The version of an MSSQL database provides valuable information that cyber attackers can exploit. With the version details in hand, they can attempt to find and exploit any of the version’s known vulnerabilities. As part of our research at Pentera Labs, we attempted to obtain the version of the widely-used MSSQL (Microsoft SQL Server) database.
The TDS protocol is is critical for secure communication with an MSSQL database, as it handles authentication and queries. Misconfigurations can lead to critical vulnerabilities that compromise systems, such as improper database credential management or overly permissive access controls. Proper validation can reduce these risks and help maintain secure database configurations. Explore this guide on database vulnerabilities to understand common risks.
In this blog post, we show how we detected the version with the TDS protocol, without having to authenticate. To read a more in-depth explanation of the steps we took, you can read the entire research paper here.
What is the TDS Protocol in an MSSQL Database?
The Tabular Data Stream (TDS) protocol is an application layer protocol for communicating with databases – from authentication all the way to querying. By using TDS, researchers can obtain a database’s version. To do so, they can use the “Pre-Login” sequence, which includes sending data to the server and getting a reply with the version information. Understanding the Pre-Login packet is vital for analyzing how attackers extract version details from an MSSQL database. Learn more about securing your MSSQL database.
Analyzing the Pre-Login Packet in MSSQL Databases
The Pre-Login packet consists of tokens. These tokens provide information about the database. The Version token contains the information we need. Its type is 0x00.
The Version Token’s data is made of 6 bytes:
- Major version (first byte, unsigned long)
- Minor version (second byte, unsigned long)
- Build (third and fourth bytes, unsigned short)
- Minor build (fifth and sixth bytes, always zero therefore redundant, unsigned short).
The first four bytes of the Version Token provide the database version.
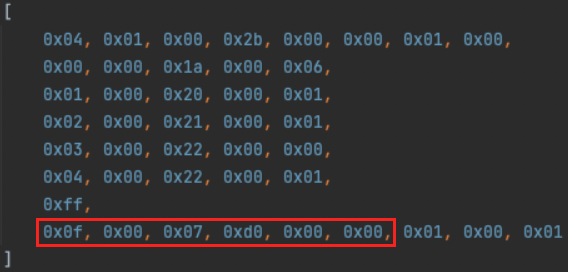
Here’s an example of the data sent back from the server. The six bytes with the version information are highlighted:
A simple code is enough to extract the version from these four bytes:
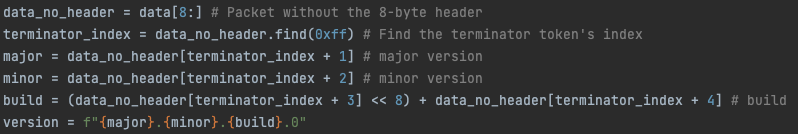
The result we received is the database’s version. In this case: 15.0.2000.0
Mitigating Vulnerabilities in MSSQL Databases
The ability to detect the database’s version with the TDS protocol relies on the database’s port being open and accessible. Therefore, mitigation involves restricting access to the port. This can be done with firewalls, iptables and host-based firewalls.
To learn more about mitigation strategies and for a detailed explanation of how we leveraged the TDS protocol, read the complete paper.