Pentera Cloud
Know your true exploitable
cloud exposures (in a rapidly
changing environment).
Build up your cloud defenses.
Automated cloud penetration testing.
Discover how our platform
can make a difference for
your cloud security.

Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Helpful resources for smarter security validation.
FAQ
Does Pentera Cloud perform security validation for PaaS, IaaS, and SaaS?
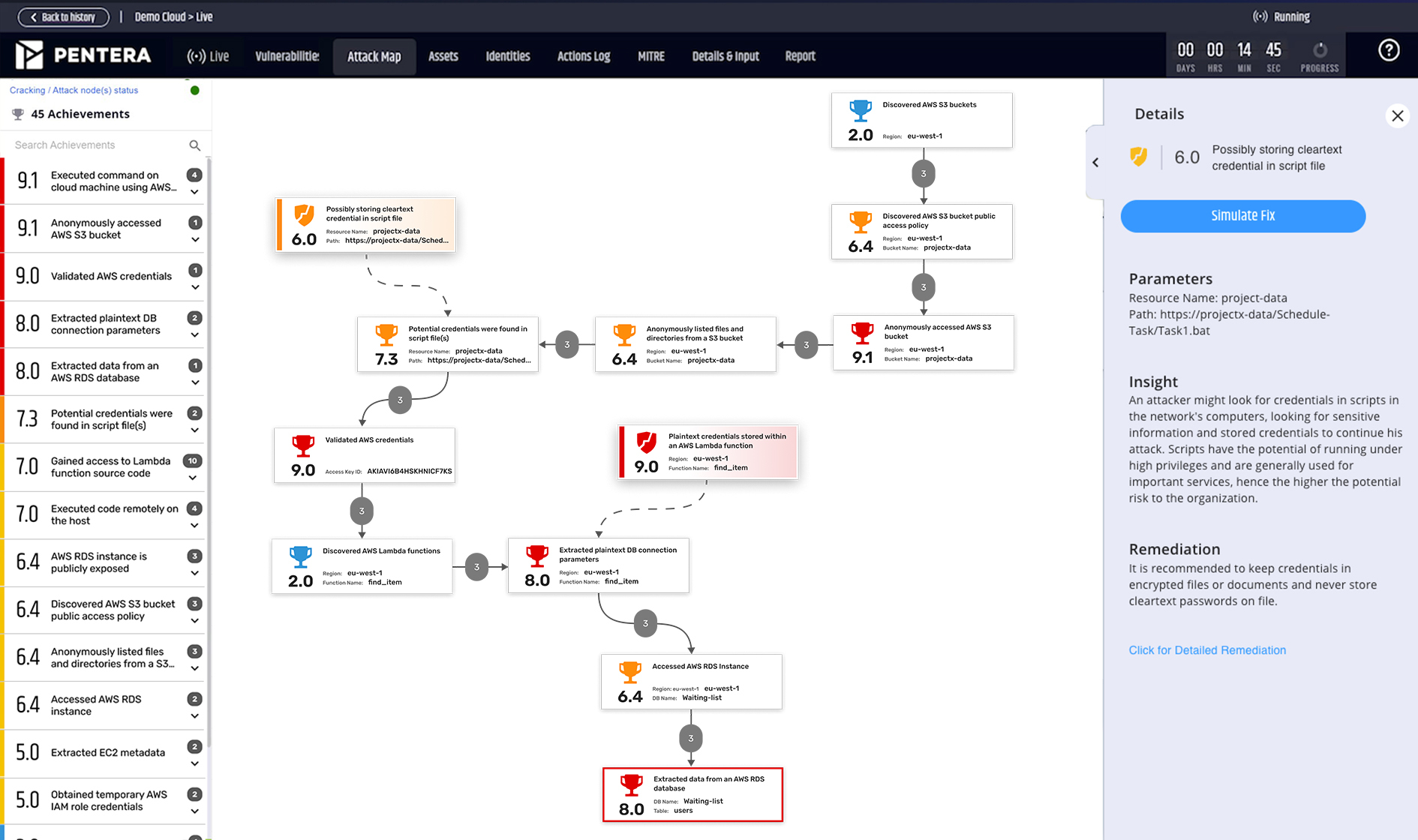
Pentera emulates attacks on various cloud services, mimicking the techniques an adversary would employ to compromise an organization. For SaaS applications, Pentera attempts token hijacking and other methods to bypass authentication and gain unauthorized access. For IaaS services, Pentera tries to infiltrate and manipulate virtual machines, storage, databases, and other infrastructure components to actively progress an attack.
