Pentera Credential Exposure
Explore doc topics
Datasheet
Pentera
Credential Exposure
Test for Cyber Identity Risks from
Stolen or Leaked Credentials
Stolen or Leaked Credentials
Harden Your Credential And Identity Attack Surface
Automate the discovery and testing of compromised identities against your internal and external attack surfaces. Know the real-world impact of leaked credentials and prioritize remediation to eliminate identity threat exposure.
Key Product Pillars
-
Continuous
FeedsReceive real-time leaked credential data from threat intelligence feeds and see how adversaries could potentially use these credentials against your infrastructure and applications. -
All Attack
SurfacesTest across all attack surfaces – internal, external, and cloud -
to identify exploitable active credentials. -
Multi-Format
TestingValidate leaked credentials in multiple formats, whether they are hashed, appear in clear text, in both full or partial user and login sets. -
Targeted
RemediationRetire compromised credentials, update password security policies, and trigger SOAR corrective action workflows.
1
Datasheet
How it works
Credential Intelligence
Collect leaked credential data associated with your domain. Monitor continuous feeds containing millions of credentials distributed in the open and dark web, including data recaptured from infostealers.
Remediation & Reporting
Receive detailed reports of findings for immediate action to reduce exposure. Retire active compromised credentials, trigger SOAR corrective workflows, and improve secure access policies.
