Continuous
Threat Exposure Management (CTEM)
Key Capabilities
-
Continuous Attack Surface DiscoveryFind out where you are vulnerable by monitoring your internal, external, and cloud attack surfaces.
-
Impact-Based PrioritizationPrioritize proven exploitable security gaps based on their level of impact.
-
Exposure Validation TestingReveal complete attack kill chains and know the true impact of vulnerabilities in your live environment.
-
Surgical Remediation GuidanceEliminate critical attack paths with clear step-bystep guidance. Re-test to validate your security posture and confirm fixes.
Improve Your Cybersecurity Posture with CTEM
Continuous Threat Exposure Management (CTEM) is an emerging framework for ongoing proactive risk reduction. The goal of CTEM is to establish a systematic approach to identifying, prioritizing, and mitigating security vulnerabilities by continuously assessing and validating IT security posture. Organizations adopting CTEM can address potential risks early, adapt to evolving IT infrastructure and adversary techniques, comply with security policies and regulations, and enhance their resilience against cyber threats.
Gartner, “How to Manage Cybersecurity Threats, Not Episodes”, August 21, 2023
At the Core of CTEM:
Pentera’s Adversarial Exposure Validation
Adversarial exposure validation is a critical element within CTEM. It is essential for pinpointing true security gaps and ensuring defenses can withstand actual attacks, driving a resilient defense against cyber threats.
Pentera offers unparalleled depth and breadth in automated, algorithm-based attacks. Pentera’s platform conducts real attack techniques in live IT environments, ensuring safety by design. IT security, blue / red / purple teams, and SOC teams leverage Pentera to validate their cyber readiness anytime—daily, weekly, or monthly. Pentera provides detailed reports with actionable insights and step-by-step remediation guidance, enabling the effective identification and resolution of critical gaps.
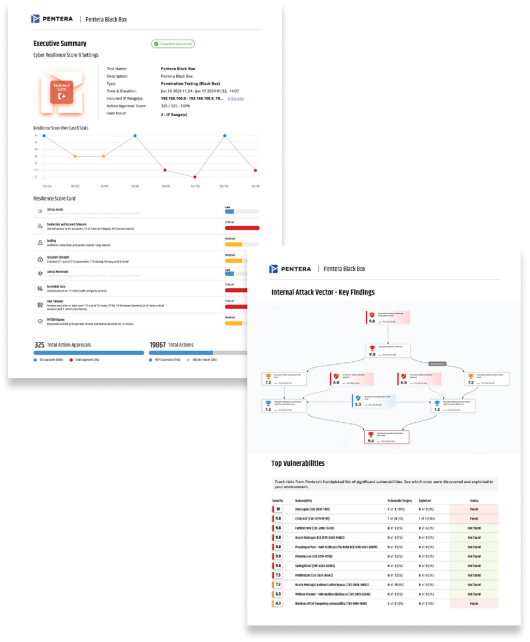
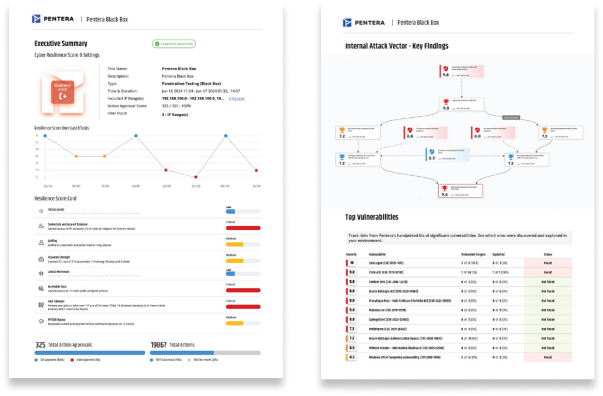
Pentera Supports All Stages of CTEM
Define the IT infrastructure segments and attack surfaces of focus for threat exposure management.
Pentera maps your IT environment and associated attack surfaces. See your internal, external-facing, and cloud infrastructure through the lens of an adversary to identify the areas with the highest risk exposure.
Identify assets, vulnerabilities, and potential threats within the defined scope.
Pentera automates reconnaissance, enumeration, and vulnerability scanning on defined IT scopes. Uncover software vulnerabilities, misconfigurations, exposed credentials, and other security gaps.
Rank vulnerabilities and threats based on risk and impact to the organization.
D o a Pentera finds exploitable vulnerabilities in your live environment that allow adversaries to compromise your critical assets. Prioritize the highest-risk vulnerabilities based on proven impact.
Test the effectiveness of security measures and remediation efforts.
Pentera runs complete attack kill-chains, mimicking the behavior of an adversary. Assess vulnerabilities and security controls’ effectiveness based on a true view of what attackers can achieve.
Implement improvements and adjust strategies based on findings and validations.
Pentera provides exposure insights and actionable remediation guidance on a continuous basis. Build collaboration and demonstrate continuous security posture improvement.
All your attack surfaces, tested continuously
with the Pentera Platform




