Pentera RansomwareReady™
Answer the burning
question: Am I ransomware
defense ready
Eliminate ransomware exposure.
Ransomware defense validation in-depth.
Discover how our platform
can make a difference for
your security.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Helpful resources for smarter security validation.
FAQ
What are the hardware requirements for running RansomwareReady?
RansomwareReady runs on the same Pentera nodes used across the platform, with no special hardware required. A standard configuration of 8–16 CPUs, 64GB RAM, and ~1TB storage is typically sufficient, depending on the environment size and testing scope. The module is lightweight, agentless, and deployable on existing infrastructure, ensuring safe ransomware validation without additional hardware investment.
Does RansomwareReady require local admin rights to run, and how should teams handle the alerts it generates?
RansomwareReady runs with controlled permissions to emulate real-world ransomware behavior. While elevated privileges may be required for certain attack paths, all activity is safe and expected to trigger alerts. This is by design, validating whether your SOC detects and responds effectively. Security teams are advised to communicate test plans in advance to avoid confusion while still gaining full value from the exercise.
Does the target node for RansomwareReady need to be domain-joined, and does it require placement in a specific domain?
No. RansomwareReady does not require the target node to be domain-joined or tied to a specific domain. It operates from a Pentera node within your environment, safely emulating ransomware behavior across systems and shares. Placement is flexible so that nodes can be deployed wherever validation is needed, ensuring realistic testing without special domain dependencies.
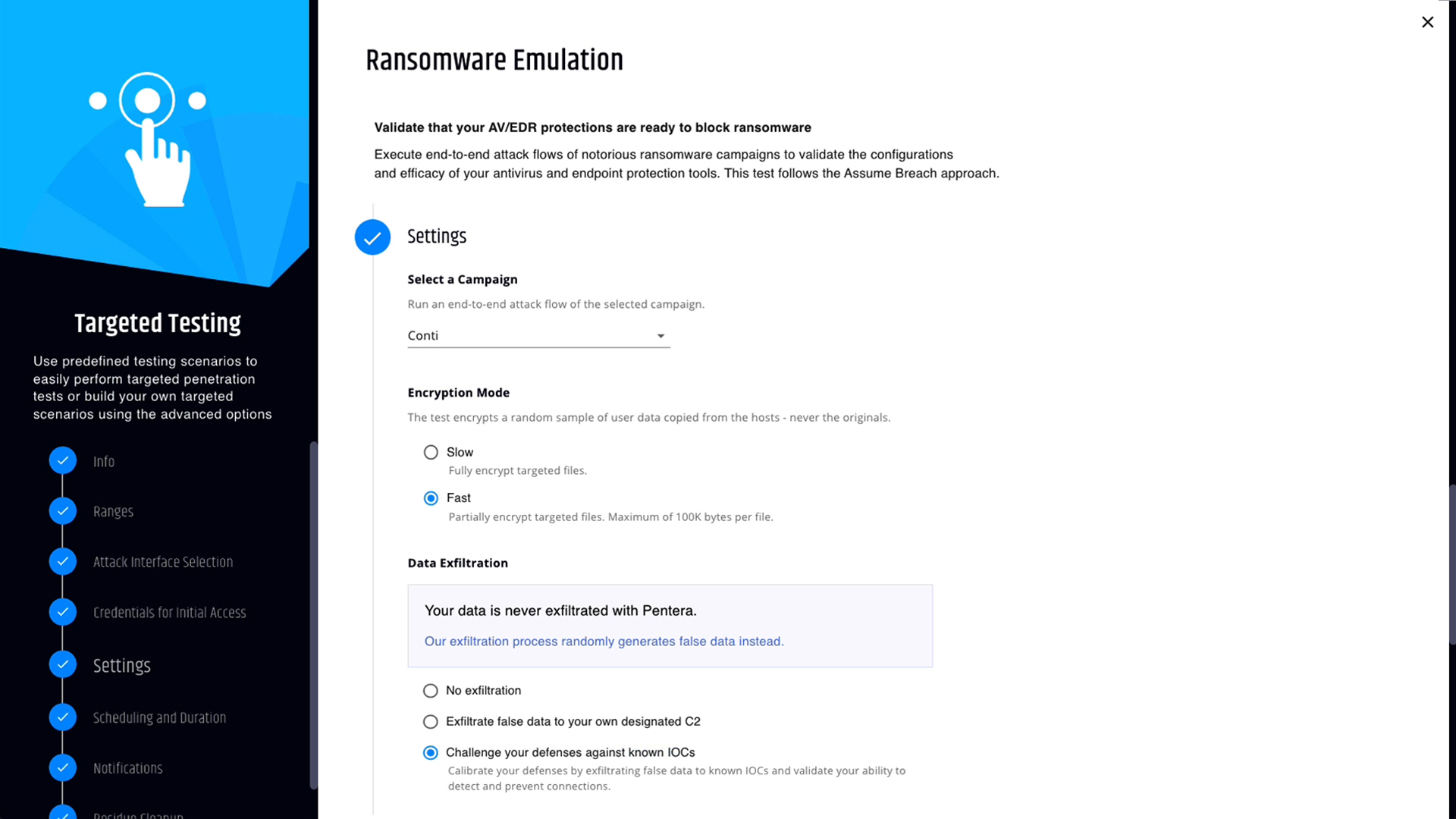
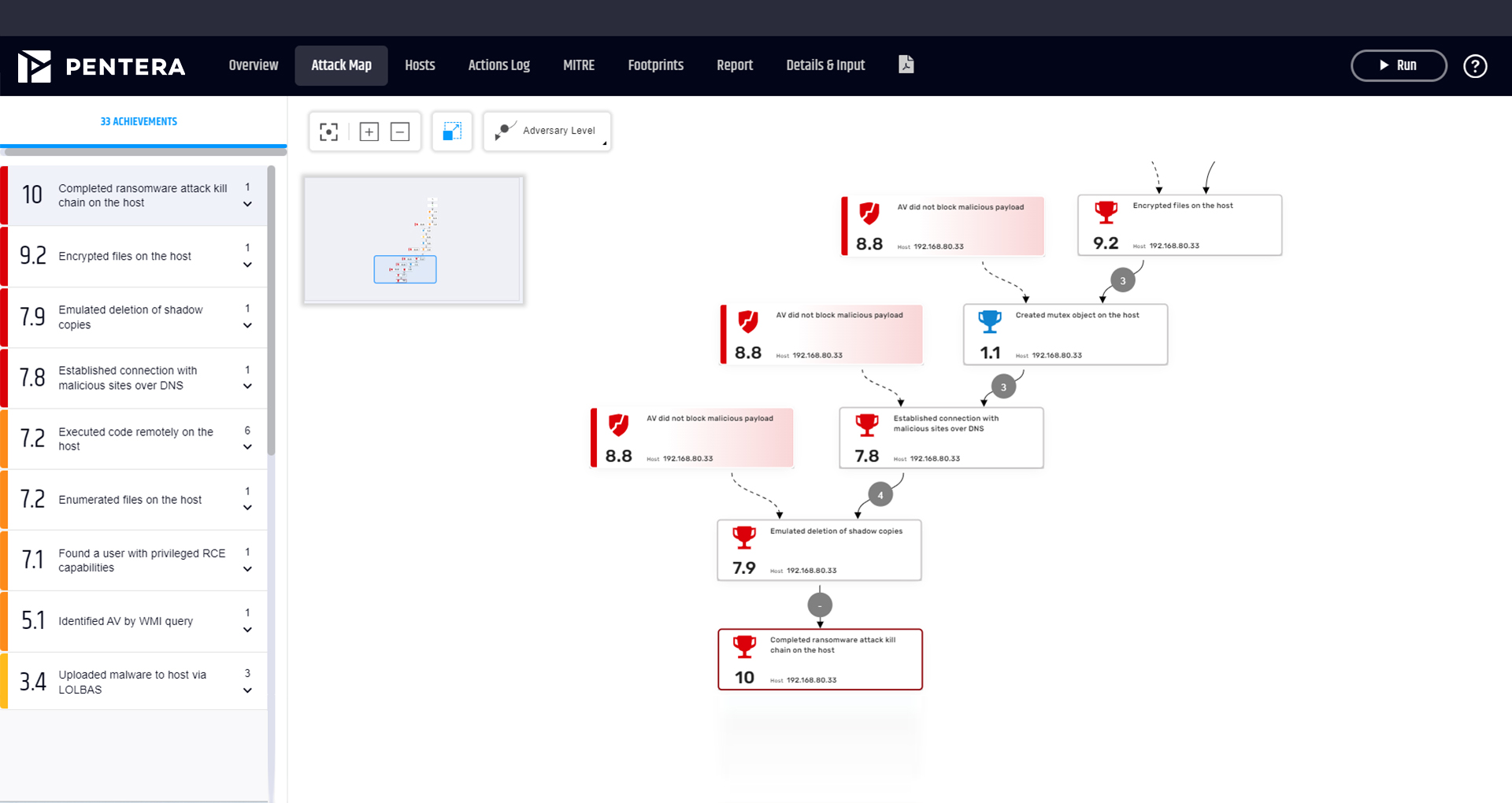
How does RansomwareReady emulate ransomware strains, does it use or update real hashes?
RansomwareReady uses safe, proprietary replicas of ransomware behaviors rather than live malware. It leverages continuously updated attack content from Pentera Labs, aligned with real ransomware groups, to emulate encryption, persistence, and propagation techniques. This approach validates detection and response without using actual malicious hashes, ensuring tests are safe, controlled, and non-disruptive.
