AI-powered ransomware resilience validation
Know your backups
and defenses are ready
against ransomware.
Make sure your security is prepared to block and tackle ransomware attacks.
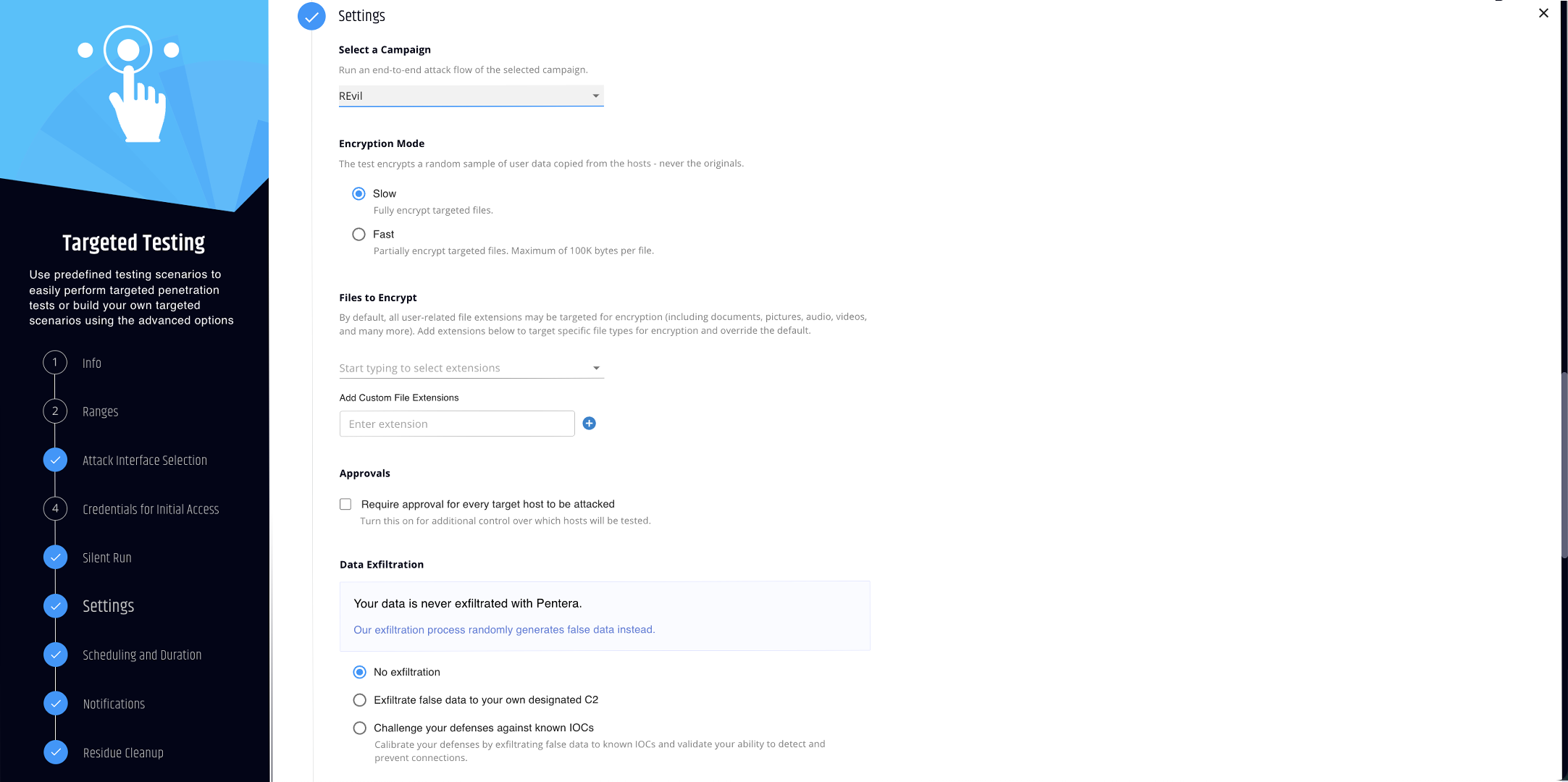
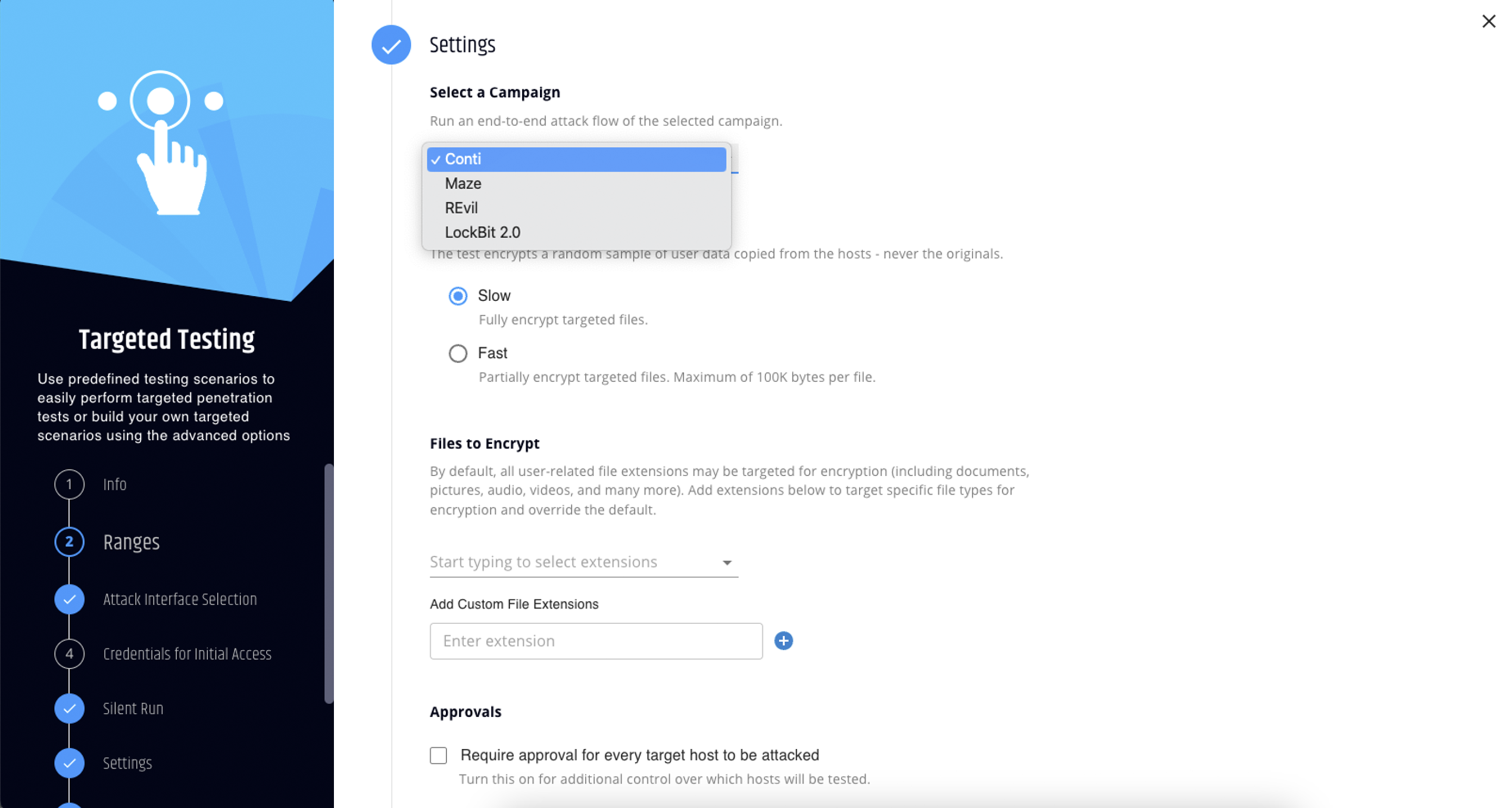
Validate the strength of your ransomware defenses.
