Pentera Core
Know that your
internal controls block attacks.
Test your defenses from within.
Network security validation in-depth.
Discover how our platform
can make a difference for
your security.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Helpful resources for smarter security validation.

FAQ
Does Pentera support big distributed infrastructures?
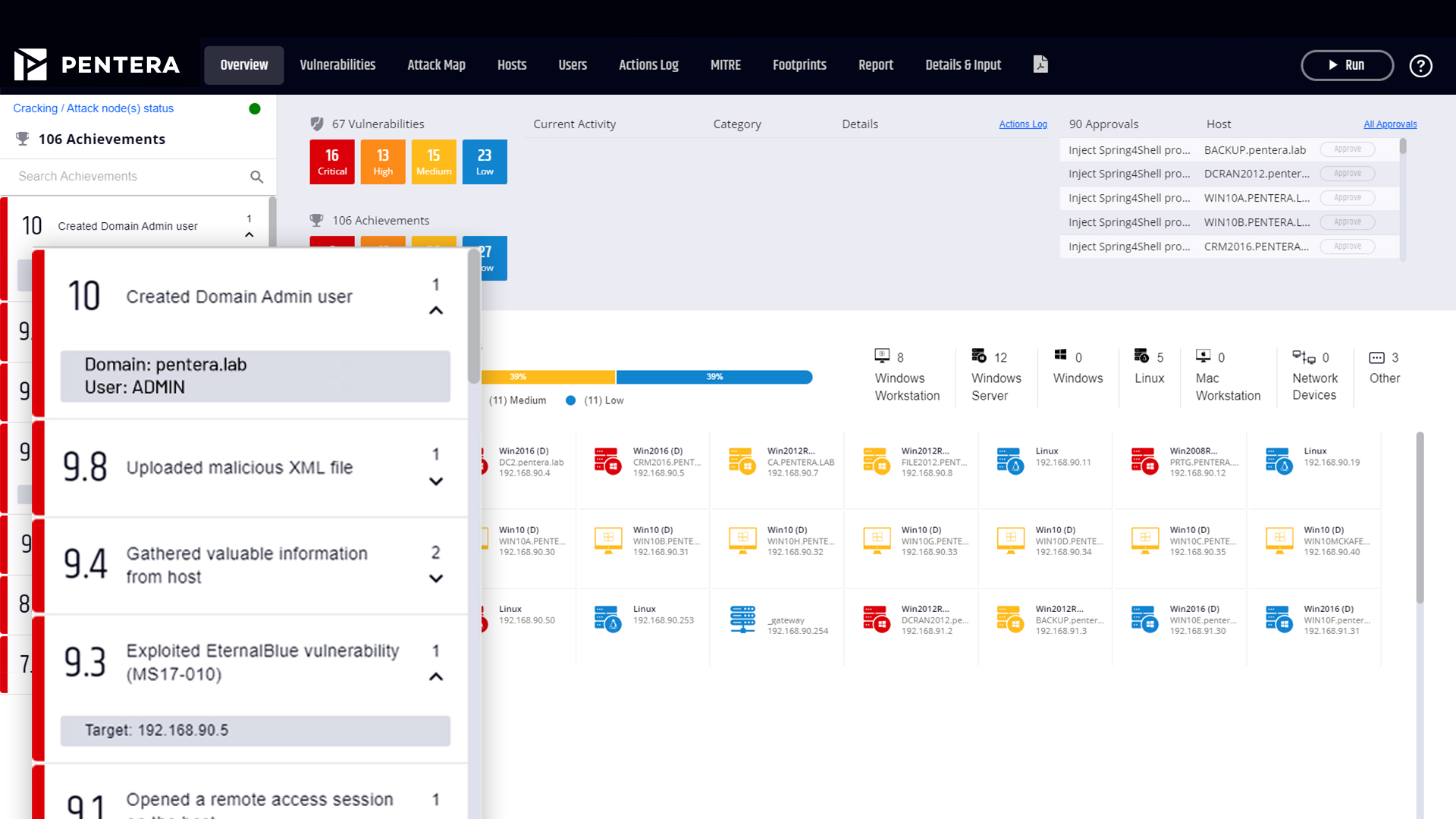
Yes. Pentera Core uses Remote Attack Nodes (RANs) to extend the testing scope to remote offices and data centers. A RAN can be deployed in remote offices, data centers, or cloud environments to emulate attacks from that location. This allows you to run internal security validation at scale, without backhauling traffic, and ensures distributed environments are tested consistently. All tests are orchestrated centrally, providing unified visibility and reporting.
Is it possible to set up alerts on Pentera Core if critical vulnerabilities are identified?
Yes. Pentera Core can generate alerts when critical, exploitable vulnerabilities are identified. Findings are prioritized by business impact and can be integrated into SIEM, SOAR, or ticketing systems via API or reporting workflows. This enables security teams to receive real-time notifications, automatically open remediation tickets, and ensure critical exposures are addressed quickly.
