CTEM Adoption
The validation piece of your CTEM framework.
Speed up your CTEM adoption with real-world testing and continuous validation.
Turn threat exposure insights into evidence-based action plans
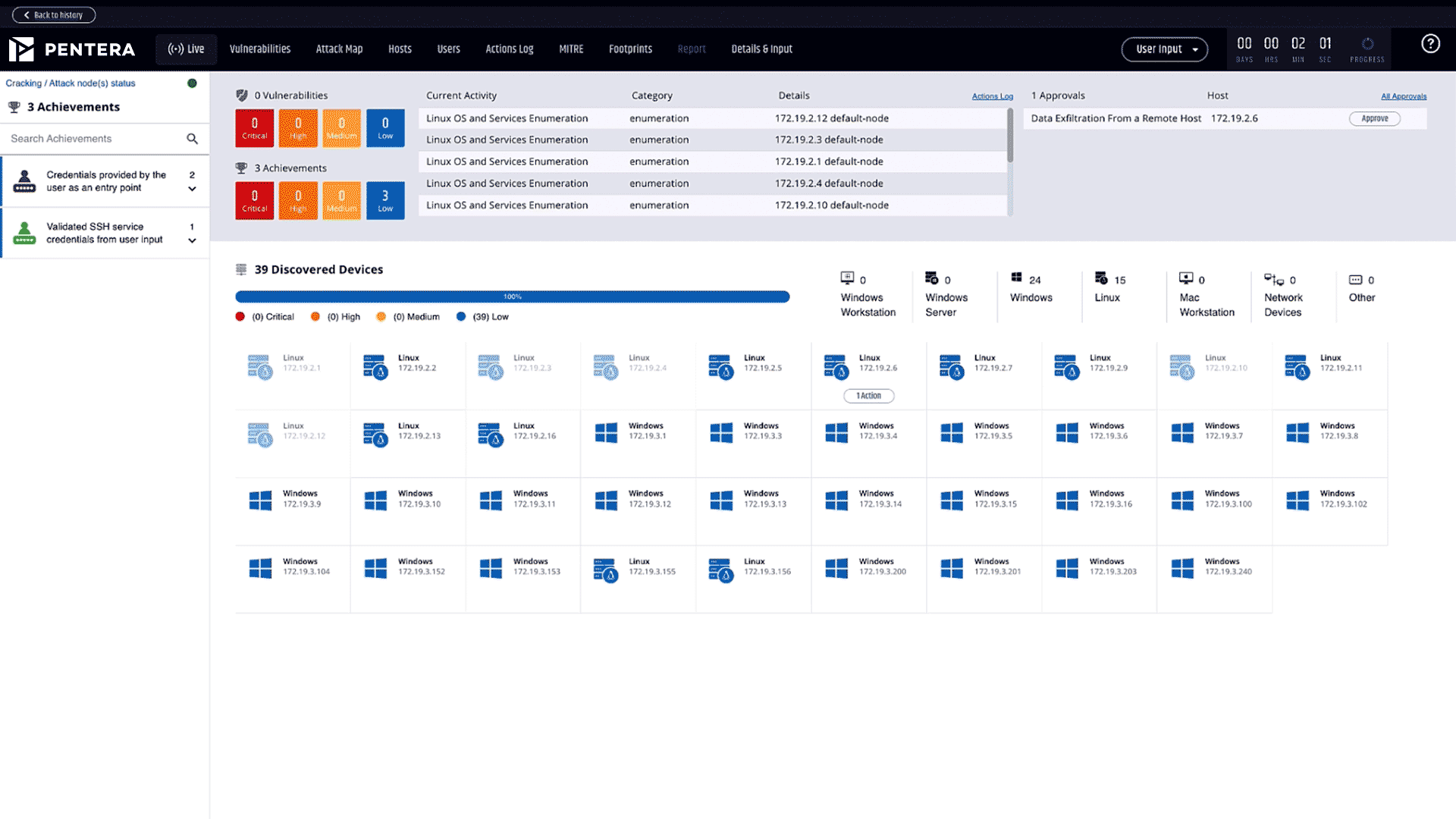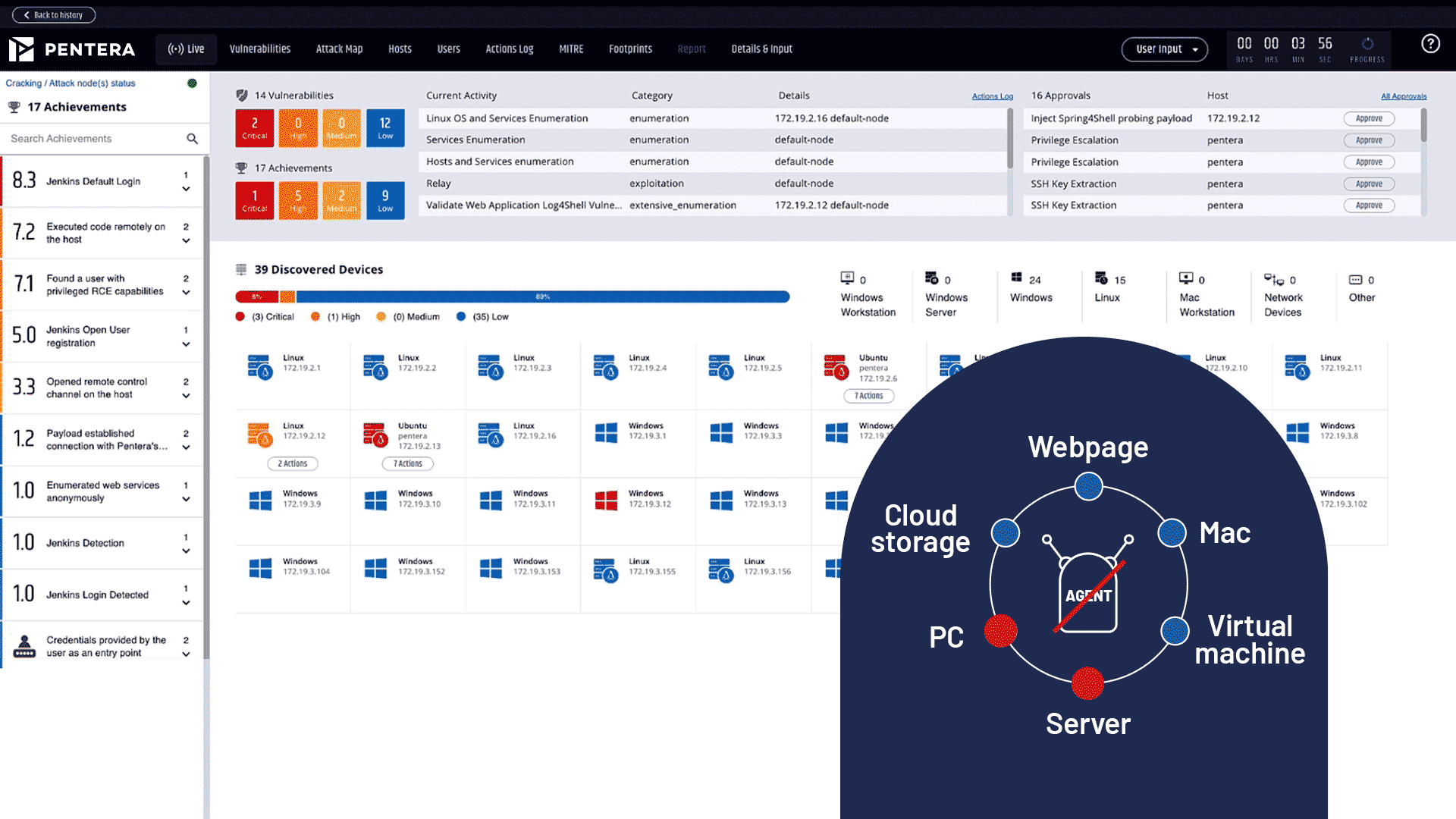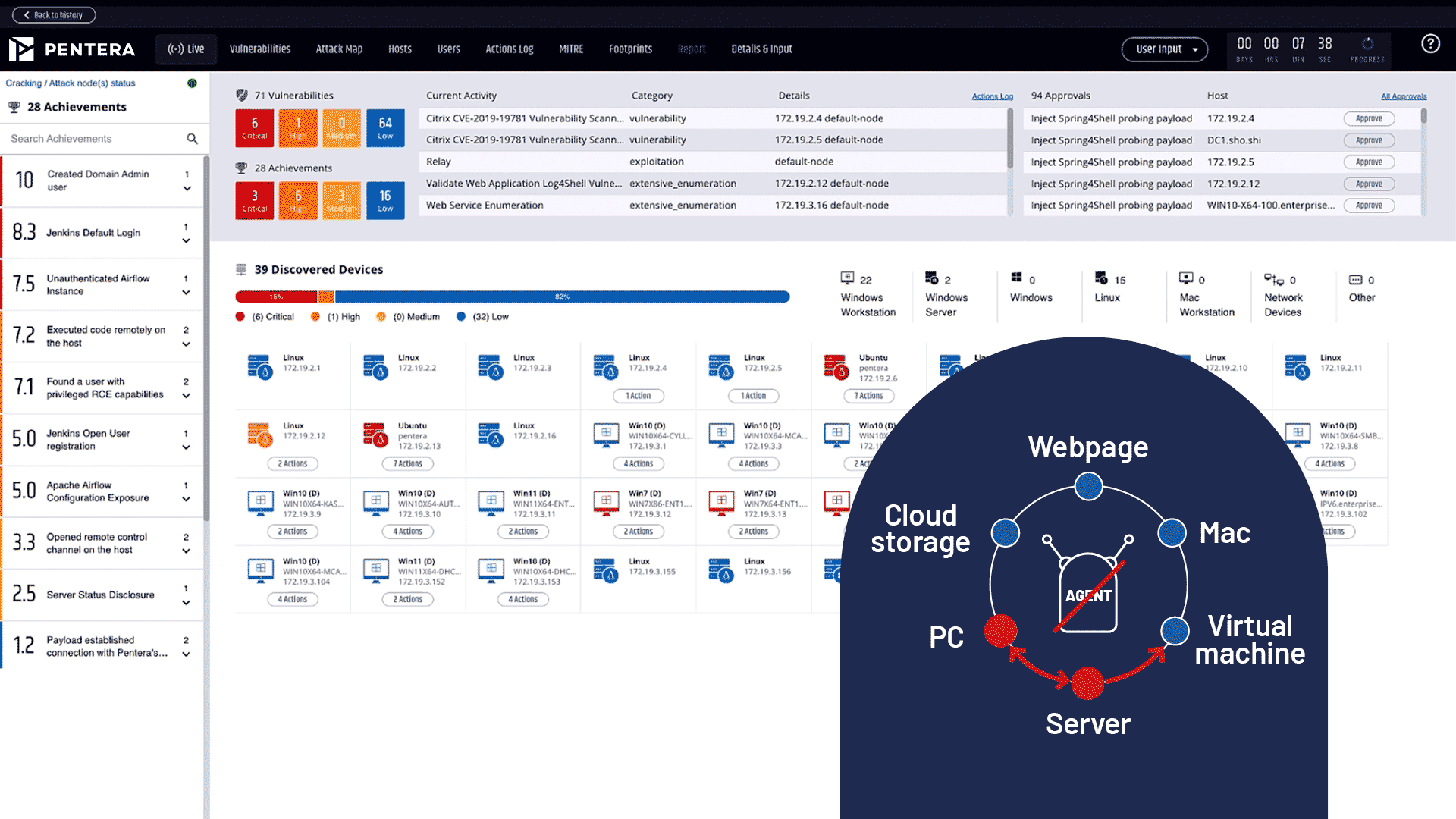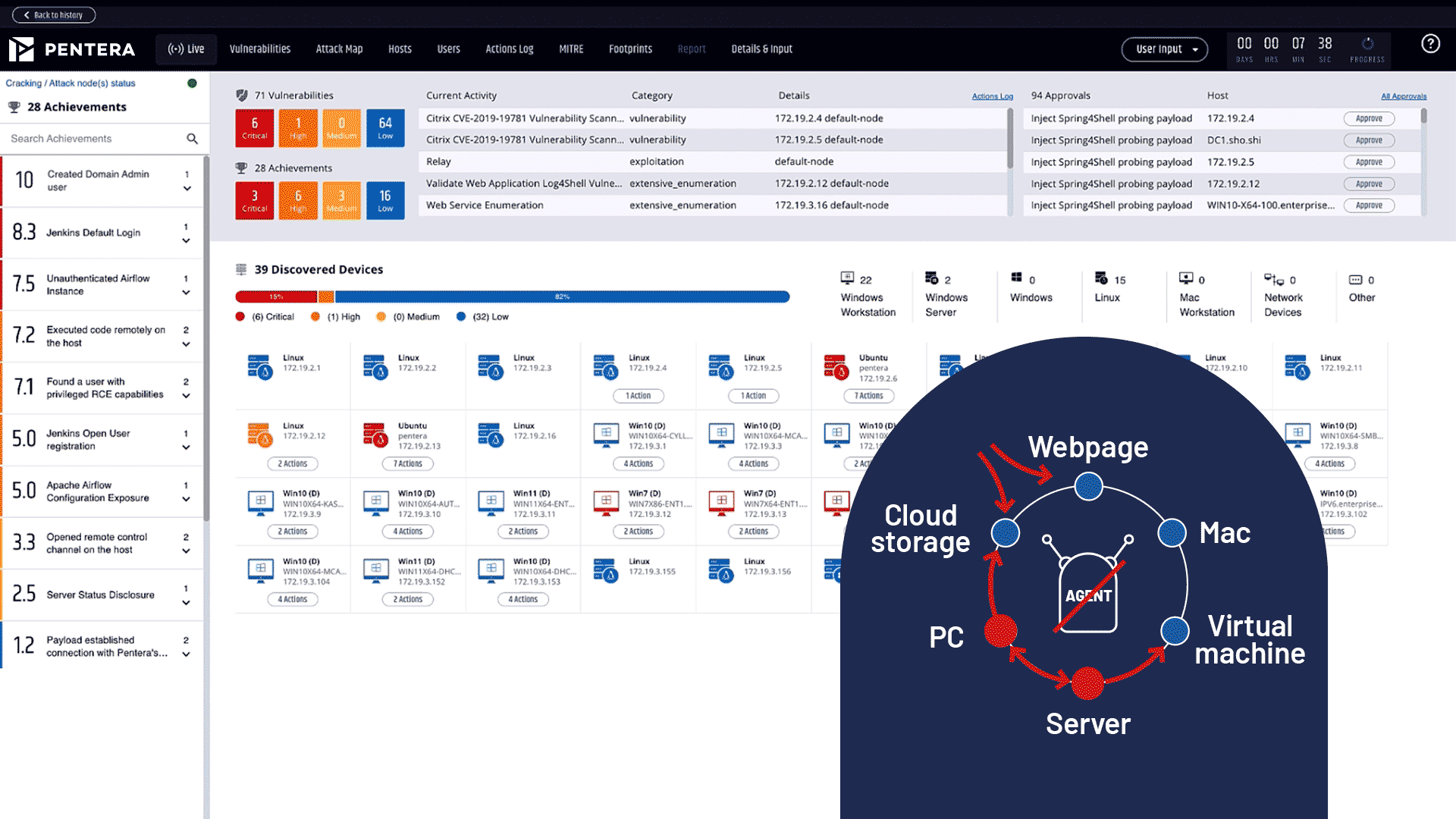
Validate your defenses with real-world attack emulations. Continuously test and challenge your security posture to uncover gaps and ensure ongoing protection with the CTEM framework.
