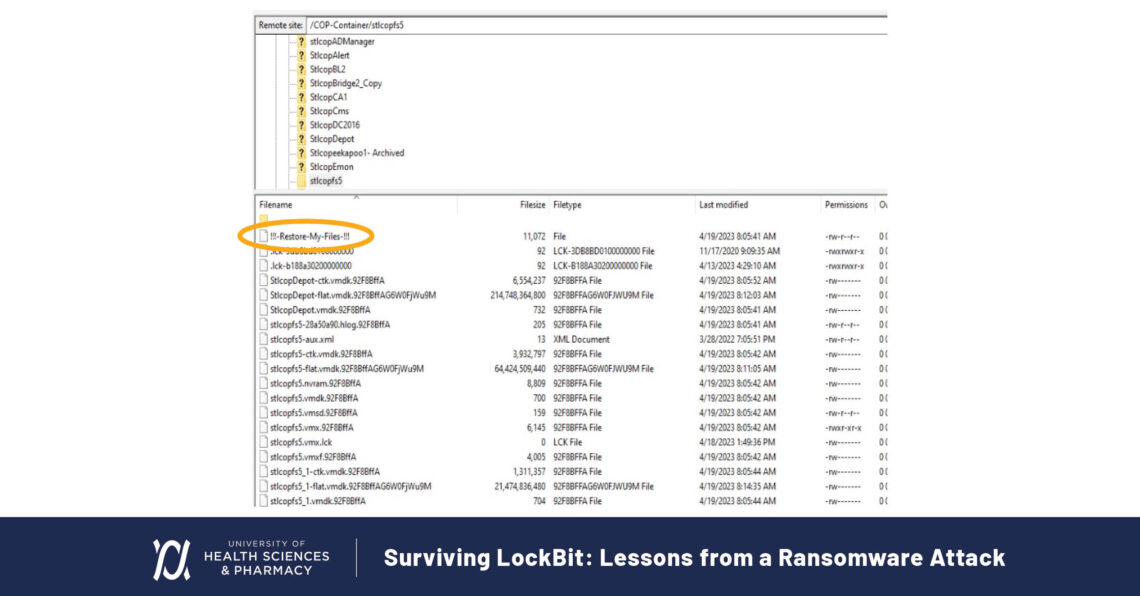
On April 21st, we found a ransomware note on the root of the hypervisor hardware, confirming the attack. At that point, we halted recovery operations, updated leadership, and switched to our incident response plan. The next day, after notifying the FBI, CISA, and our cyber insurance provider, I met with outside counsel. Incident response teams arrived, and negotiations with the threat actor began.
While recovering from the incident and reviewing logs, we discovered that the attackers used a weak password to compromise a user service account. They accessed our systems through an unsecured VPN. Identifying weaknesses in your infrastructure is essential to avoiding similar outcomes. They used lateral movement to reach our server segment, extracting high-level credentials and escalating their privileges to access our hypervisor and exfiltrate our data.
Throughout our recovery process, they continued moving through our environment. They located and wiped our secondary backup location, then created backdoor accounts to regain access. Our EDR systems missed these moves because they don’t run on the hypervisor OS level.
Key Milestones in Our Recovery
April 24th to June 2nd: Recovery
LockBit supplied two partial lists showing 5% of the exfiltrated file names and initially demanded $1.25 million, claiming they had 175 GB of our data.
We learned that some PII resided on a compromised server hosting our local password manager. This helped attackers escalate their privileges. At some point, LockBit apparently notified the Department of Education, presumably to pressure us. We conferred with the department and informed our campus.
During recovery, backups became a major hurdle. Our primary backups relied on AD authentication, which had been encrypted by the attackers, rendering them inaccessible.
Fortunately, we reached our tertiary backups, which were not connected to our environment. We also kept certain passwords on paper in a physical safe in another building. Having a hard copy of our incident response plan was invaluable, because it outlined the order of restoration for critical systems. Together with our tertiary backups, that allowed us to restore directly to Azure. From the University’s esports athletic division, we borrowed a gaming PC to restore the AD until new hardware arrived.
By June 2nd, we had recovered nearly 100% of our systems, though we still weren’t entirely sure what data had been lost or stolen.
Restore-My-Files note left by LockBit ransomware on UHSP servers.
