Pentera Platform
Focus your energy on true
security gaps across your
entire attack surface.
Build up your security readiness with AI-powered security validation™.
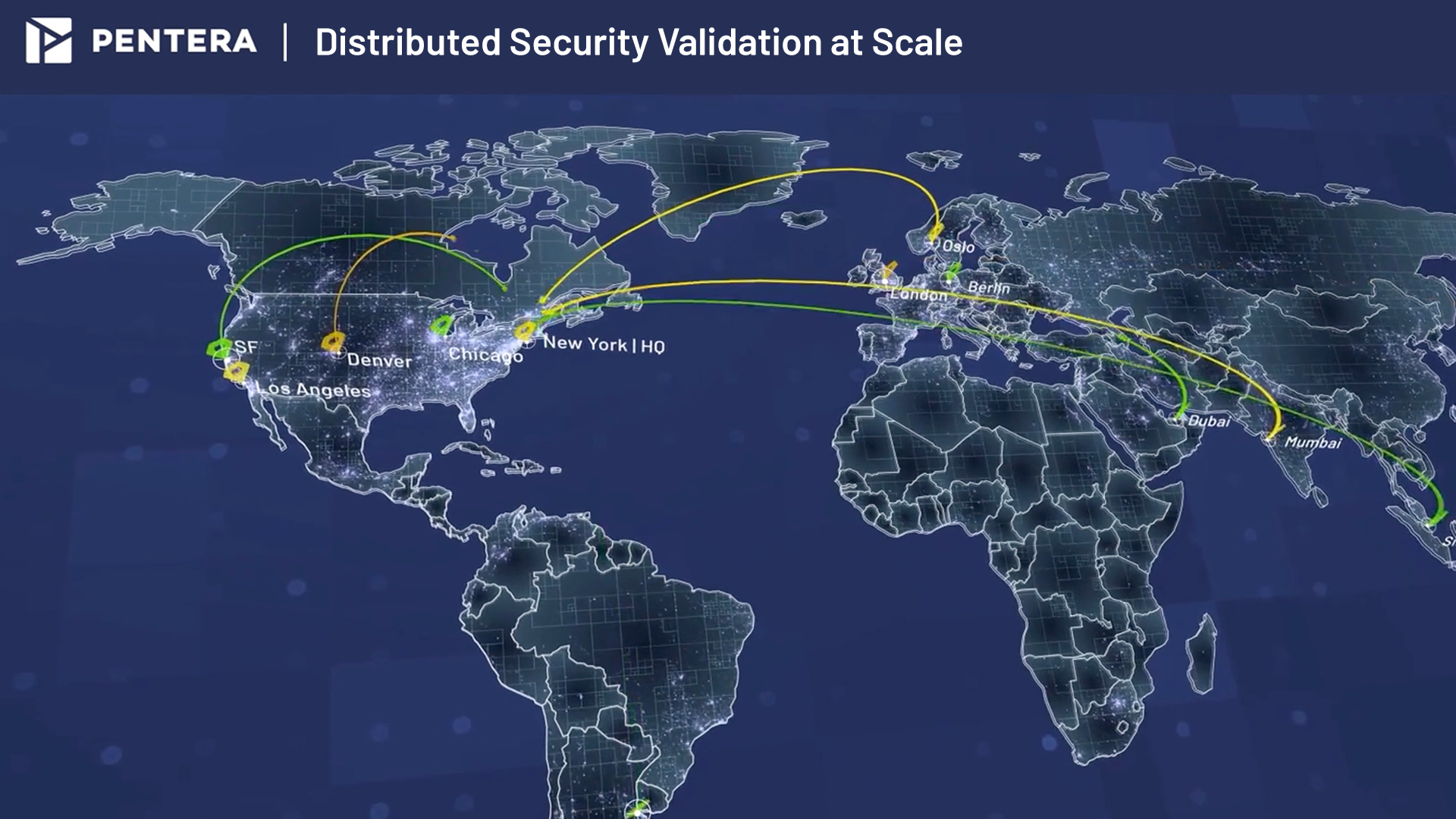
Orchestrate Distributed Attacks Across the Enterprise
Govern a consistent security posture across decentralized IT architectures. Enterprise security teams can scale security validation testing by simultaneously running tests across distributed environments, coordinated through a single interface.
