Virtual private networks (VPNs) have become widely used by enterprises for secure remote network access to protect sensitive data. This critical role has made VPNs attractive to threat actors, with more than half of enterprises attacked via VPN vulnerabilities in 2023. The FortiClient VPN reveals logging blind spots often exploited by adversaries. Comprehensive logging measures can mitigate these risks and reduce exposure to vulnerabilities like the Fortinet CVE-2024-47574 zero-day. Additionally, secure configurations and regular testing of VPNs can prevent adversaries from gaining unauthorized access, as shown in advanced VPN testing strategies.
With this in mind, we focused our research on popular VPN clients, including Fortinet’s VPN solution, a preferred choice for many enterprises. During this research, we developed a method to automatically validate credentials against Fortinet VPN servers. In the process, we uncovered a bug that attackers can exploit, potentially compromising the security of countless organizations.
We shared this information with Fortinet, and while they do not classify it as a vulnerability, they acknowledge the blind spot it creates. Pentera is releasing this to the broader security community as we believe this is a security flaw and recommend adopting a vigilant approach to enhance security awareness and visibility for these types of attacks on this widely used software.
In this article, we will share with you how we found a way to outsmart Fortinet’s logging mechanism and will provide a solution together with a fun, simple script to test against your own Fortinet VPN server.
It all began in a beautiful, yet ordinary sprint.
The impetus for our research arose from our efforts to create an automatic credential validation system for Fortinet VPN. To address this, we attempted to establish a connection with the server using clients such as OpenConnect. Unfortunately, this approach proved unreliable for automation, prompting us to delve deeper into the communication protocols between the client and the VPN server.
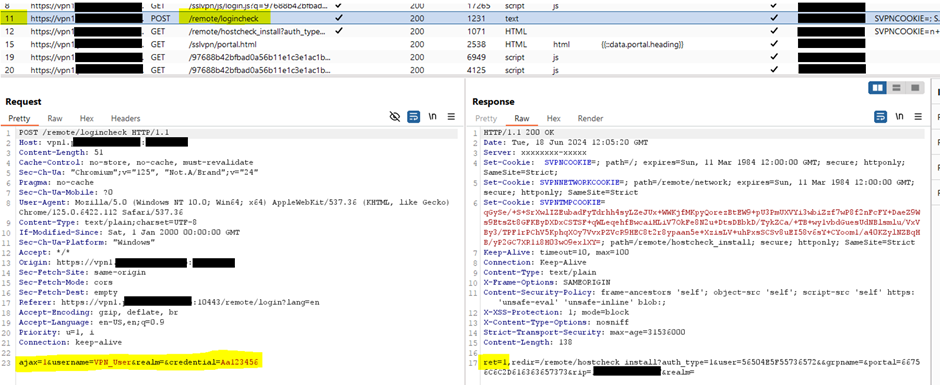
We began by recording the interactions between the client and the VPN server using Burp Suite. Through detailed research, we discovered that a simple HTTPS request initiates the authentication attempt against the server. This discovery was pivotal as it allowed us to understand the initial stages of the authentication process.
