What is Command and Control (C2) in Cybersecurity?
Command and Control (C2) refers to the methods cybercriminals use to communicate with and control compromised systems. After gaining initial access, attackers use C2 channels to issue commands, spread malware, exfiltrate data, or launch further attacks.
Command and Control (C2) systems enable attackers to maintain long-term access to compromised systems. Advanced Persistent Threat actors often rely on C2 to execute commands and exfiltrate data without detection.
What is Command and Control (C2) in Cybersecurity?
Command and Control (C2) refers to the mechanisms used by attackers to issue instructions to malware on compromised devices. Once a device is compromised, the C2 infrastructure allows threat actors to control the malware remotely, coordinating malicious activities such as downloading additional malware, creating botnets, or exfiltrating data.
C2 can leverage a variety of technologies, including communication protocols, covert channels, and callback mechanisms, to maintain stealth and evade detection. For this reason, C2 detection should be a top priority for security operations teams.
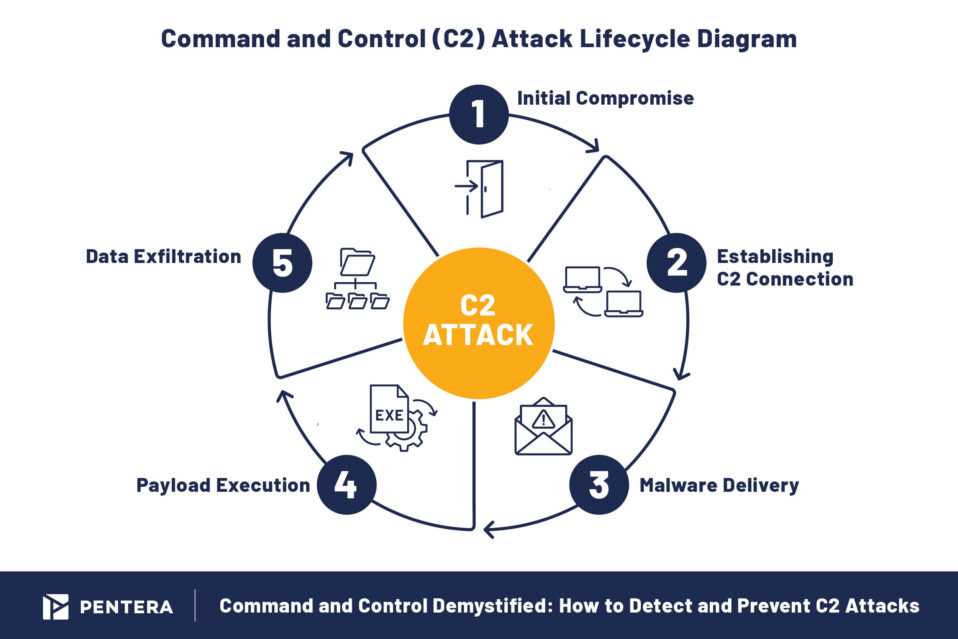
Stages of Command and Control C2 Attacks
A typical C2 attack unfolds in several stages, each crucial to the success of the operation:
- Initial Compromise: Attackers exploit vulnerabilities (e.g. unpatched software) or use social engineering techniques to gain access to the target system.
- Establishing C2 Connection: Once inside, the attacker establishes communication with a C2 server, creating a channel to send instructions and receive information or further instructions.
- Malware Delivery and Execution: The compromised system is used to download and execute malware payloads, which then follow the instructions received from the C2 infrastructure.
- Data Exfiltration or System Disruption: At this stage, attackers use C2 to extract sensitive data or disrupt system operations, such as launching ransomware attacks.
- Defense evasion: Attackers commonly attempt to mimic normal, expected traffic to avoid detection. Depending on the victim’s network, they establish command and control with varying levels of stealth to circumvent security tools.
Attackers may employ advanced techniques such as encryption, obfuscation, and dynamic DNS services to evade detection. A classic example of a Command and Control C2 attack is a ransomware operation, where C2 is used to deploy malware , encrypt critical data and exfiltrate it by bypassing endpoint protection tools and other security controls.