Reconnaissance & Assessment
Map internal and external attack surfaces to identify potential points of compromise and credential exploitation opportunities.
Exposure Validation
Test leaked credentials against your attack surfaces using techniques like password cracking and credential stuffing. Map full attack paths to see potential impact.
Reconnaissance & Assessment
Map internal and external attack surfaces to identify potential points of compromise and credential exploitation opportunities.
Credential Intelligence
Collect leaked credential data associated with your domain. Monitor continuous feeds containing millions of credentials distributed in the open and dark web, including data recaptured from infostealers.
Exposure Validation
Test leaked credentials against your attack surfaces using techniques like password cracking and credential stuffing. Map full attack paths to see potential impact.
Remediation & Reporting
Receive detailed reports of findings for immediate action to reduce exposure. Retire active compromised credentials, trigger SOAR corrective workflows, and improve secure access policies.
Threat Intelligence
(Based on leaked credentials data sources)
2
Datasheet
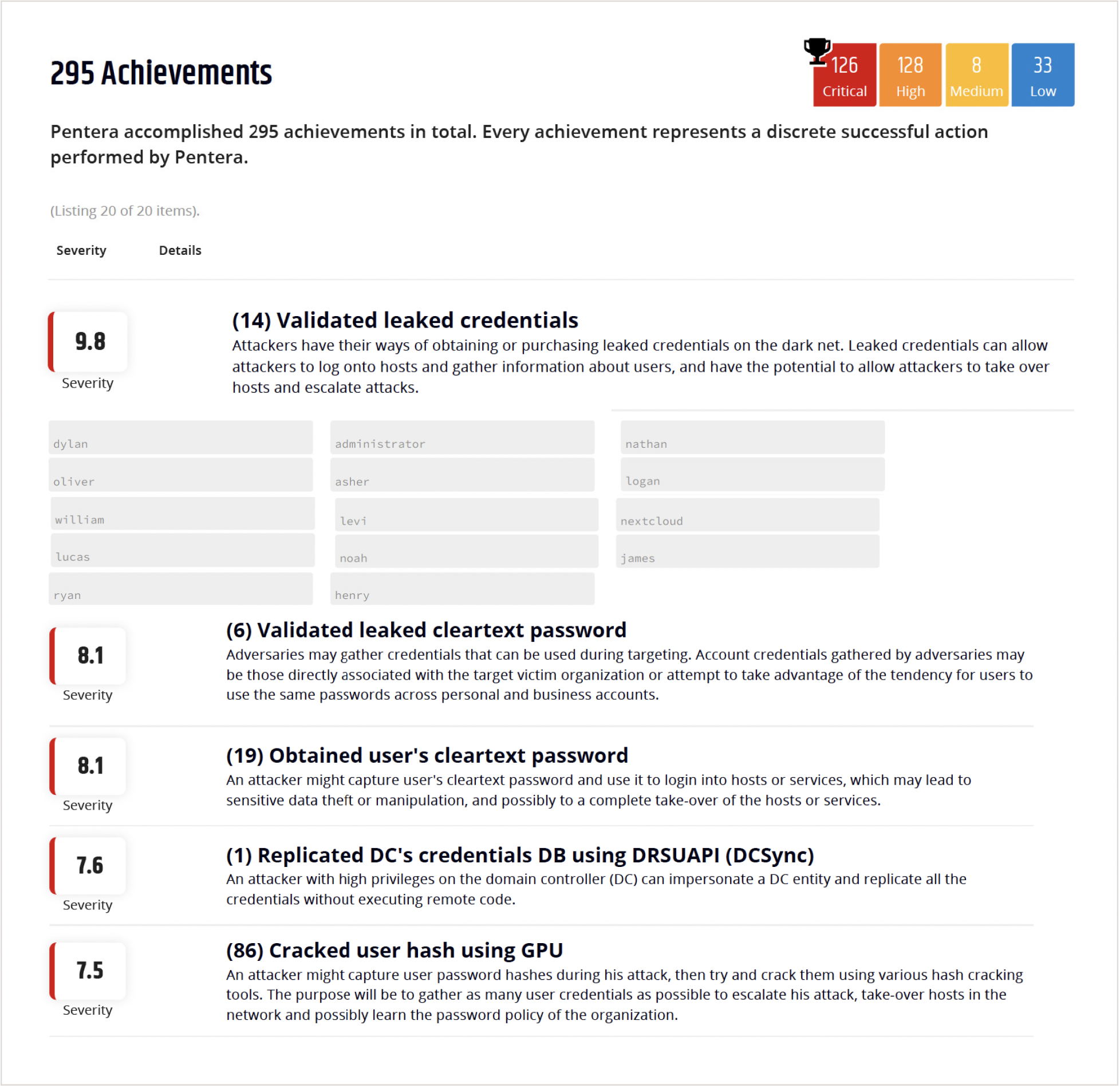
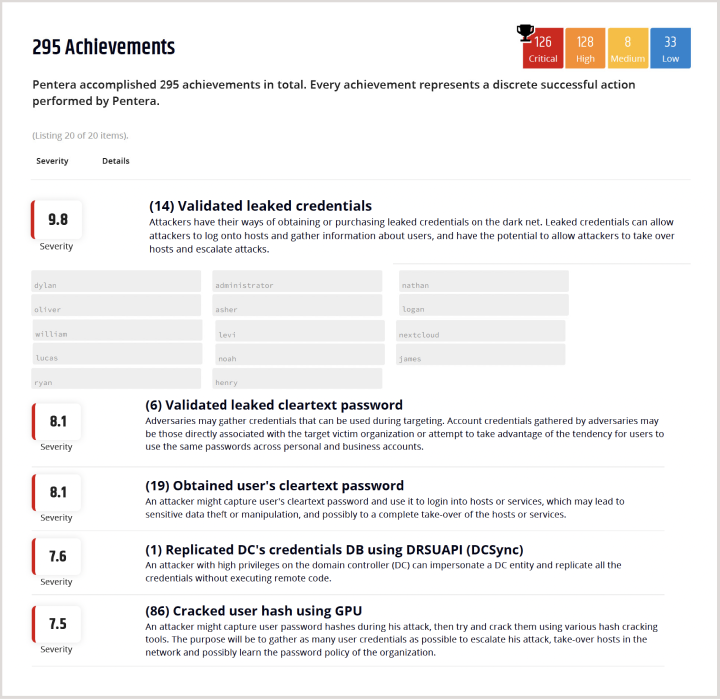
Benefits
-
Reduce cyber risk exposureBeat adversaries in identifying and remediating leaked and stolen credential exposures.