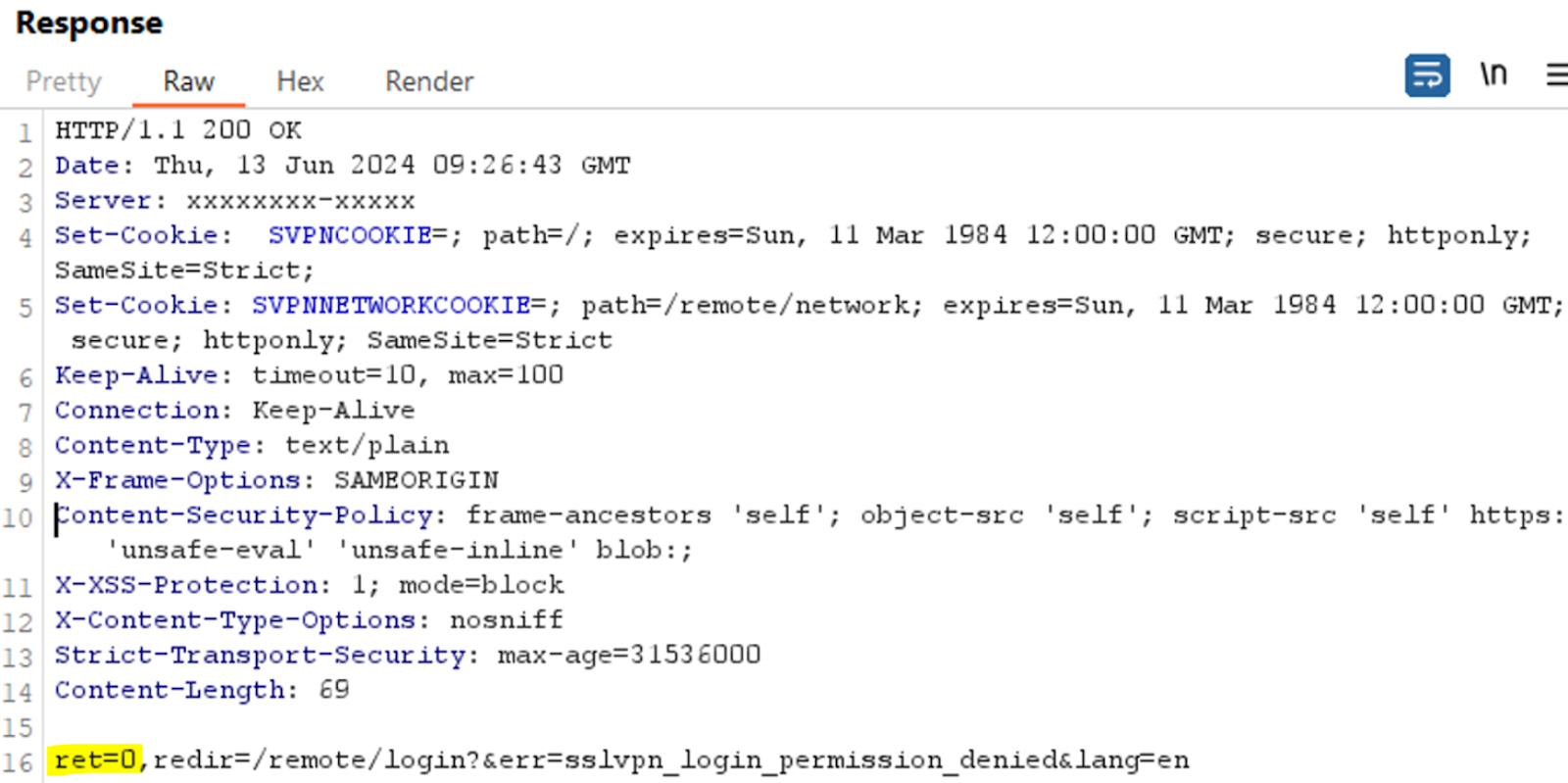
We noted that the server’s response to the initial HTTPS request can determine one of three outcomes: valid credentials, failed authentication, or a throttling error due to too many consecutive failed attempts. This response is crucial as it provides immediate feedback on the status of the authentication attempt.