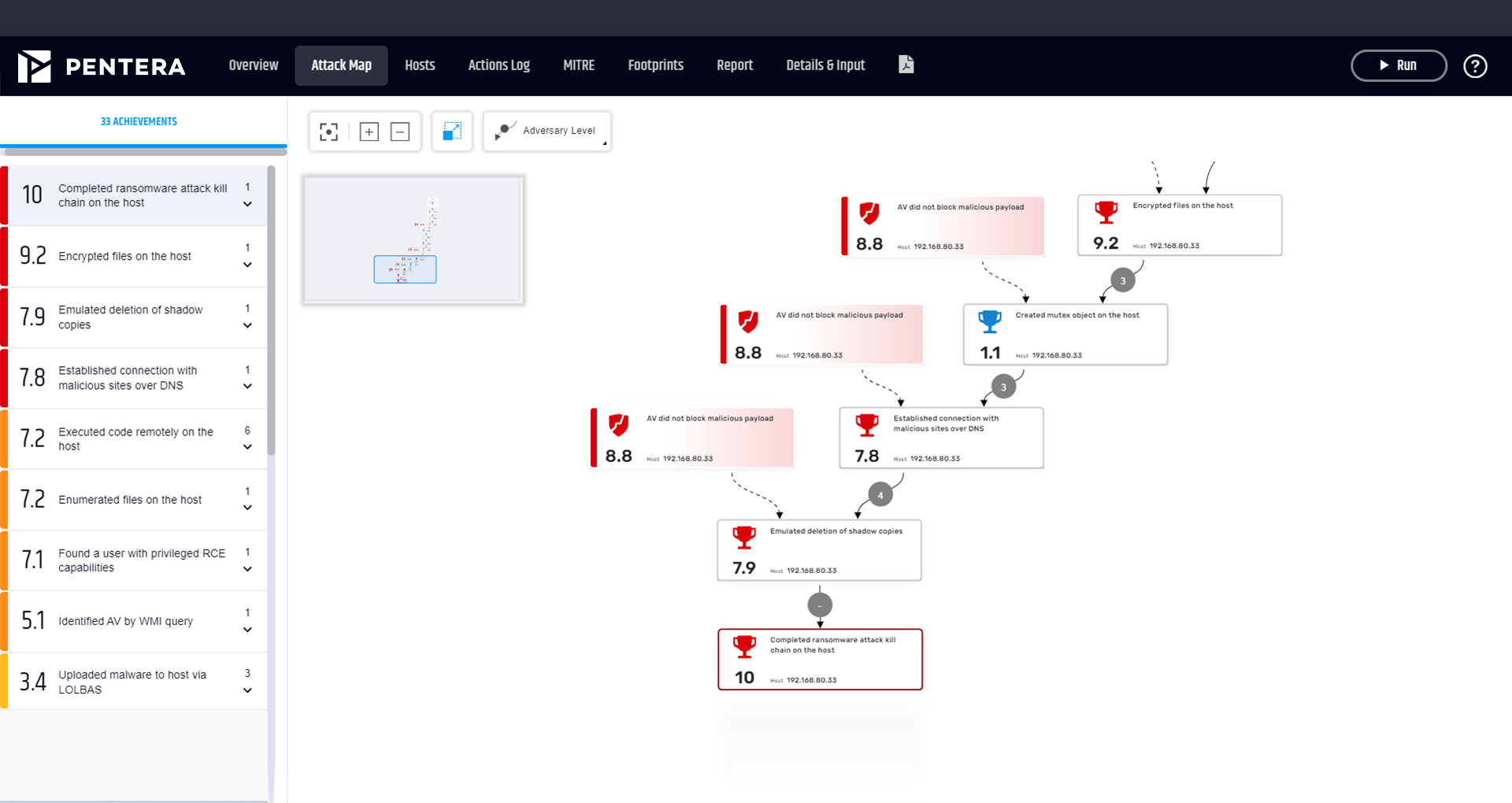
Run today’s most notorious ransomware attacks safely, in your own network. Use controlled methods to test the full attack kill-chain, from initial intrusion to C&C connection, encryption, and data leakage.
FAQ
What is the best protection against ransomware?
The best protection is validating that your security controls can detect, block, and contain real ransomware threats. Pentera safely emulates ransomware groups in your live environment, revealing exactly where your defenses fail, before attackers do. This proactive validation lets you fix exposures and confirm readiness.
What is the single most effective practice to counter ransomware?
The most effective practice is continuous validation of ransomware defenses. Cybersecurity professionals can run safe ransomware emulations to test endpoint protection, backup integrity, segmentation, and SOC response. You’ll know if you’re truly protected based on hard evidence.
What is the best backup strategy in the case of a ransomware attack?
The best strategy is a 3-2-1 backup model—3 copies, 2 media types, 1 offsite, but that’s not enough. You must also validate that backups can’t be encrypted or exfiltrated. It is possible to test ransomware kill chains and ensure your backups remain a viable recovery option under attack.
How much does ransomware protection cost?
Ransomware protection costs can vary widely depending on the tools and strategy used. Basic endpoint protection may cost a few dollars per device per month, while enterprise solutions, including EDR, backup, and network segmentation, can run into tens or hundreds of thousands annually. Costs also depend on organization size, complexity, and compliance needs. You can optimize the ROI of your ransomware protection strategy by routinely validating your defenses and ensuring their effectiveness against a ransomware attack.