Close security gaps faster
with automated remediation workflows
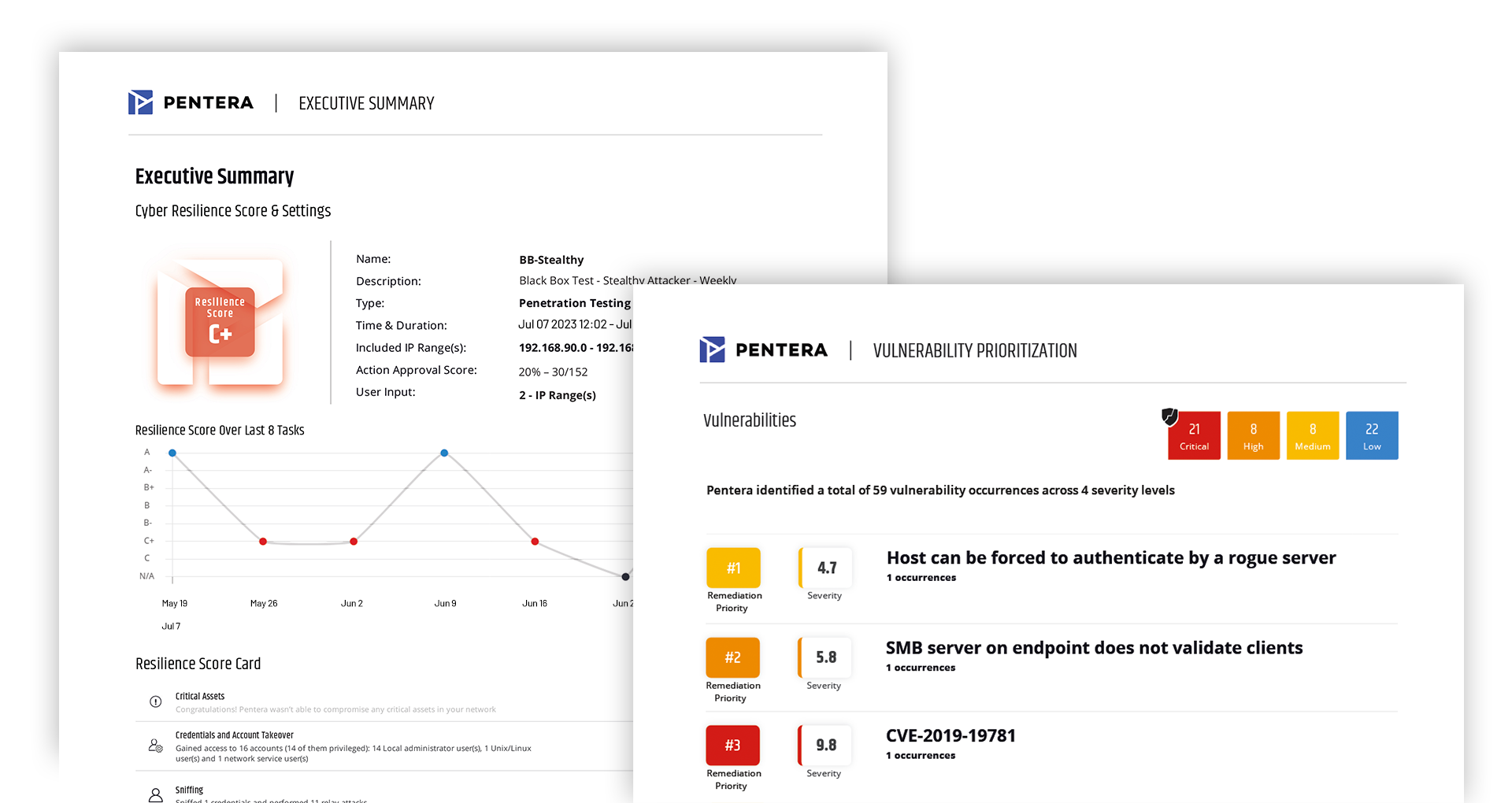
Close the risk-to-fix gap with AI-powered remediation workflows. Automate the process from security validation to resolution—deduplicating findings, assigning ownership, tracking SLAs, revalidating fixes, and delivering audit-ready proof of resolution.