Throughout all testing, Pentera strictly follows AUP rules for penetration testing set by cloud providers. This ensures Pentera actions cannot disrupt or impact the normal operation of your cloud environment. Safety-by-design is a core principle at Pentera.
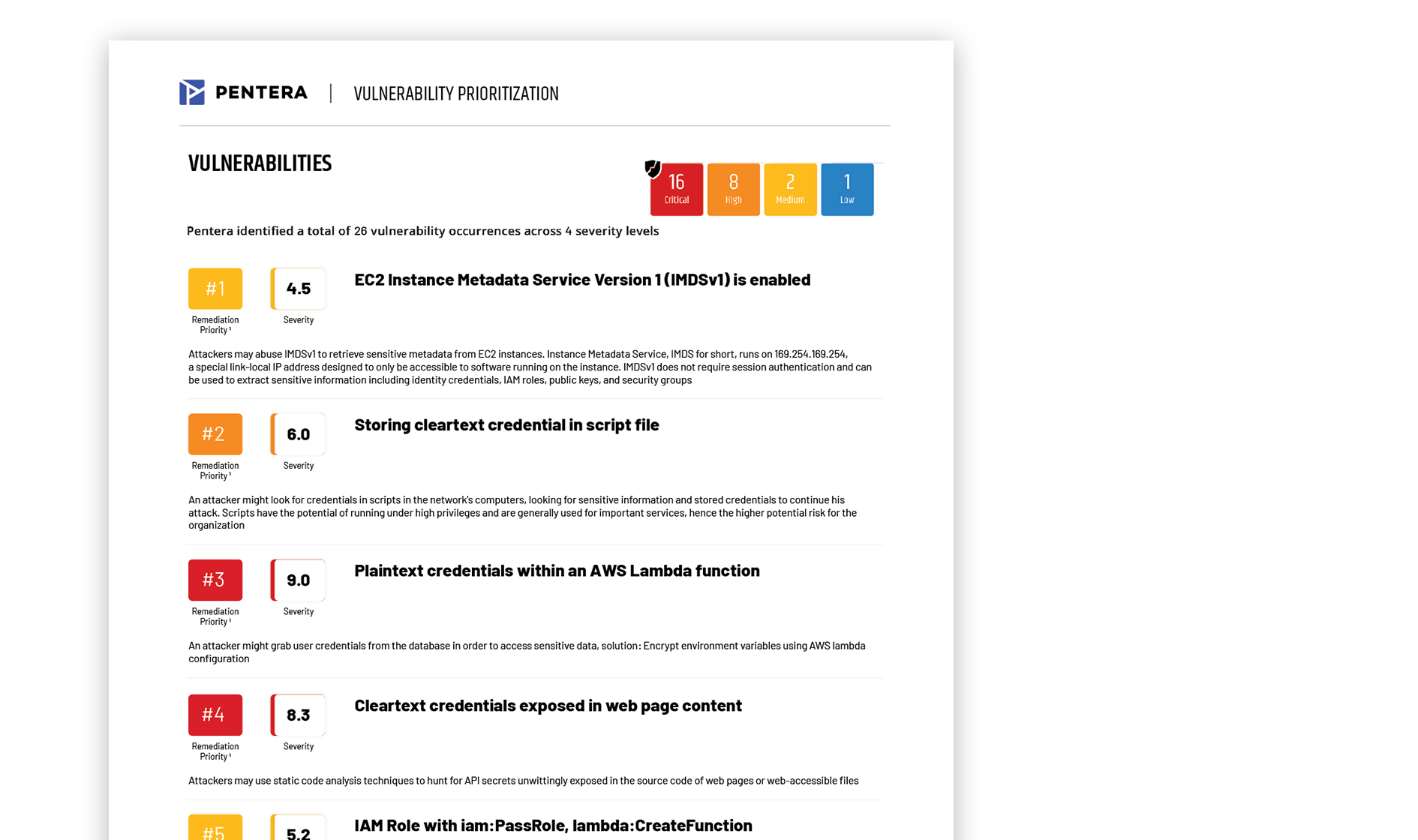
Can Pentera Cloud find any leaked or exposed cloud credentials and secrets? Can it alert when there is a new leak?
Yes, Pentera Cloud is designed to discover and validate credentials and secrets harvested during a test from compromised resources.
