Pentera Cloud
Explore doc topics
Datasheet
Pentera Cloud Automated Cloud Penetration Testing
Test and validate your cloud defenses to ensure continuous cyber readiness with Pentera Cloud. Identify exploitable misconfigurations, software vulnerabilities, exposed credentials, and excessive permissions across your cloud estate to guide remediation efforts based on true exposure.
Key Product Pillars
-
Cloud Attack Surface VisibilityRequiring no agents, Pentera continuously maps your cloud assets, identifying workloads, storage, databases and identities across all regions.
-
Cloud-Native Attack TestingPentera safely runs ethical penetration testing attacks, validating your resilience against MITRE ATT&CK cloud techniques.
-
Cloud to On-Premises TestingJust like an adversary, Pentera uncovers lateral attack paths between hybrid, on-premises and cloud environments.
-
Evidence-Based RemediationExploitable security gaps are prioritized based on business impact, with detailed remediation guidance.
1
Datasheet
Automating the Cloud-Native Attack Testing Lifecycle
Pentera safely performs all the actions an adversary would.
Vulnerability Assessment
Identify configuration flaws, vulnerabilities and exposed credentials across your cloud estate
Lateral Movement
Move between cloud assets and on-prem resources to broaden the threat actor's reach
Exfiltration & Impact
Emulate the outcomes of a successful cloud attack without compromising data or operational continuity
Reporting
Document findings for internal communication and remediation ticketing
Reconnaissance & Discovery
Automatically discover and enumerate your cloud assets
Privilege Escalation
Use collected credentials and compromised assets within data files to acquire elevated permissions, advancing the attack
Collection & Post Exploitation
Inspect compromised systems for additional vulnerabilities, then harvest cloud secrets and collect sensitive data for potential exfiltration opportunities
Remediation Guidance
Eliminate critical attack paths and prioritize fixing of identified security gaps based on true impact
Clean up
Remove data or code used in the test run to leave zero residual footprint
Reconnaissance & Discovery
Automatically discover and enumerate your cloud assets
Vulnerability Assessment
Identify configuration flaws, vulnerabilities and exposed credentials across your cloud estate
Privilege Escalation
Use collected credentials and compromised assets within data files to acquire elevated permissions, advancing the attack
Lateral Movement
Move between cloud assets and on-prem resources to broaden the threat actor's reach
Collection & Post Exploitation
Inspect compromised systems for additional vulnerabilities, then harvest cloud secrets and collect sensitive data for potential exfiltration opportunities
Exfiltration & Impact
Emulate the outcomes of a successful cloud attack without compromising data or operational continuity
Remediation Guidance
Eliminate critical attack paths and prioritize fixing of identified security gaps based on true impact
Reporting
Document findings for internal communication and remediation ticketing
Clean up
Remove data or code used in the test run to leave zero residual footprint
2
Datasheet
Find Exploitable Attack Paths in Hybrid Cloud
and On-Premises Environments
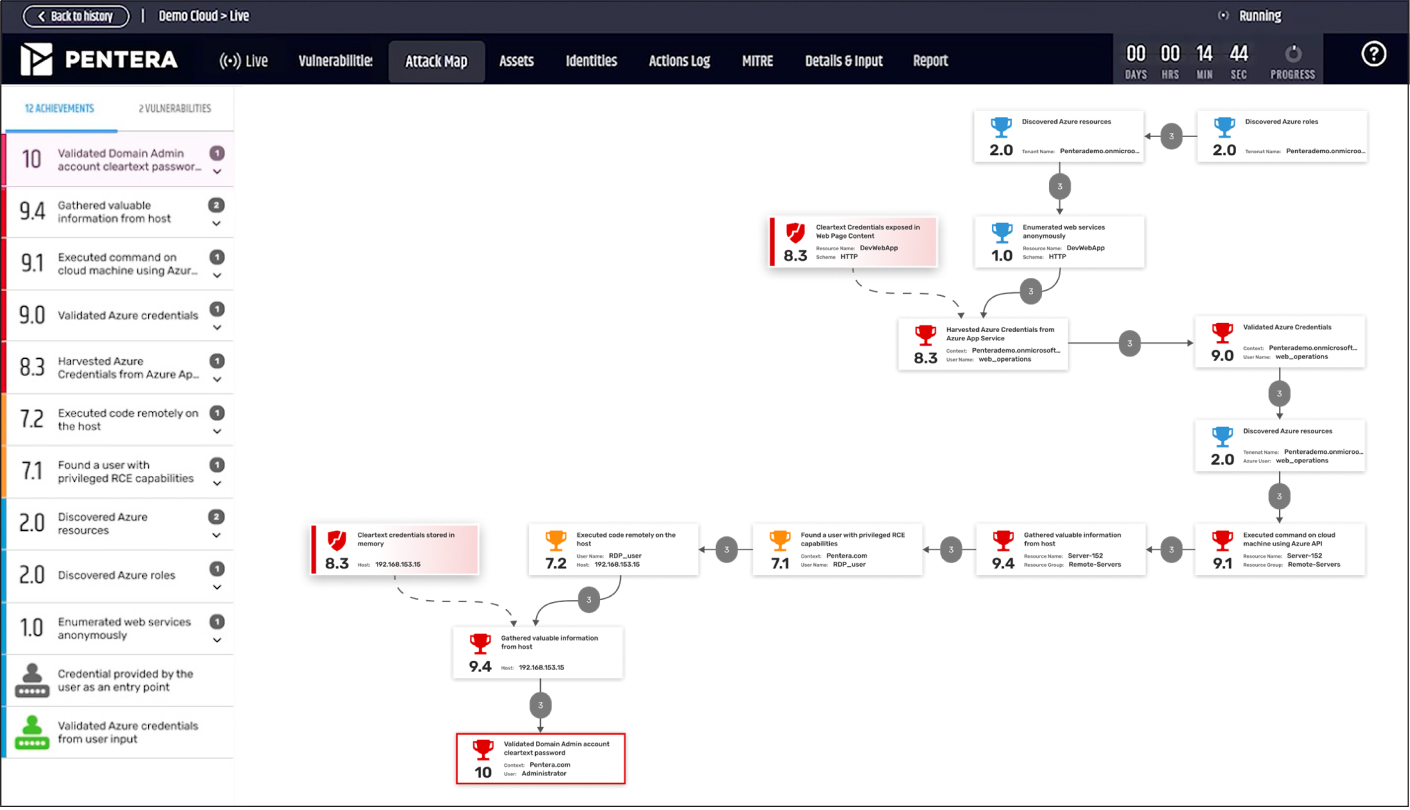

Benefits
-
Reduce cyber risk exposureIdentify and block exploitable attack kill-chains in your cloud environment.
-
Increase cybersecurity team efficiencyAutomate security validation testing activities across the entire attack surface.
-
Reduce third-party testing reliance and expensesMinimize cost and dependence on external cloud penetration testing services.
-
Accelerate time-to-remediationAddress critical cloud vulnerabilities and misconfigurations, mitigating risk before it materializes.
3
Datasheet
All your attack surfaces, tested continuously
with the Pentera Platform


About Pentera
Pentera is the category leader for Automated Security ValidationTM, allowing every organization to test with ease the integrity of all cybersecurity layers, unfolding true, current security exposures at any moment, at any scale. Thousands of security professionals and service providers around the world use Pentera to guide remediation and close security gaps before they are exploited.
4


