Pentera Credential Exposure
Test for cyber identity risks
from stolen or leaked
credentials.
Harden your credential and identity attack surface.
Check and eliminate compromised credential threats safely.
Discover how our platform
can make a difference for
your security.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Helpful resources for smarter security validation.
FAQ
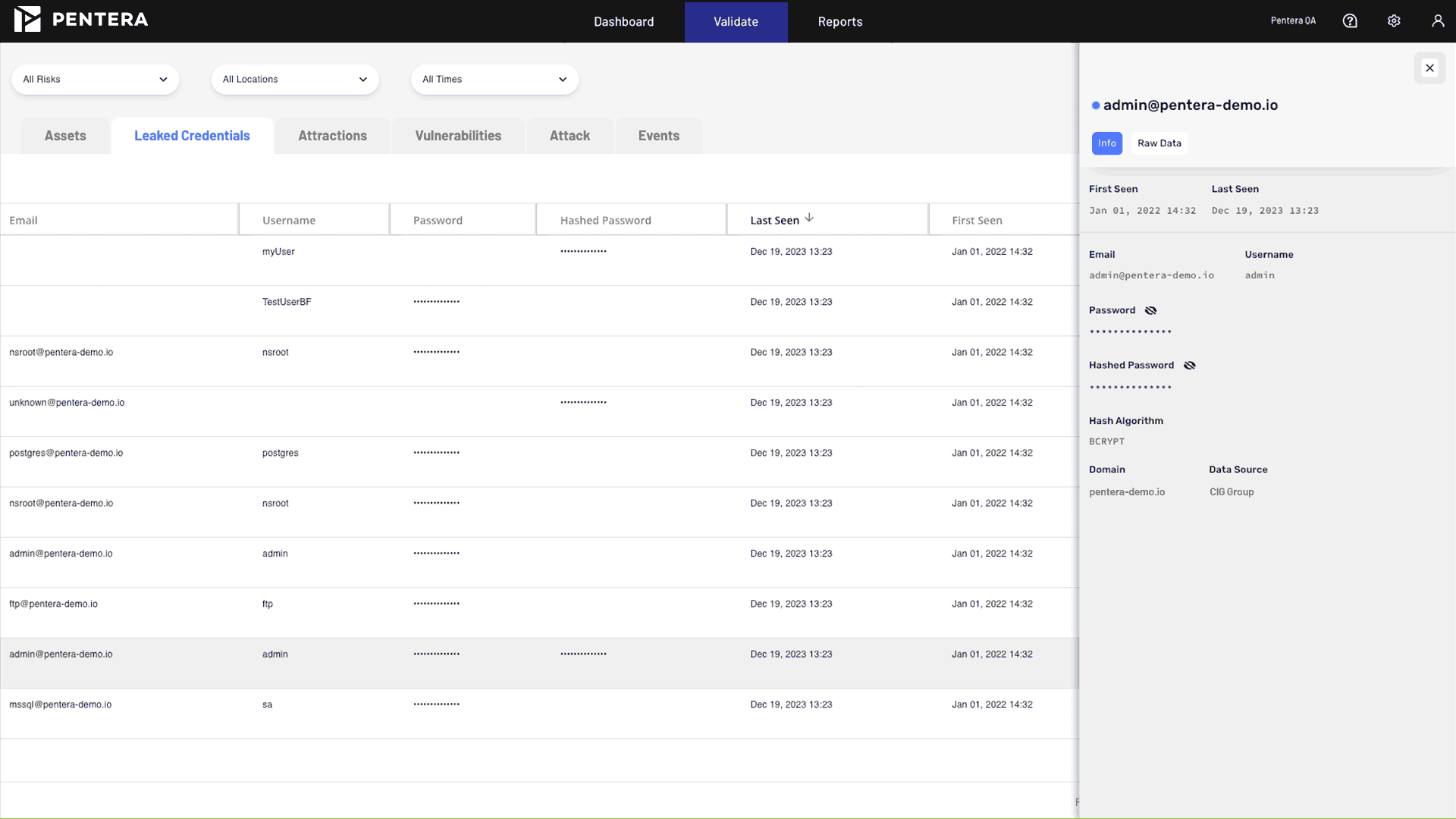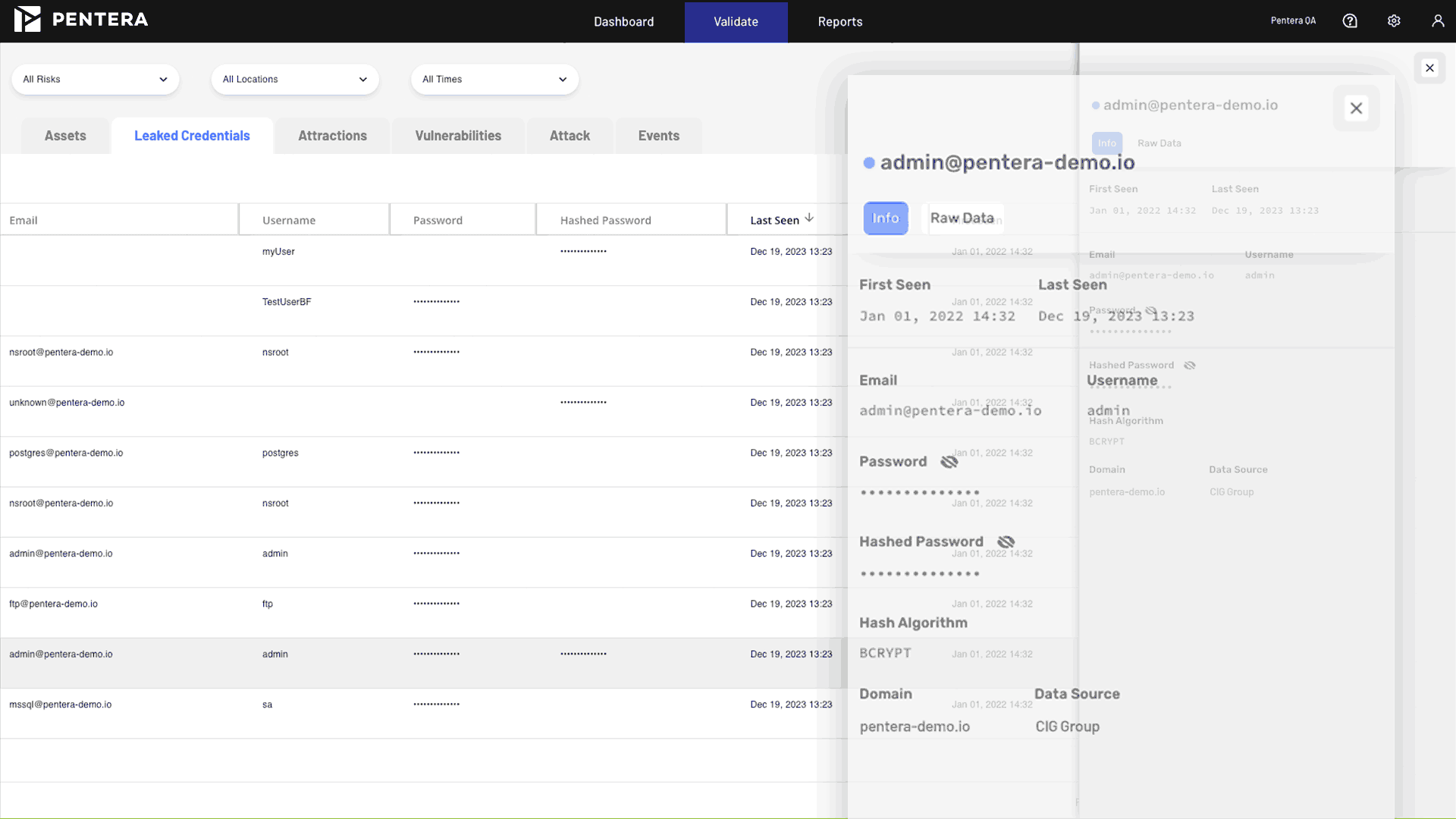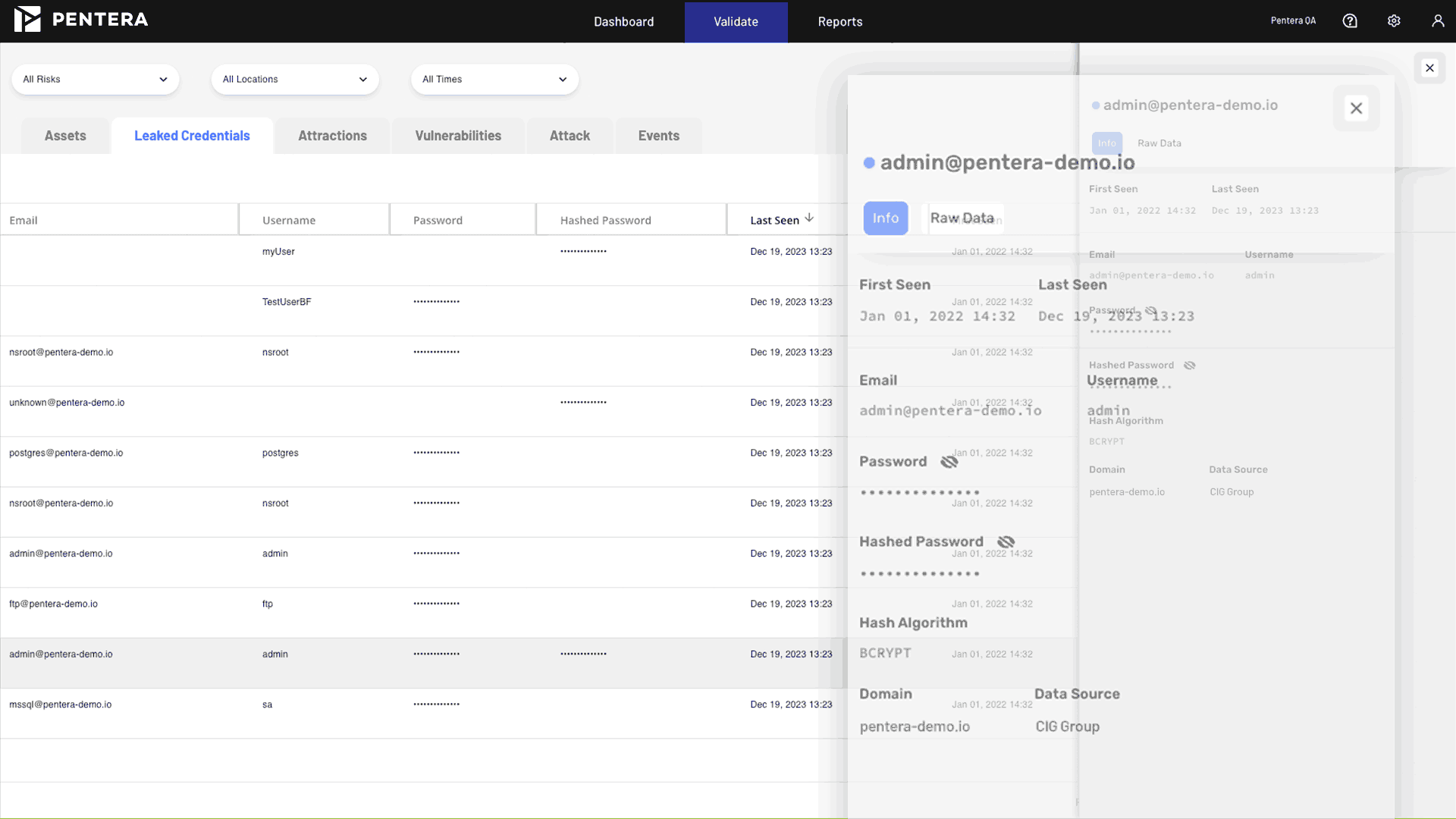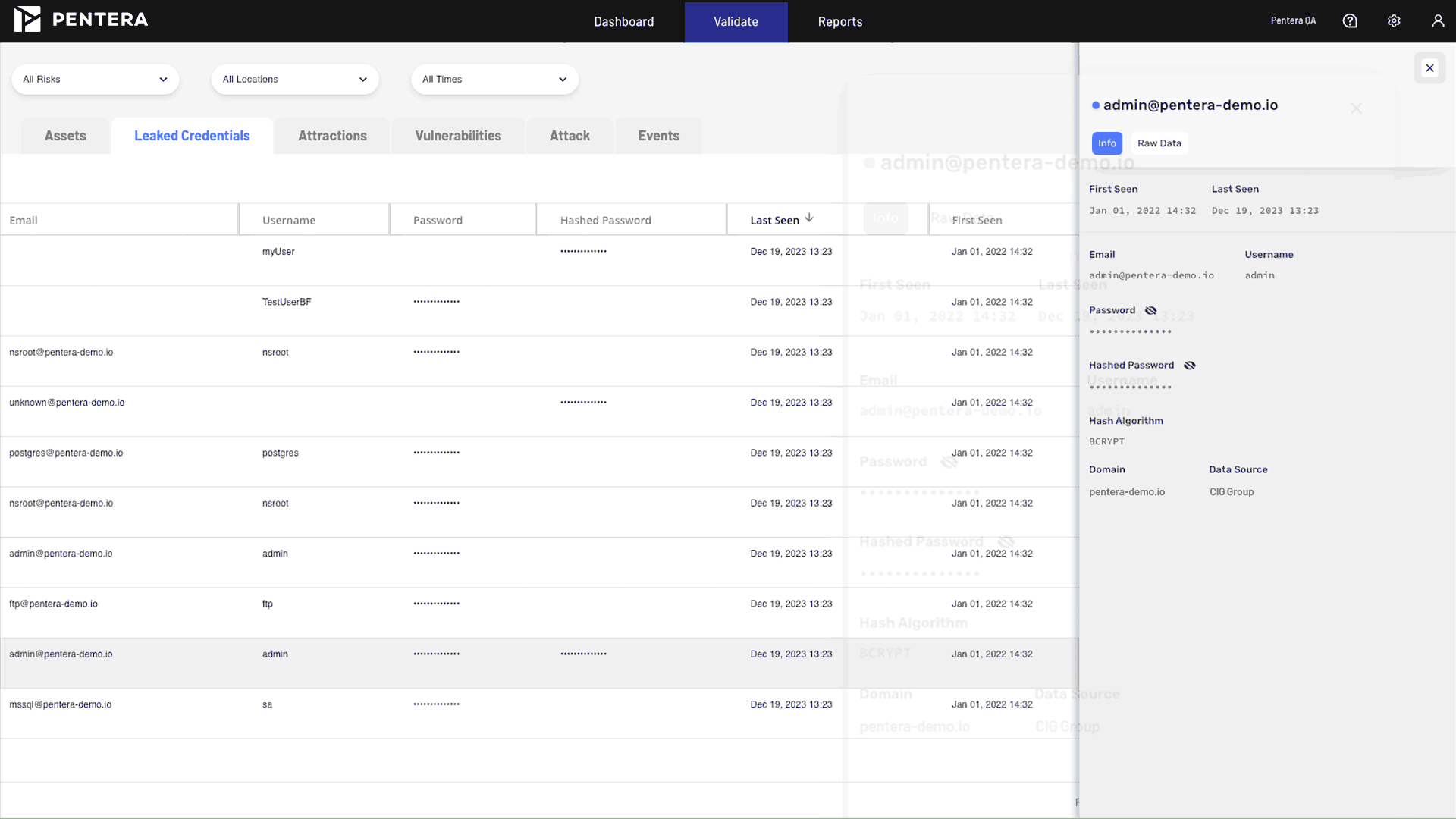