Don’t assume. Validate.
Pentera Core
RansomwareReady™
Pentera Surface
Credential Exposure
Pentera Cloud
Test every surface.
Leave nothing to chance.
Validate every attack surface in your network, and test continuously to maintain control over your true security posture. Be proactive in fixing vulnerabilities, misconfigurations, leaked credentials, and privileges before they are exploited.
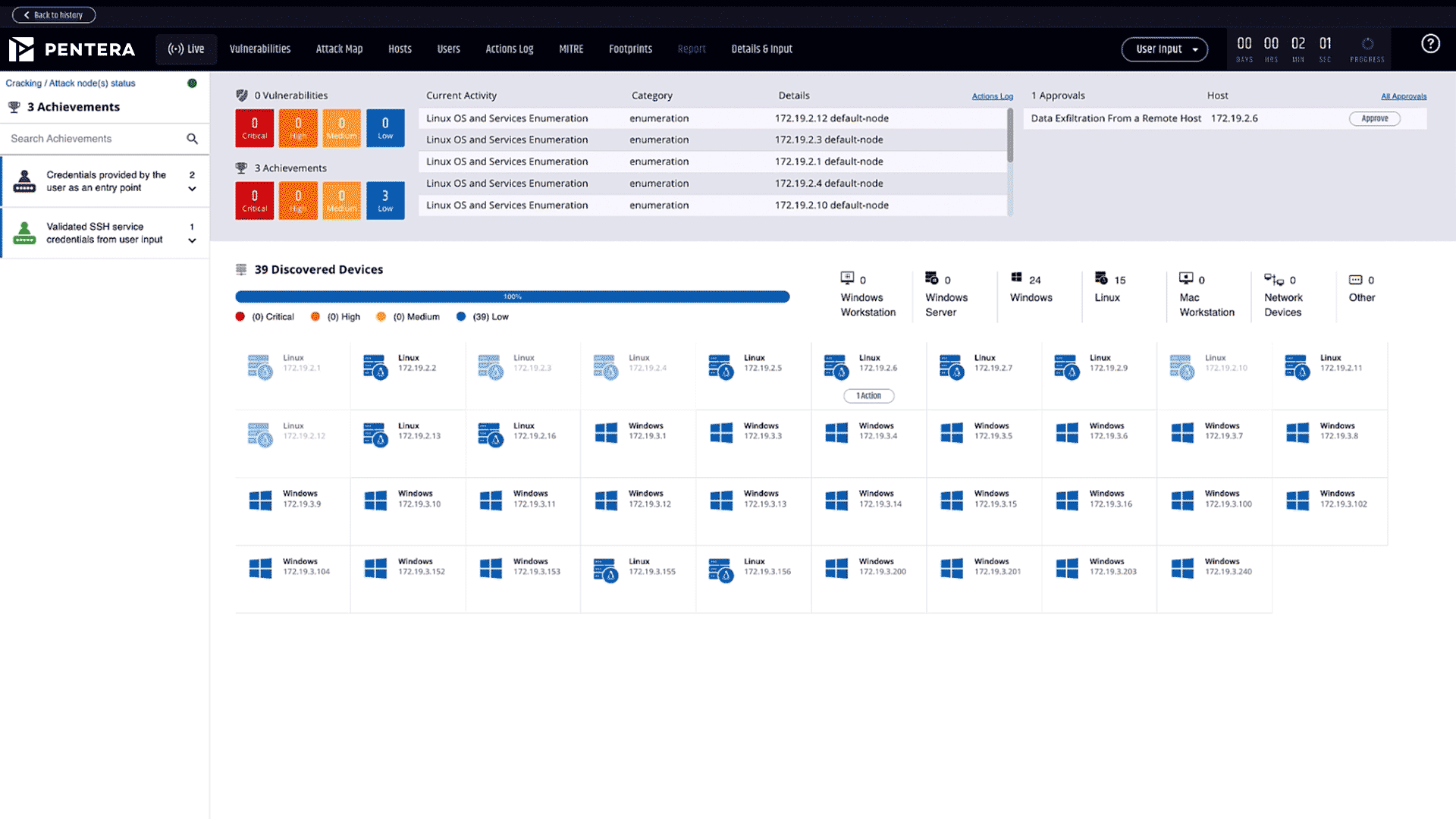