About Ransomware Resilience
Build resilience against ransomware attacks.
Learn how to prevent, respond to, and recover from ransomware to protect your data and minimize operational downtime.

Ransomware Insider Threats: Understanding the Growing Danger
Understanding the Risks of Ransomware Insider Threats
The trope of the burglar comparison in cybersecurity is more than overused. But when we talk ...

Continuous Ransomware Validation: Why Annual Testing Is No Longer Enough
Ransomware isn’t just a security issue; it’s a business problem that’s grown too big to ignore. What started as floppy-disk attacks back in the 1980s ...

Ransomware Readiness Strategies: How to Protect Your Organization
Ransomware Readiness Strategies: Are You Prepared?
If this question is keeping you up at night, you’re certainly not alone. The threat is tangibly ...

How Susceptible are Your Linux Machines to a Ransomware Attack?
Ransomware targeting Linux machines is becoming increasingly common. While the vast majority of ransomware is still designed to target Windows systems...

Surviving LockBit Lessons from a Ransomware Attack
What Happened During the LockBit Attack?
On April 13, 2023, we were hit hard. The University of Health Sciences and Pharmacy (UHSP) faced a serious a...

Cyber Attack Lessons 2024: Key Takeaways for Security Teams
The State of Cyber Attacks in 2024
Cyber threats have escalated in 2024, forcing security teams to analyze cyber attack lessons from 2024 to improv...
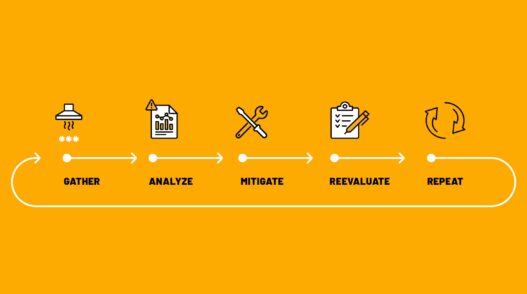
Steps to Mitigate Credential Exposure Risks
Every year, billions of credentials appear online, be it on the dark web, clear web, paste sites, or in data dumps shared by cybercriminals. These c...

Cybersecurity Highlights of 2020
The Greatest Hits of 2020
Who doesn’t love some good old nostalgia? Ok, it’s true, many of us are glad to see the back of 2020. But as we sta...
Begin your security validation journey
Request a demo