-
Reduce manual testing workEliminate the manual process of matching threat intelligence with active credentials.
-
Prioritize credential exposure based on true impactFocus on the 1% of leaked credentials that are proven to be exploitable.
3
Datasheet
All your attack surfaces, tested continuously
with the Pentera Platform
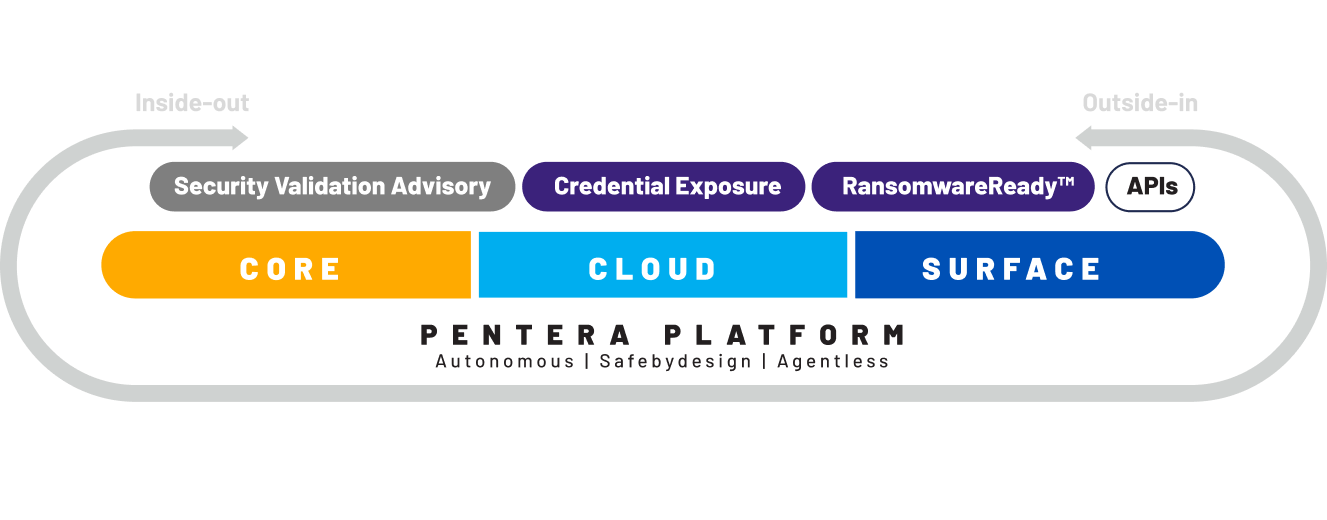
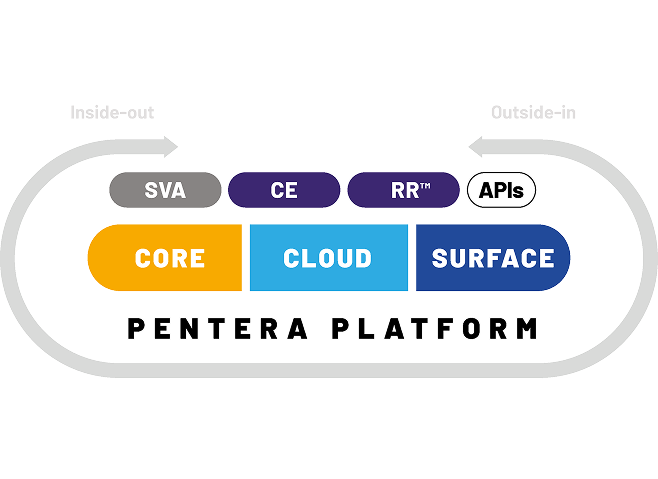
About Pentera
Pentera is the category leader for Automated Security ValidationTM, allowing every organization to test with ease the integrity of all cybersecurity layers, unfolding true, current security exposures at any moment, at any scale. Thousands of security professionals and service providers around the world use Pentera to guide remediation and close security gaps before they are exploited.
4