Helpful resources for smarter security validation.
FAQ
What is CTEM?
CTEM (Continuous Threat Exposure Management) is a risk-based framework for continuously identifying, validating, and prioritizing exploitable exposures across your IT environment. Pentera enables CTEM by emulating real-world attacks to uncover your true exposure, helping you reduce risk proactively and continuously.
What is the difference between CTEM and SIEM?
CTEM reveals and validates exposures. SIEM detects and correlates events. SIEM tells you what happened; CTEM shows what could happen and if your controls can stop it. Integrated with SIEM, Pentera enhances detection by revealing blind spots, validating alerts, and enriching correlation logic with evidence-based insights. By combining offensive testing with defensive tuning, Pentera ensures your SIEM is focused on real threats, not noise.
What is the difference between CTEM and SOC?
The SOC responds to threats. CTEM preempts them. CTEM proactively validates your environment and gives your SOC the context and evidence to improve detection, reduce noise, and focus on high-impact exposures.
What is the CTEM Maturity Model?
The CTEM Maturity Model outlines five stages: Scoping, Discovery, Prioritization, Validation, and Mobilization. Pentera automates and accelerates every phase with real attack emulation and evidence-based remediation guidance.
How to implement Continuous Threat Exposure Management?
Start with scoping your critical assets. Then continuously validate exposures using Pentera to emulate real attacks, assess control effectiveness, and prioritize based on risk. Insights are automatically integrated into your remediation workflows for measurable posture improvement.