Does Pentera Core do application pentesting?
While Pentera Core does not perform full application penetration testing like business logic testing or OWASP code reviews, it can uncover application-related exposures (e.g., weak authentication, misconfigurations, credential reuse) as part of broader attack paths. For full application pentesting, organizations typically complement Pentera with dedicated AppSec tools or services.
Can Pentera Core move between network segments?
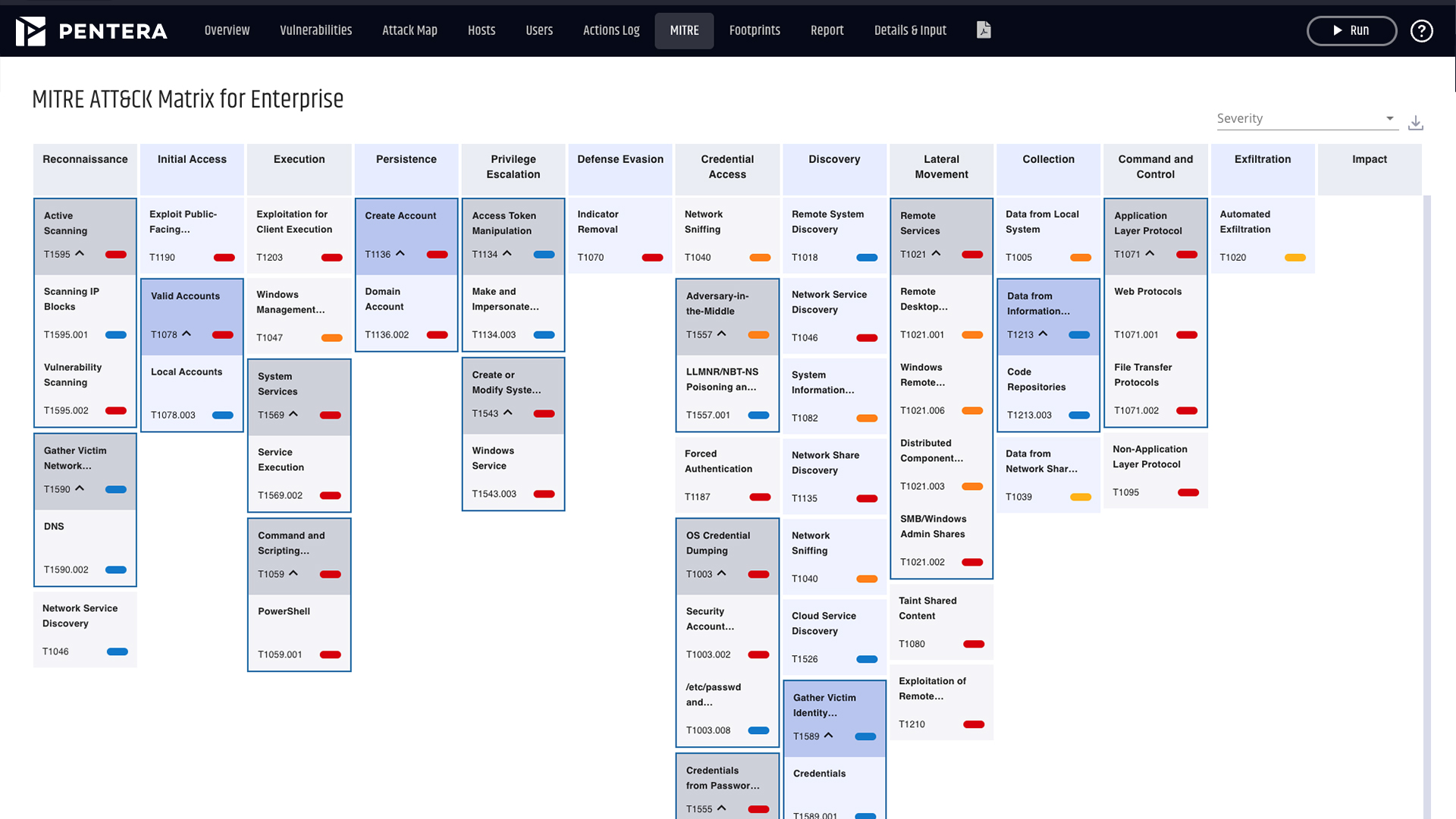
Yes. Pentera Core is designed to emulate real attacker behavior, including lateral movement across network segments. It identifies misconfigurations, weak credentials, or trust relationships that allow movement between segments, mapping full attack paths. This helps security teams validate segmentation controls and confirm whether attackers could pivot deeper into the network.
Can the user determine what critical assets are? Whether devices or accounts?
Yes. In Pentera Core, users can define which assets, such as specific devices, servers, or accounts, are considered critical. These inputs help tailor testing and remediation prioritization, ensuring Pentera highlights attack paths and exposures that matter most to the business. This allows teams to align validation results with their own asset criticality and risk priorities.