Common Types of C2 Malware
C2 malware comes in various forms, but its purpose is always the same: to maintain communication with a C2 server and carry out attacker commands.
For example, the disastrous Log4j involved attackers exploiting vulnerabilities to infiltrate systems, escalate privileges, and establish control over networks. This critical flaw which was discovered in 2021 but continued to be exploited well into 2023, allowed attackers to execute remote code, opening the door for command-and-control (C2) attacks. Attackers would install backdoors, communicate with compromised systems, and conduct further malicious activities.
Some common examples include:
- Rootkits: Alter system functions to hide attacker activity, ensuring long-term access.
- Remote Access Trojans (RATs): Allow attackers full control over compromised systems for data theft or surveillance.
- Keyloggers: Record keystrokes, helping attackers steal credentials and sensitive information.
- Botnets: Networked devices controlled by C2 servers to launch coordinated attacks, such as Distributed Denial of Service (DDoS) attacks.
Proactive C2 Defense
The best defense lies in building your security system’s resilience, therefore it’s important to be able to uncover your system’s weaknesses before they can be exploited. Automated security validation tools, like Pentera, are used to emulate the techniques used by real-world attackers to C2 attacks. By emulating these attacks on live IT production environments, including reconnaissance, lateral movement, and C2-based data exfiltration, security teams can proactively identify and close gaps in their defenses.
How to Detect and Prevent C2 Attacks
Detecting C2 activity early is key to stopping attacks before they escalate. Here are several ways to detect and prevent Command and Control C2 attacks:
- Endpoint Detection and Response (EDR): EDR solutions can monitor systems for suspicious activity, such as high resource usage or unusual connections to external servers and block suspicious activities
- Intrusion Detection Systems (IDS): These tools analyze network traffic to detect anomalies that could indicate C2 activity.
- Cyber Threat Intelligence (CTI): Utilizing threat intelligence to stay informed about emerging C2 tactics and infrastructure.
- Traffic Analysis: Monitoring outgoing traffic for abnormal patterns (like frequent communication with known malicious IP addresses or domains) to detect C2 connections.
However, prevention is always better than detection. Proactively addressing security vulnerabilities can prevent attackers from establishing C2 infrastructure in the first place.
Building Resilience Against C2 Attacks
Incorporating C2 detection and prevention strategies into your organization’s cybersecurity framework can drastically improve incident response times and strengthen defenses against prolonged attacks. By understanding C2 attacks, security teams can recognize early indicators of compromise and deploy countermeasures more effectively.
Securing Your Organization from C2 Attacks
Tackling Command and Control C2 attacks should never be an organization’s sole focus but should be part of a larger security program including good “cyber hygiene” practices, security awareness training for employees, and continuously tested and validated policies and procedures. Proactively identifying vulnerabilities and securing your infrastructure against these exposures is critical to minimizing your exposure and maintaining a robust cybersecurity posture.
Frequently asked questions
What is a Command and Control (C2) attack in cybersecurity?
C2 attacks refer to the mechanism that allows attackers to communicate with and control compromised systems remotely, issuing commands such as deploying malware, exfiltrating data, or launching further attacks.
How do attackers establish a C2 connection?
Attackers typically establish a C2 connection by exploiting system vulnerabilities or using phishing attacks to gain initial access. Once inside the network, they set up communication channels to their C2 servers to control infected systems.
What are the common types of malware used in C2 attacks?
C2 malware includes Remote Access Trojans (RATs), botnets, rootkits, and keyloggers. These types of malware allow attackers to maintain control over compromised systems, hide their activity, and launch additional attacks.
How can organizations detect C2 activity in their networks?
Detecting Command and Control C2 attacks involves monitoring network traffic for unusual patterns, using tools like Endpoint Detection and Response (EDR) and Intrusion Detection Systems (IDS), and analyzing outbound connections to known malicious domains or IP addresses.
What are some best practices for preventing C2 attacks?
Preventing Command and Control C2 attacks involves patching vulnerabilities, implementing strong access controls, monitoring network traffic for anomalies, and using threat intelligence to stay updated on emerging C2 techniques.
Identify and fix vulnerabilities in C2 attack paths.
Test your defenses against C2 attacks.