Does Ransomware Ready encrypt files without disruption?
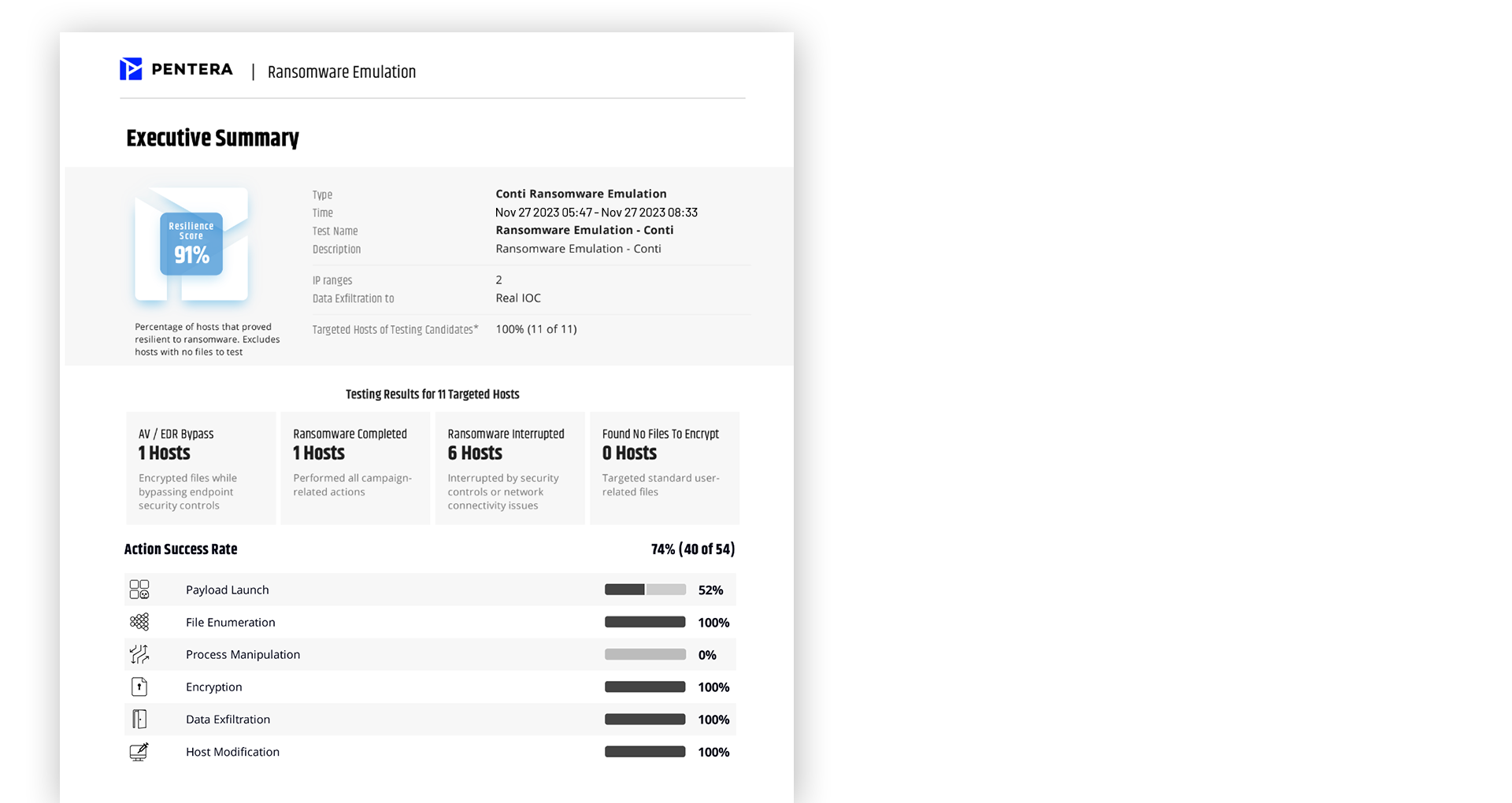
Pentera encrypts a duplicate of existing files to validate whether defenses can detect, block, and respond to a real ransomware attack, giving proof of resilience against ransomware without concern for business disruption.
Can RansomwareReady validate the security of Linux systems?
Yes. RansomwareReady can emulate ransomware behavior on both Windows and Linux systems. It safely tests common ransomware techniques across mixed environments, including Linux servers that often hold critical workloads.
Can RansomwareReady exfiltrate data out of the environment?
No. RansomwareReady does not exfiltrate data outside your environment. It safely emulates ransomware behaviors, including encryption and data theft techniques, but all actions are controlled and non-destructive. Instead of removing real data, it emulates the impact to validate whether your defenses can detect and respond.