Does Credential Exposure provide any indication of the source of the collected credential data?
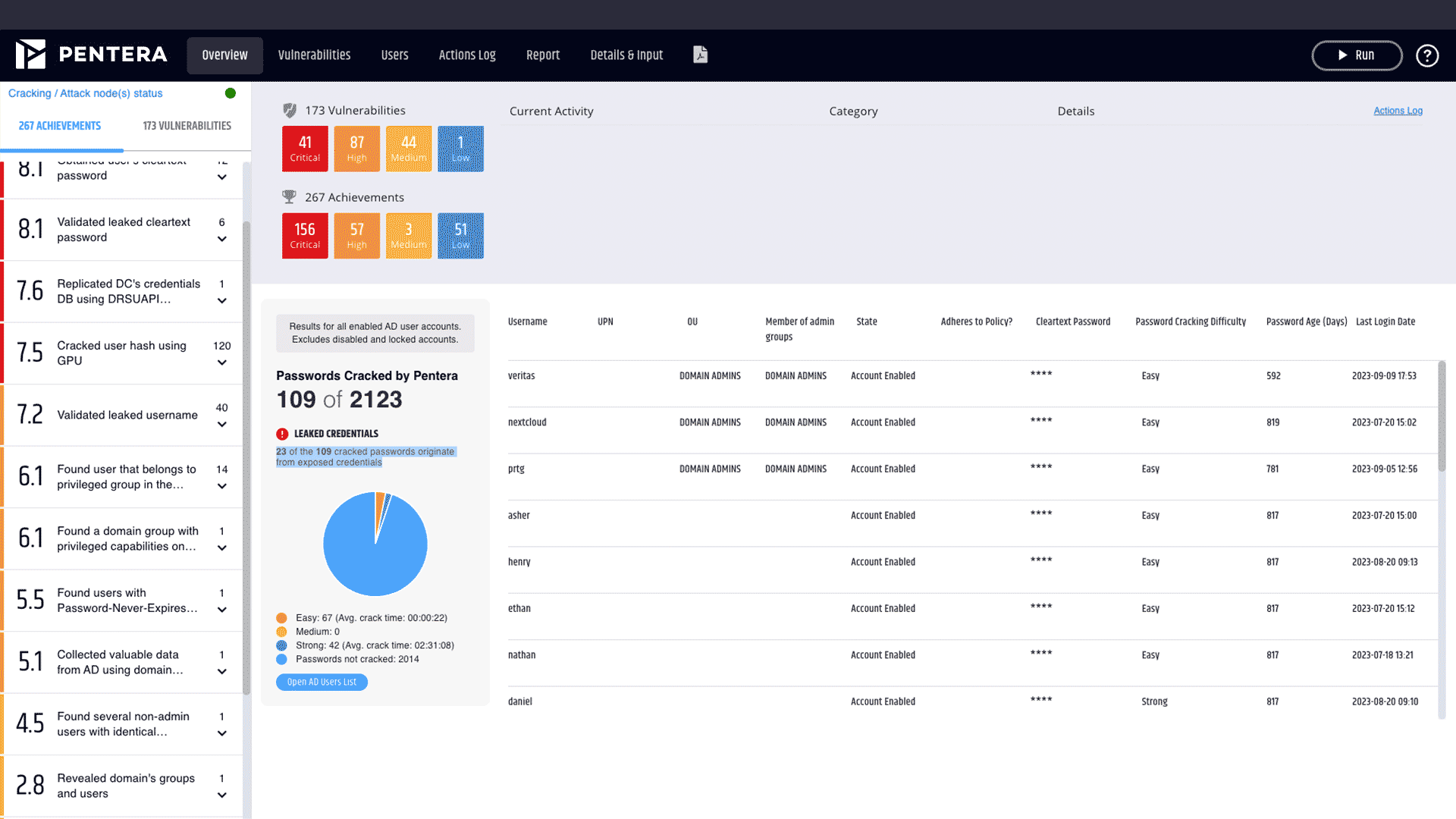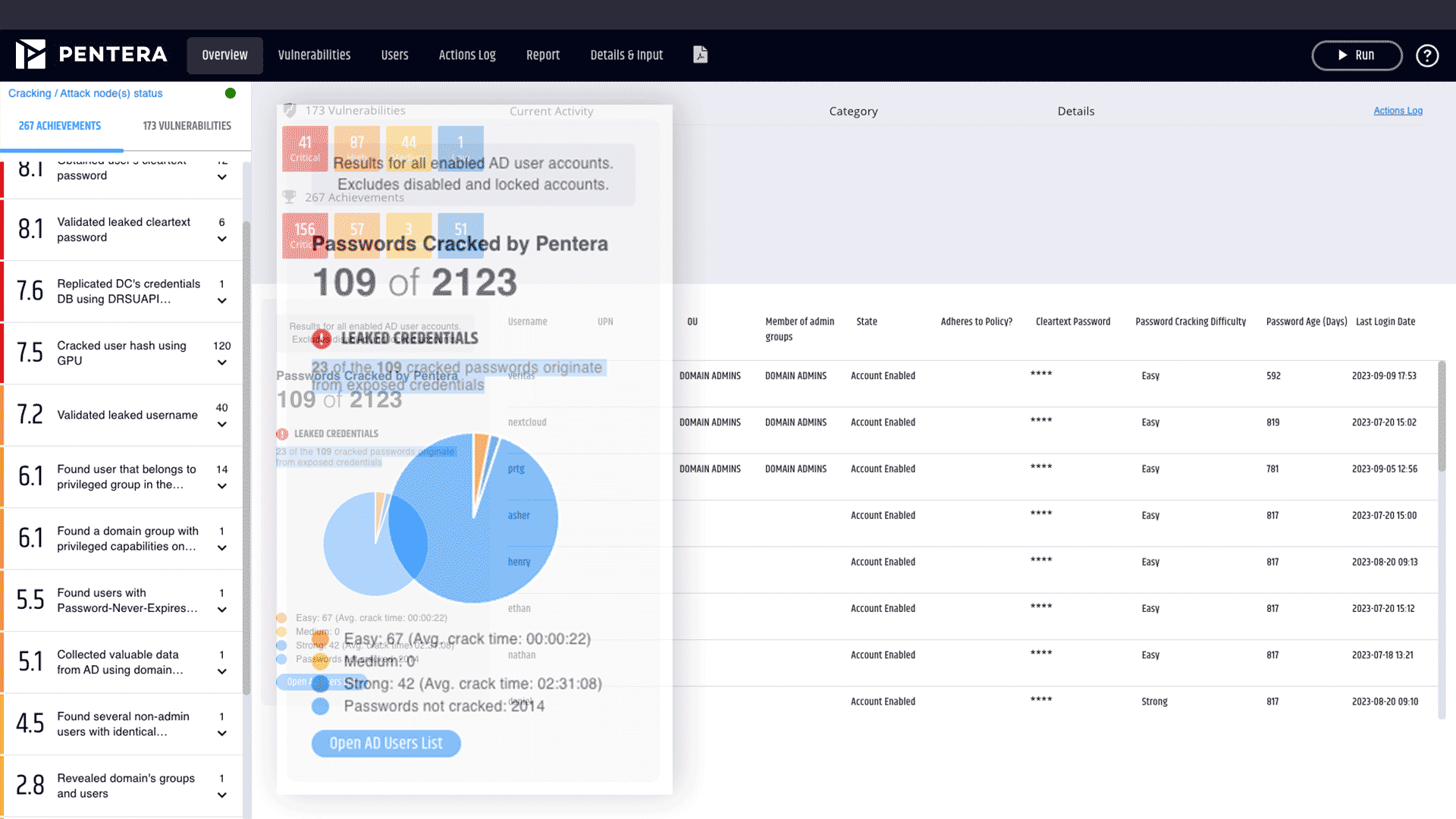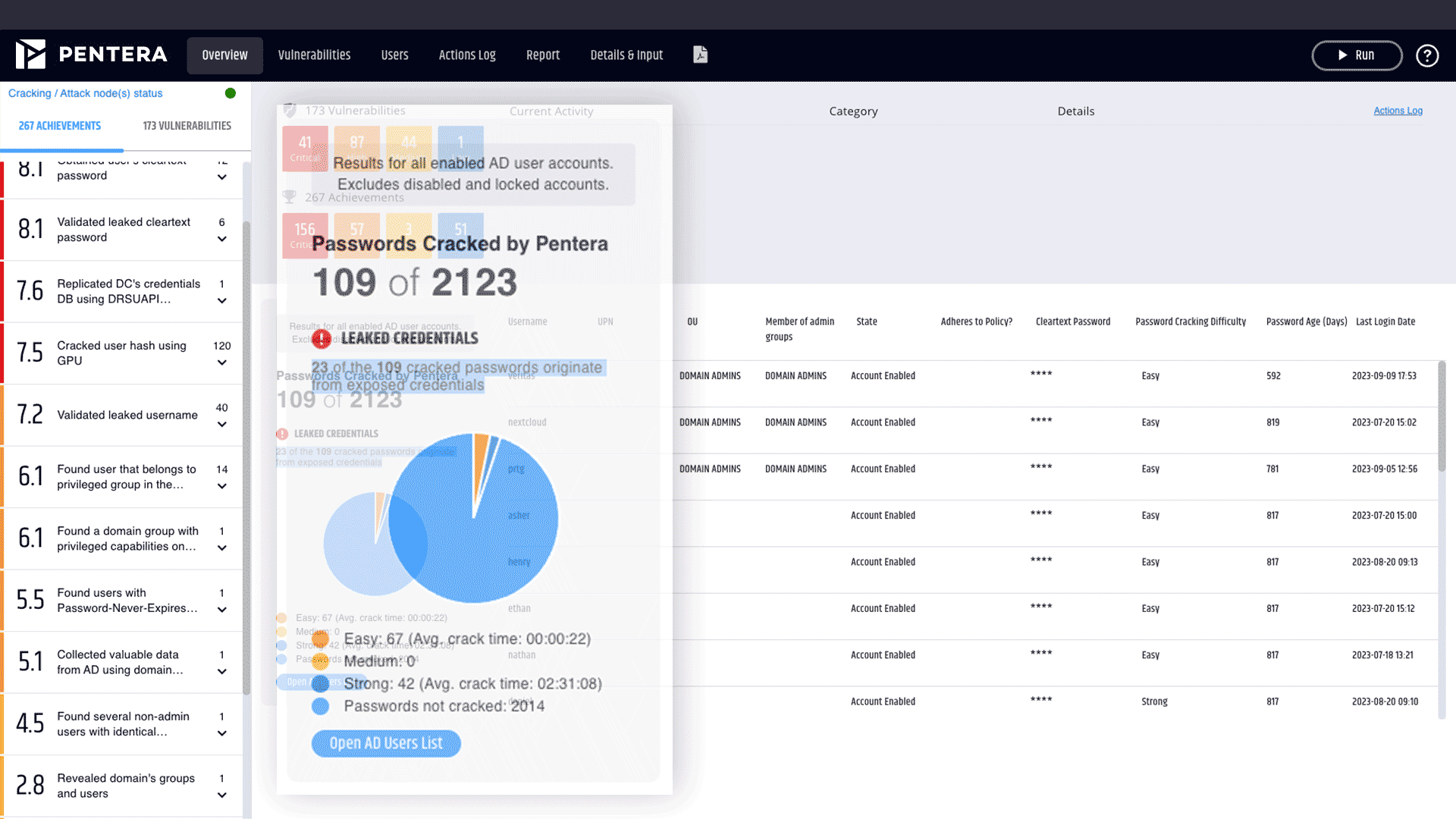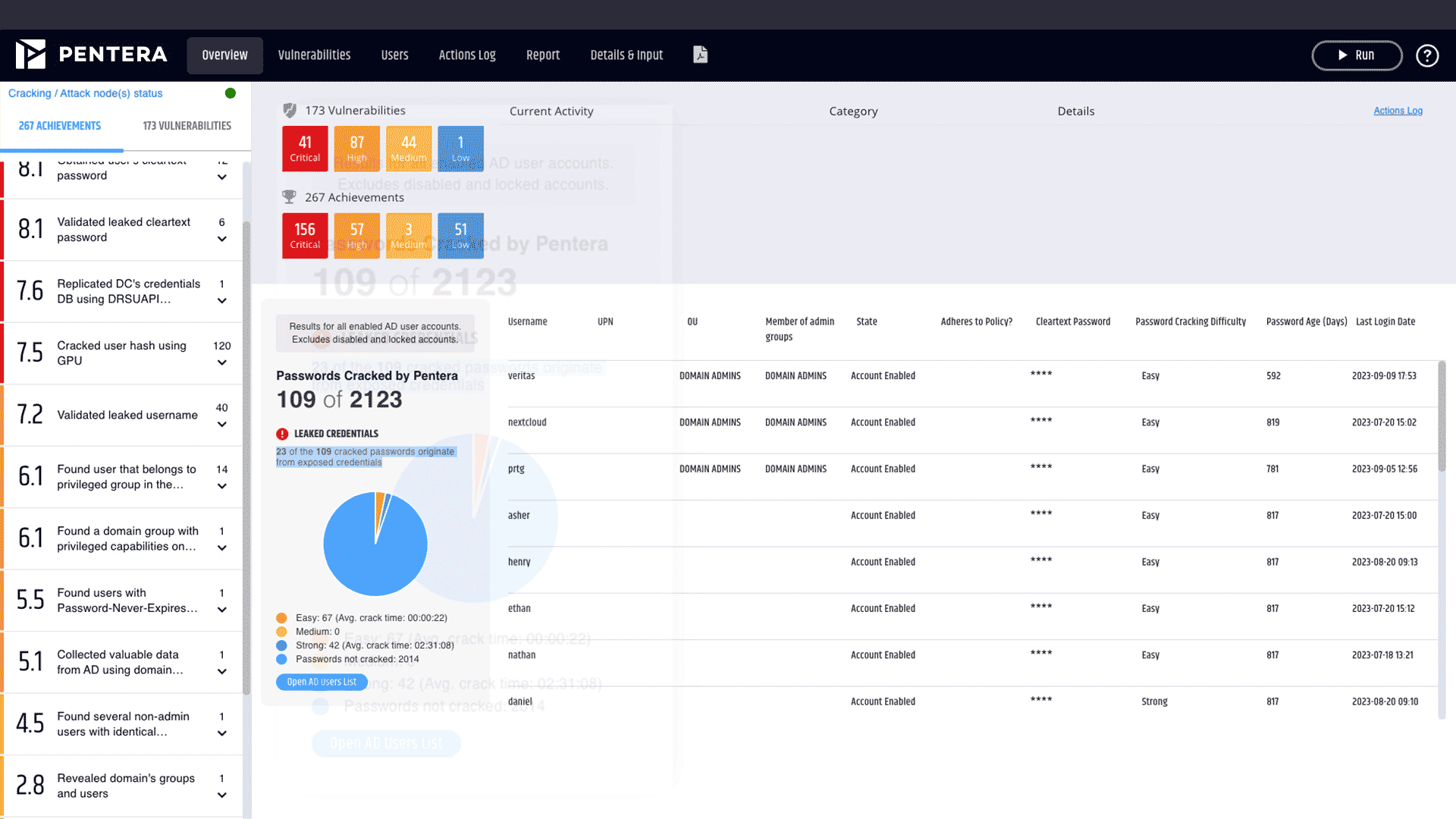
Yes, for each leaked credentials entry, Credential Exposure indicates the source database (not the URL origin). The module correlates data from multiple threat intelligence feeds, the dark web, and password-cracking assessments. Results include details on where the credentials were found (e.g., dark web dump, third-party breach, internal reuse).
How does Pentera differentiate itself from other threat intelligence vendors?
Threat intelligence vendors provide data; such as lists of IOCs, vulnerabilities, or emerging threats, based on what’s happening in the wild. Pentera is different: it operationalizes that intelligence by emulating real-world attacker techniques safely in your live environment. Instead of telling you what could be risky, Pentera proves what is exploitable in your infrastructure and prioritizes remediation by business impact. In short, threat intel shows potential threats; Pentera shows your actual exposure.
Can the customer import leaked credentials from their existing threat intelligence vendors if they wish?
Yes, Pentera Core provides an option to manually load leaked credential data. This is also a good solution for offline customers.