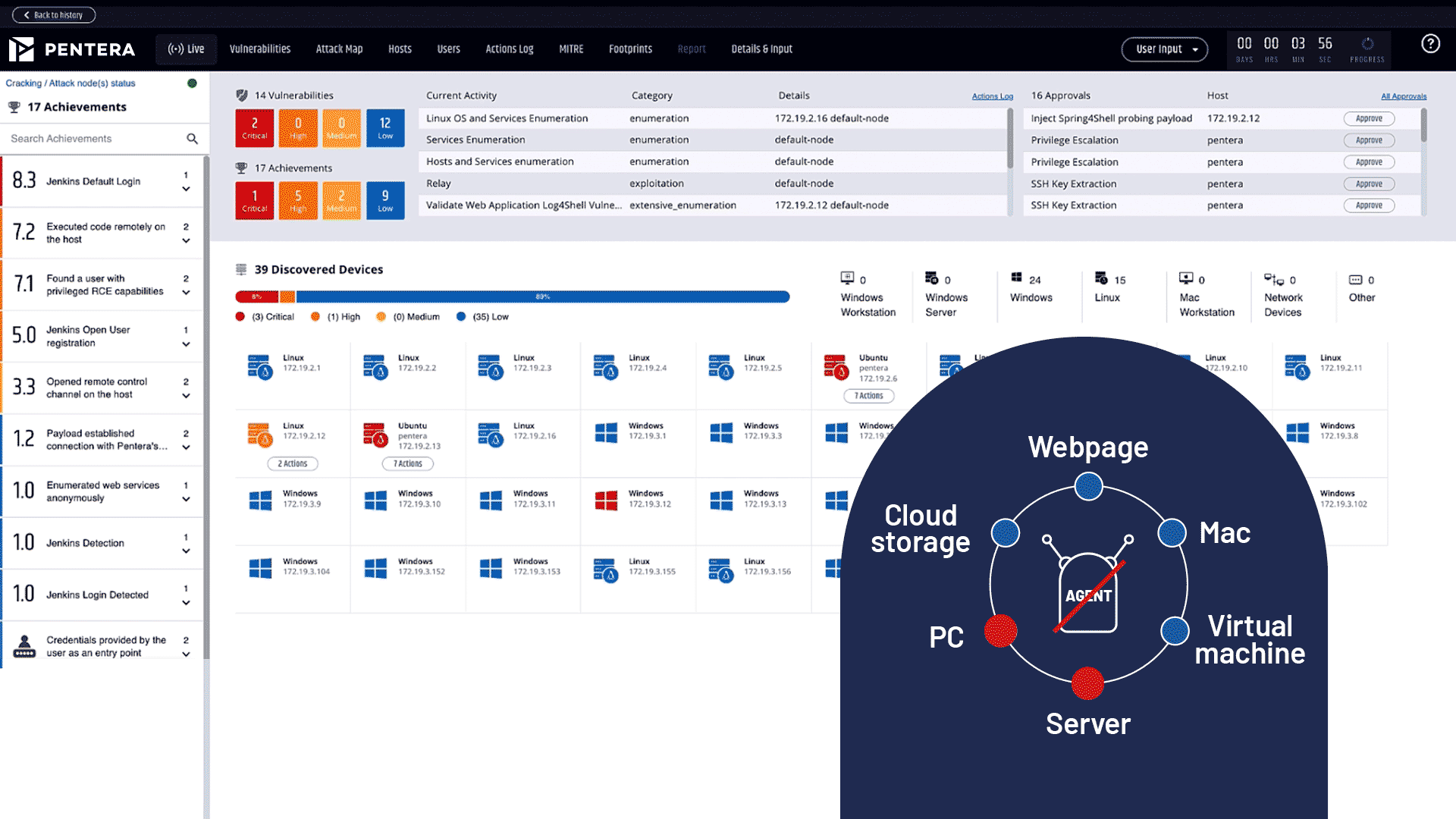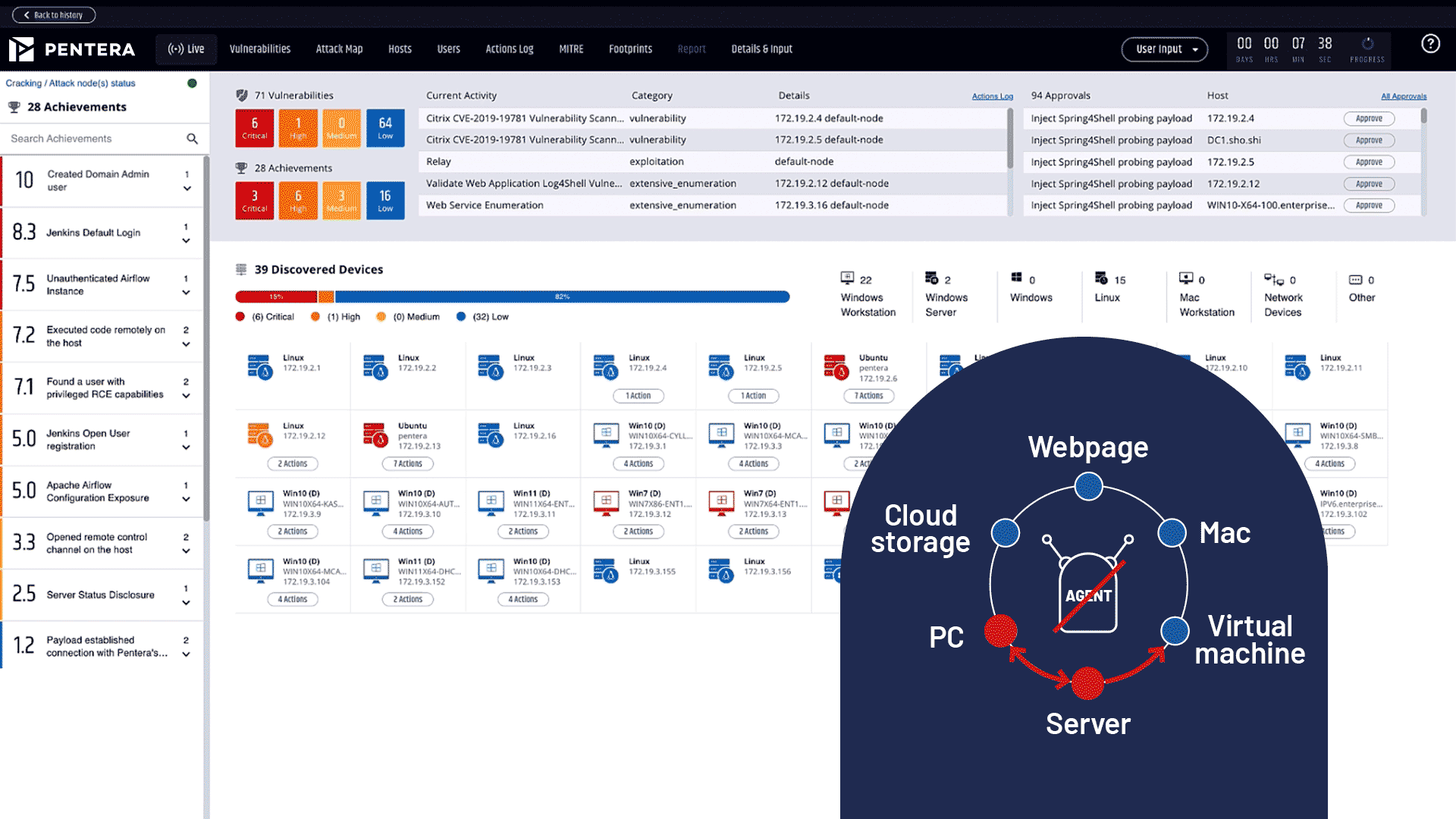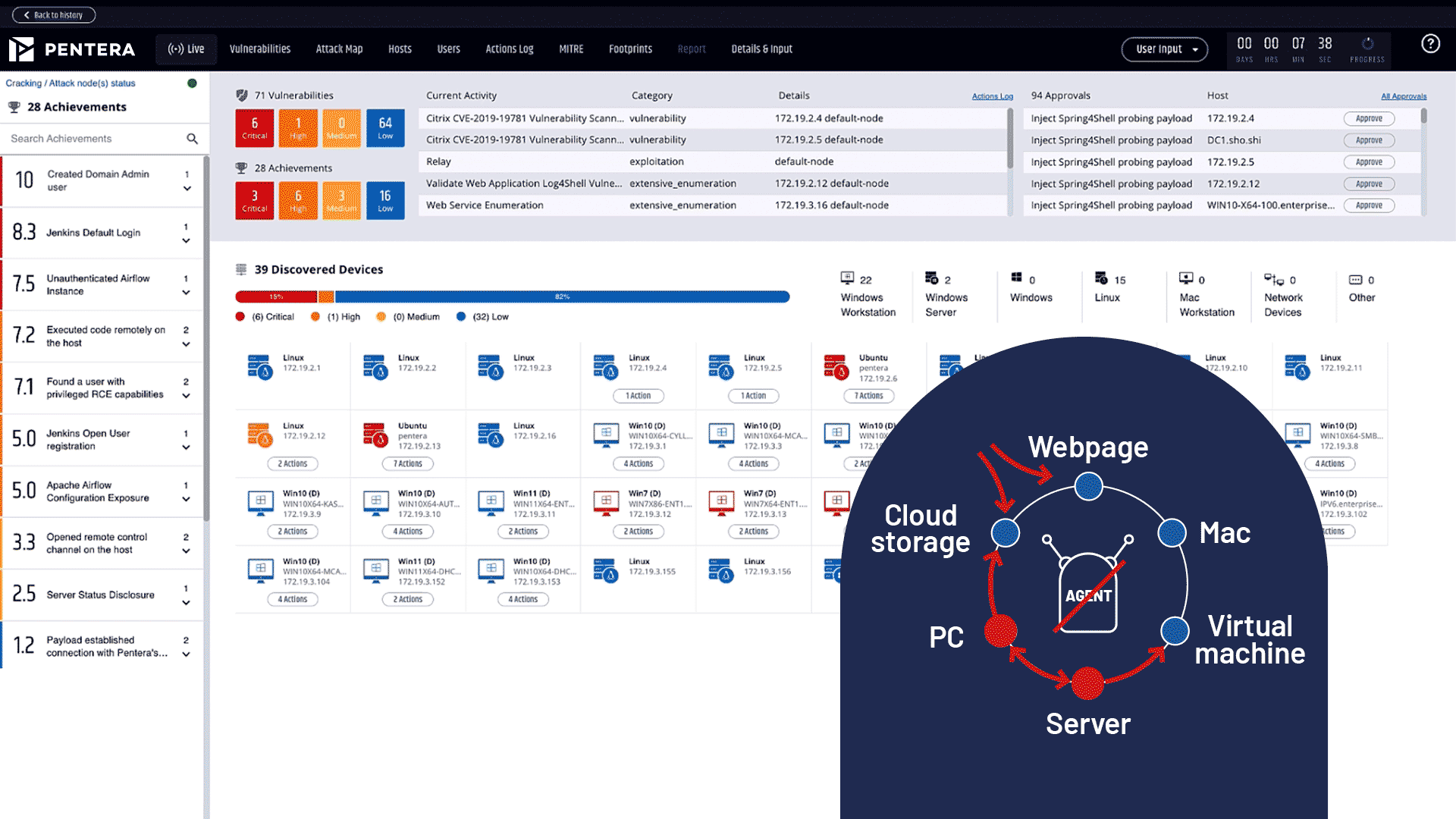

Challenge like an attacker.