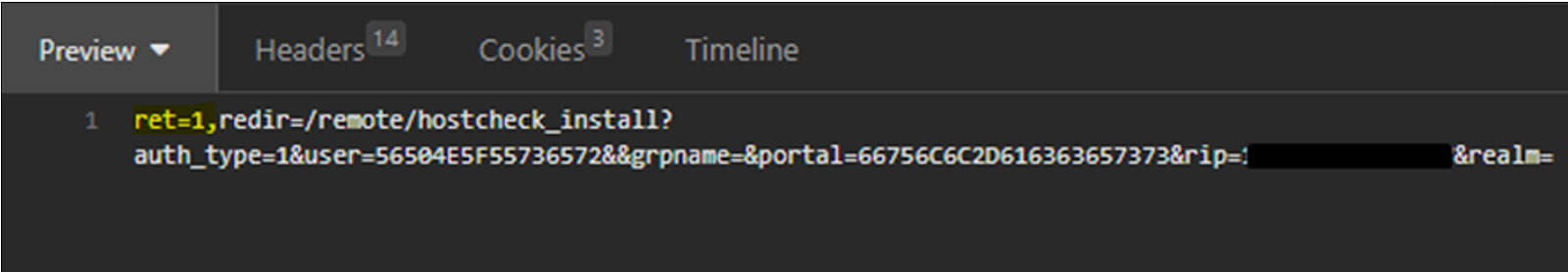
Successful Login represented by ret=1:
Burp Suite example
Our proof-of-concept Insomnia example
Failed Login represented by ret=0:
So what?
To this point, we had enough to continue with our development of an automated validation process using the initial response as the differentiator and to determine the validity of the user. As responsible researchers, we wanted to understand how this method impacts the incident response (IR) teams for our customers who use this solution. We expected to see a lot of logs and alerts identifying our repeated multiple authentication attempts.
However, upon logging into the VPN server, we only found logs for failed log-in attempts. This discovery was surprising, as it indicated that IR teams monitoring Fortinet VPN usage, cannot differentiate between a failed and a successful brute-force attempt. This means that if an attacker were to use the technique we discovered, the successful login could go undetected, potentially leaving their network compromised.
Allow me to explain, in a typical brute-force attempt, a successful login to the VPN would generate a log entry. However, this log is only recorded after the authorization phase, which follows the authentication phase. While authentication verifies the credentials, authorization is required to establish the VPN session. Consequently, if an attacker is solely attempting to validate legitimate credentials, they can achieve this by passing the authentication step alone, avoiding authorization. This method allows them to confirm credentials without generating a log entry, effectively keeping their brute-force activity undetected.
Is it dangerous?
The inability to log successful authentication attempts at the authentication phase presents a significant security risk. Attackers could potentially exploit this vulnerability to conduct brute-force attacks without a detection of their successful attempts. Additionally, an attacker with a bank of leaked credentials could quickly determine which are valid VPN users without exposing those users.
In a properly configured logging system, a professional Incident Response (IR) team can notice that after many failed attempts, a successful one means the brute-force attempt was successful and creates a call-to-action to reset the user’s password. However, in this case, since successful attempts are not logged, the IR team might think that the whole attack has failed and will not be able to identify the compromised credentials that require a password reset. Meanwhile, the attacker can leverage this gap to authenticate with the compromised credentials at another time, disguise their behavior as legitimate, or sell the compromised credentials on the dark web.
WIFM
First of all, we still recommend that Fortinet enhances its logging mechanisms to mitigate this issue. Specifically, the system should log all authentication attempts, regardless of their outcome, at the earliest stage. This would enable administrators to monitor and respond to suspicious activities more effectively.
In the interim, Fortinet VPN users should implement additional security measures, such as multi-factor authentication (MFA) and strict monitoring of authentication logs. Regular audits and updates to the VPN system are also recommended to ensure ongoing security. Our research also found that after a few minutes, a log of “SSL tunnel shutdown” was created for users who were validated, so theoretically, a detection could be devised based on users with an “SSL tunnel shutdown” log without an “SSL tunnel established” log before it. Additionally, a Web Application Firewall (WAF) before the VPN server could potentially detect these kinds of attacks as well.
As promised, we created a simple script to help you test the vulnerability against your own Fortinet VPN server: Fun AIY (Attack It Yourself) script – happy hacking 🙂
Cybersecurity never sleeps
Our research into the Fortinet VPN vulnerability underscores the importance of continuous vigilance in cybersecurity. By identifying and addressing potential weaknesses, we can help safeguard sensitive data and maintain the trust of users in these critical systems. The cybersecurity community must work collaboratively to share findings and develop robust solutions to emerging threats.
For any questions on this research, please reach out to [email protected].