Does Credential Exposure involve testing leaked credentials on applications and systems in production?
The customer controls the provisioning of the validation actions.
Pentera Surface validates credentials by attempting to access detected external-facing assets as an attacker would. Each credential is only validated once, to avoid user lock-out and DDoS.
In Pentera Core, the validation is performed as part of the Active Directory Password Assessment (ADPA) testing. Leaked credentials are treated as additional data that an attacker could use to identify passwords and compromise users in an organization.
How do you integrate the Credential Exposure module across Surface and Core? How is the leaked credential data shared between them?
The matching between Surface and Core is based on the AccountID field – a unique field for each user account. The integration utilizes the existing update mechanism daily
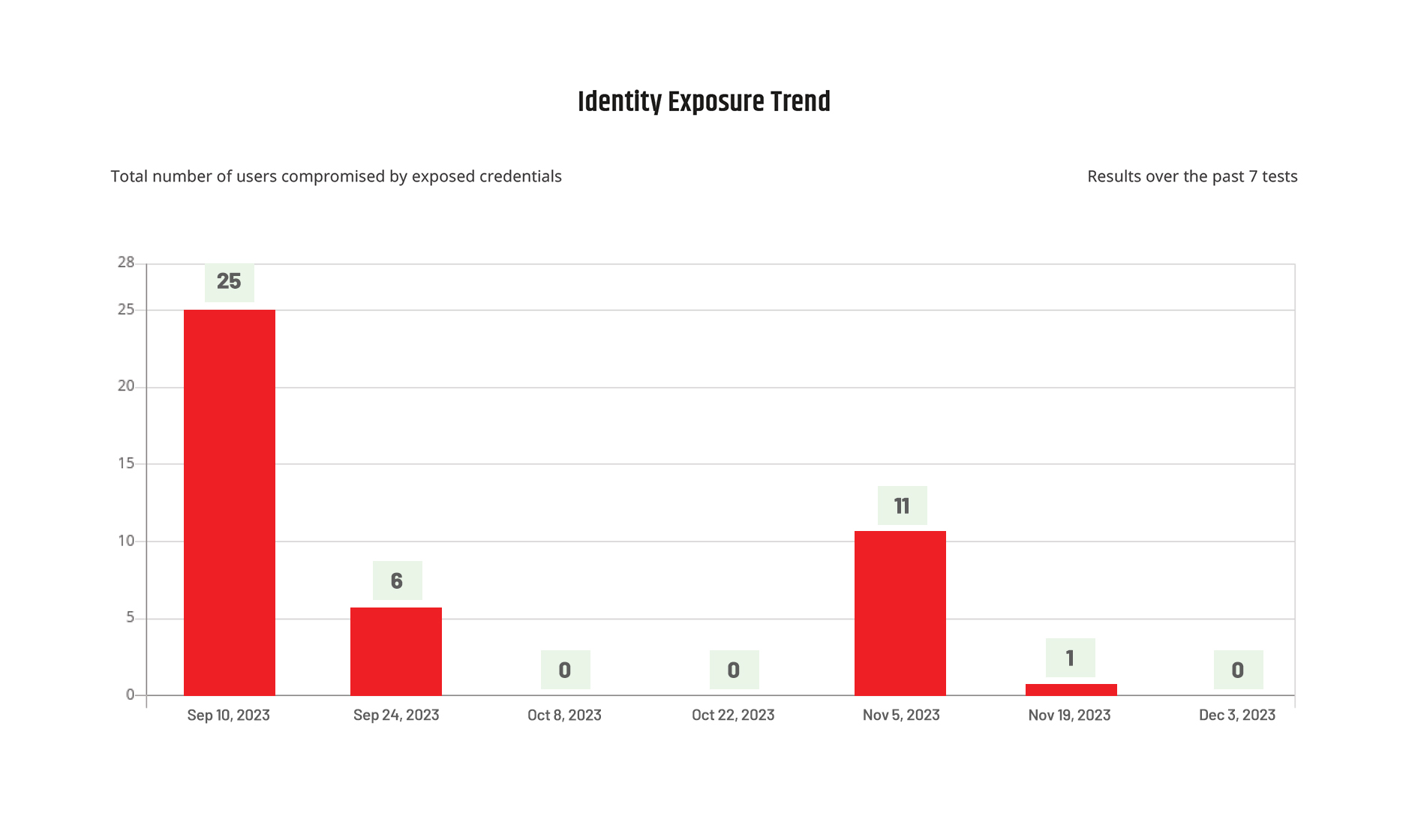
Numeric Header: Identifies and helps to remediate 100% of active leaked credentials in customer environments.