Test everything about
your security controls.
Safely run real-world attacks in production with the widest range of techniques and the largest attack library. Access research-led attack scenarios that are aligned with the MITRE ATT&CK® framework.
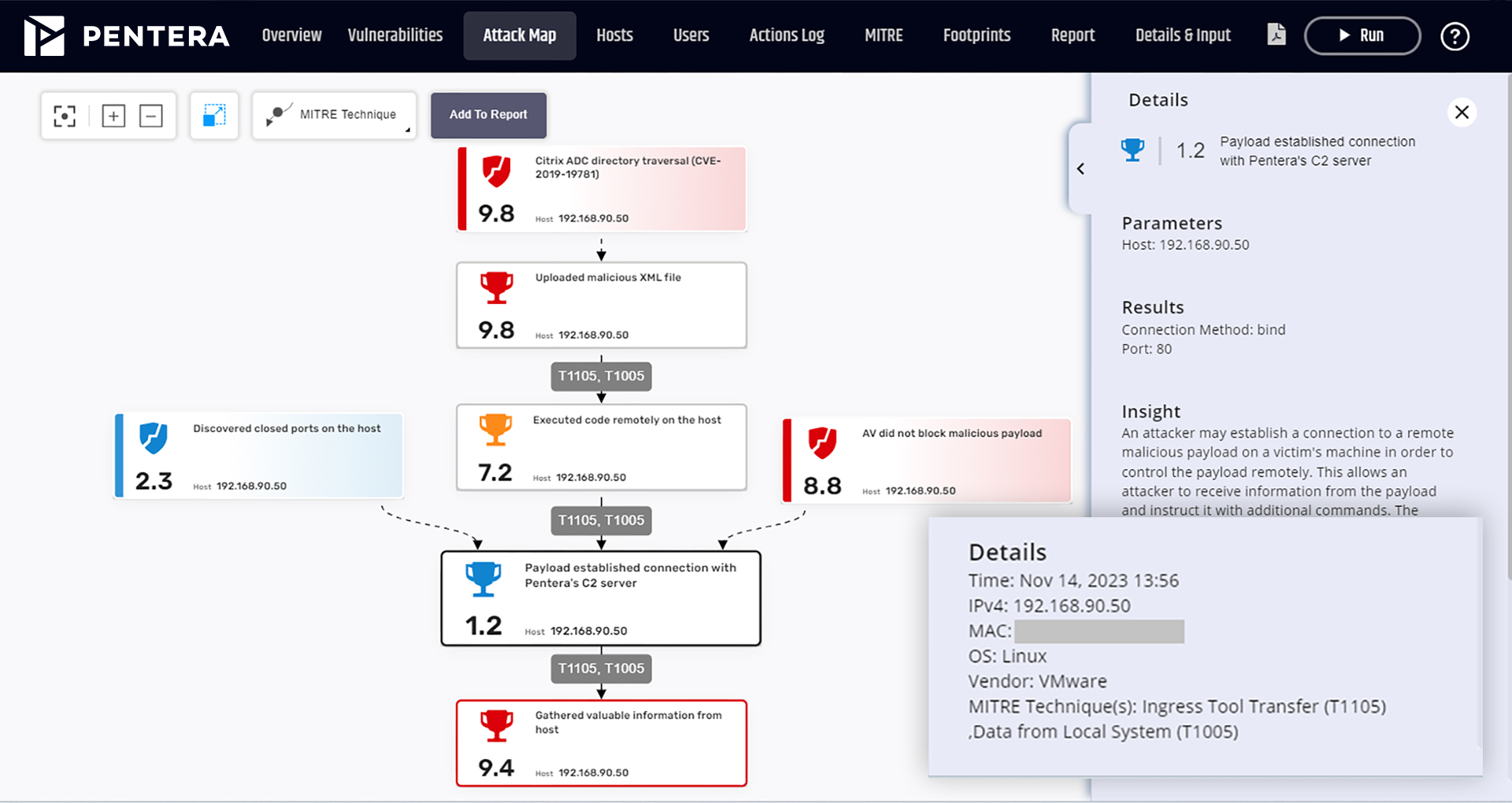
Discover how our platform
can make a difference for
your security.