June 6th-June 14th: Landing & Data Drop
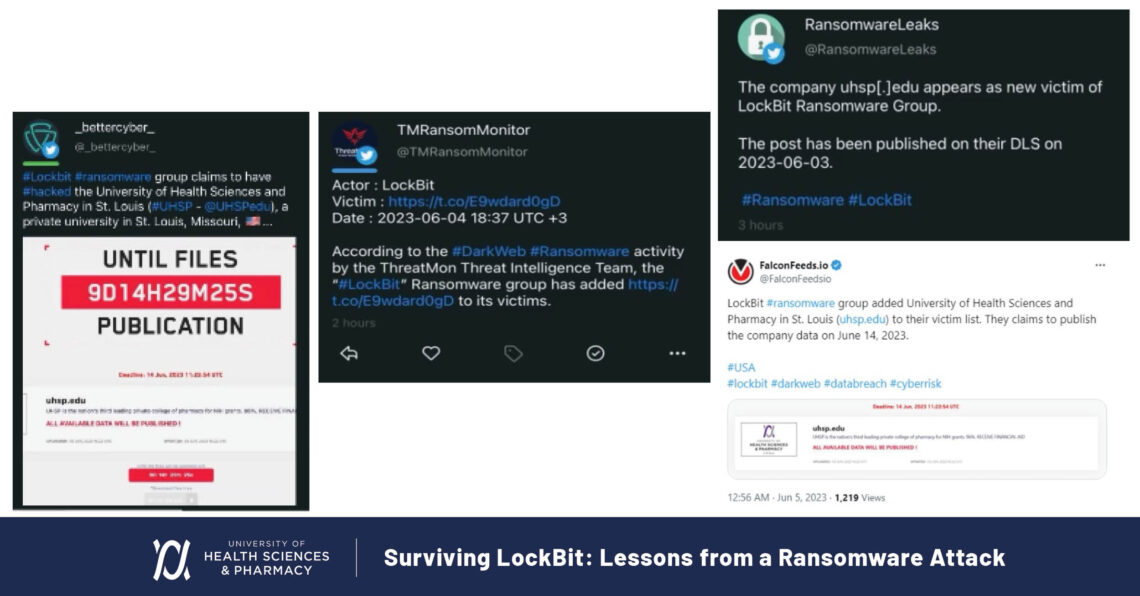
On June 6th, UHSP finally appeared on LockBit’s landing page of victims. They announced June 14th as the drop date if we failed to pay.
People shared reports of the LockBit ransomware attack on UHSP widely on social media.
LockBit’s vultures circled on Twitter, offering decryption key services. Realizing our progress in recovery, LockBit began lowering its ransom demands. They tried everything to push us into action, sending emails to users, showing encrypted files, and emphasizing our ESXI hypervisor. The clock was ticking, but we refused to give in.
Drop day arrived on June 14th, and 2.65 GB of data appeared online. This was far from the original claims of 175 GB or even 75 GB. Among the exposed files, we only found four social security numbers and one immunization record. The affected account owners accepted standard credit monitoring services.
And that was that. We did not pay any ransom and, while the ordeal cost us time and resources, it also left us with critical lessons.
