October 4, 2021

We are all hearing about new vulnerabilities discovered daily in our applications and infrastructure. But that doesn’t mean that our past demons and hacks are gone.
Pass-the-Hash hacking technique was first published in 1997 but is still challenged by hacker toolkits nowadays exploiting the good old Windows NTLM authentication mechanism.
The point is, to KNOW your cyber security works today, you need to validate against the latest threats but also perform “regression testing” for past exploits that are still in use.
This has ceased to be a person’s job – this is a job for software.
<Previous

The CISO Game
Unlike the Squid Game, the CISO-CIO relationship is not a matter of life and death. It’s more like Red light - a ransomware attack. Green light - preventing a breach with better communication and decision-making.
Next>
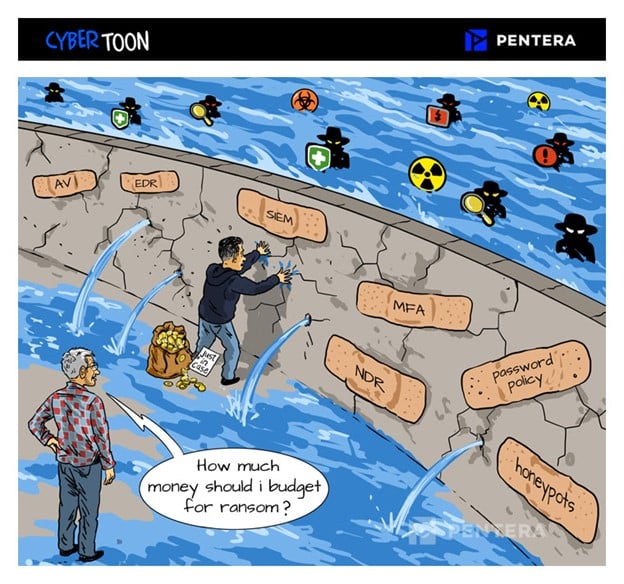
Ransomware is not Inevitable
Hans Brinker may have saved Holland by plugging his finger in a hole, but we know that’s not sustainable, not scalable, and doesn’t work in practice – certainly not in cybersecurity. We add more tools to our security tech stack, hoping we’re covered. While it may feel like you’re “dammed” if you do, damned if […]