Security Validation Updates: Stay Ahead of Emerging Threats
Pentera’s Cyber Pulse mechanism delivers frequent lightweight updates covering emerging high-profile CVEs and CISA KEV (Known Exploited Vulnerabilities), misconfigurations, and attack techniques. Now you can identify and prioritize remediation faster, report on your cyber status against new threats before they can be exploited, and maintain confidence in your security posture.
Helpful resources for smarter security validation.
FAQ
How safe is Pentera?
Pentera is built safe by design. All attack emulations are thoroughly vetted, non-destructive, and run in production without disrupting business operations or compromising data. The platform uses controlled payloads, automatically cleans up artifacts after testing, and follows strict cloud and on-prem pentesting policies. Its agentless architecture minimizes risk and complexity, enabling real-world validation, without causing harm.
What permissions do you need to provide to Pentera?
Pentera requires only the permissions necessary to safely emulate attacks in your environment. For internal and external testing, no agents are needed. For cloud validation, Pentera uses read-only API permissions aligned with provider pentesting policies to enumerate assets and configurations. If gray-box testing is desired, you can optionally provide standard user credentials to assess account-level exposures. All access is transparent, limited, and fully controlled by the customer.
What hardware configurations do you need to deploy Pentera?
Pentera is agentless and lightweight, requiring only a standard virtual or physical machine for deployment. Typical configurations include 8–16 CPUs, 64GB RAM, and ~1TB storage, depending on environment size and testing scope. It can be deployed on-premises or in the cloud, with scaling supported through distributed attack nodes for larger or multi-site infrastructures.
Will users feel a discernable impact when Pentera is operating?
No. Pentera is designed to run safely in production without disrupting business operations or user experience. Its attack emulations are non-destructive, controlled, and thoroughly vetted by cyber researchers. Payloads deployed during tests focus only on validating exploitability and are removed immediately afterward. Users continue their normal activities without noticing performance or availability issues, while security teams gain clear evidence of real exposures.
Does Pentera replace a VA tool?
No, Pentera helps you get more value out of your VA tool. Vulnerability Assessment (VA) tools scan for known flaws and provide long lists based on CVSS scores. Pentera doesn’t replace inventory function, it validates it. Pentera shows which vulnerabilities are truly exploitable in your environment, mapping full attack paths and prioritizing by business impact. Many organizations keep their VA for compliance while using Pentera to focus remediation on validated, high-risk exposures.
Does Pentera replace a BAS tool?
Pentera goes beyond BAS. While BAS tools run scripted, playbook-based attack simulations, Pentera autonomously emulates real-world adversaries in live production environments. It validates full attack paths, from initial access to impact, and provides evidence-based remediation guidance. Many organizations replace BAS with Pentera to gain deeper, continuous validation, while some use Pentera alongside BAS if compliance or specific simulation use cases are required.