Takeaways: Lessons Learned from LockBit
Going through the LockBit ransomware attack taught us some valuable lessons that I want to share with you:
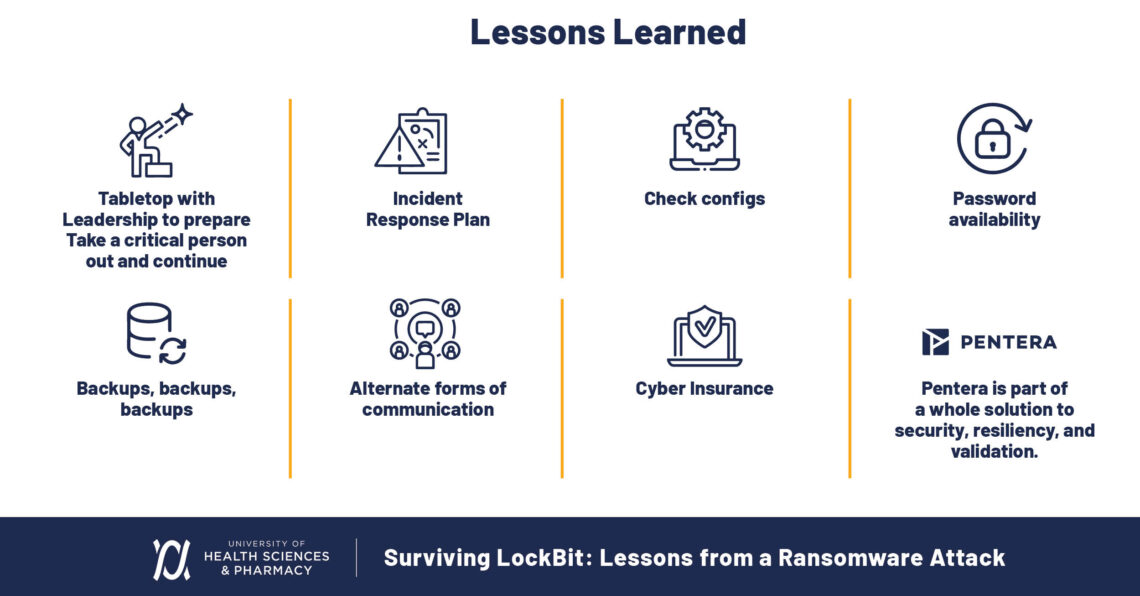
- Always tabletop with leadership, security, and IT: Have a detailed, tested response plan in place. Ransomware attacks are a very real and significant threat to organizations, so you need a ready-made plan to put into action if you find yourself in the midst of an attack.
- Keep a printed copy of your incident response plan: In the event of a ransomware attack, things get encrypted, and you can’t access digital files. Drawing on lessons from real ransomware incidents can help you prepare better. Having a printed copy of the incident response plan ensures you have a reliable reference to guide your actions during the crisis.
- Cyber insurance is a must: Having an incident response team ready to be called in was invaluable to us. Sure, rates go up a bit after an attack, but it’s a drop in the ocean compared to the price of a ransom or lost data.
- Test your resilience in an emulated ransomware scenario: Tools like Pentera would have allowed us to identify the issues we had accessing our primary backups because the ransomware was able to encrypt our AD. Regularly testing your proactive ransomware defense is a crucial step. It was only thanks to our tertiary backup that we could recover as we did, but it would have been so much better if we could have seen and mitigated this exposure in a ransomware emulation.
- Use alternative forms of communication in a ransomware event: Internal email may be compromised. In our case, we used Gmail accounts to communicate with internal leaders, outside counsel, and incident response, which helped us deal with the situation effectively.
- Ensure multiple backup strategies and regularly test them. Our tertiary backup saved us when our primary and secondary backups were compromised. Regular testing of these backups ensures they will be functional when needed.
- Check configurations regularly: Misconfigurations can lead to vulnerabilities, as was the case with our VPN settings. Ensuring all configurations are correct and up-to-date can prevent easy access for attackers.
- Password management and availability: Make sure that you can access your passwords and that they are stored securely. Consider using a cloud-based password manager and ensure that critical passwords are accessible, even if systems are down.
- Plan for critical personnel absences: In your tabletop exercises, simulate scenarios where key personnel are unavailable. Ensure that other team members can step into critical roles if needed, maintaining continuity in your incident response.
- Proactivly communicate with authorities: Engage with law enforcement and relevant authorities promptly during an incident. Their support can be crucial in both managing the attack and in any legal or regulatory follow-up.
Key lessons learned from UHSP’s LockBit ransomware attack
You’ll be better prepared and more resilient against ransomware attacks if you incorporate these lessons into your cybersecurity strategy.
A Call for Proactive Cybersecurity
The LockBit ransomware attack reminded us of the persistent threats we face. By sharing our experience, I hope to encourage more openness, transparency, and collaboration in the cybersecurity community. Discussing these incidents candidly will help us prepare for the challenges ahead, stay resilient, and remain protected. Learning major attack takeaways from other events further strengthens our defenses.
Understanding how ransomware unfolds enables organizations to defend more effectively and recover faster when an attack hits. Stay vigilant, stay prepared, and stay proactive when it comes to your security.
To make sure your security is prepared to block and tackle ransomware attacks and learn how you can eliminate ransomware exposure, read up on our Ransomware Ready offering.