Pentera’s Credential Exposure module ingests leaked credential data from external identity exposure data sources, and performs internal and external security validation against these credentials. The leaked credential data is updated regularly, however Pentera does not provide alerts when there is a new leak. The module is not currently integrated with Pentera Cloud.
How is Pentera Cloud licensed?
Pentera Cloud licensing and pricing depends on the number of active workloads in your cloud environment and whether you have it packaged with other Pentera products.
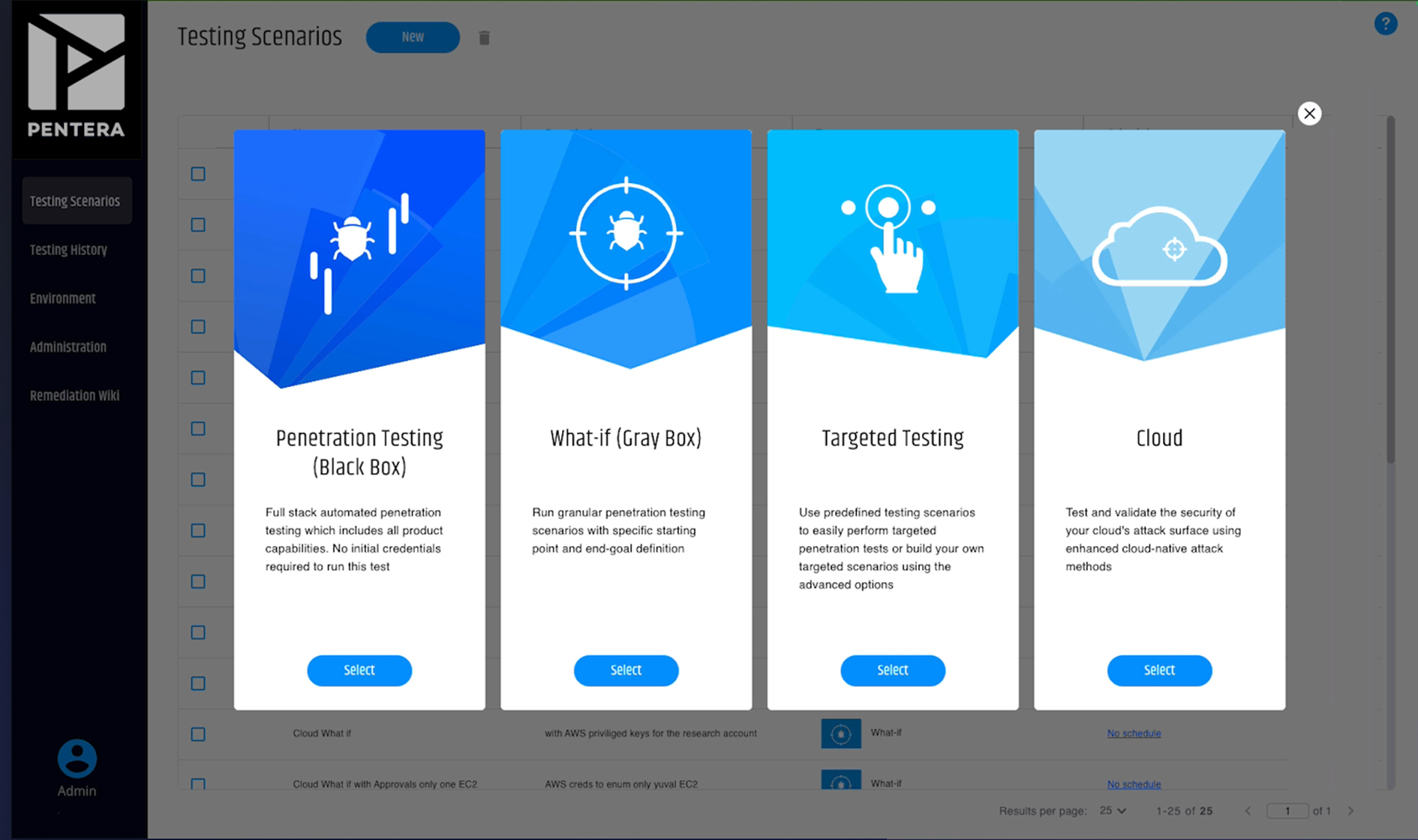
Can Pentera Cloud test more than one subscription (Azure) or account (AWS)?
Yes – Pentera Cloud is available for both AWS and Azure, while GCP is on the roadmap. Multiple accounts can be onboarded and it is possible to scan multiple accounts within the same test.